The basics of software security for software programming management
TipsMake.com - Having less security holes means better quality of software and lower cost. Merkow and Raghavan provided professional guidance in building and managing a security software that met the above criteria.
If we do not learn anything from more than 60 years of software development with its security, there will be no coincidence of high quality code. National governments know the quality and security needs to be accurately defined, designed and implemented step by step throughout the software development cycle (SDLC - Software Development Life - Cycle).

Governments are always sure of allowing only new capable software to be used to protect national secrets. However, this view is never revealed to the commercial world and what we lack today is the question of the reliability of a group of applications.
Therefore, this article will emphasize issues and provide solutions to help you avoid repeating mistakes that cause unsecure and unreliable software and systems. We will mention what people want when they have a software and what they really get, the reason for the vulnerabilities, and when you are a manager, what can you do to upgrade your company's software development habits as well as evaluate your successful progress.
What do users expect from software?
Software is really useful for what they can do. People buy software because it can meet their needs to perform some functions. These functions (or features) can be as simple as allowing users to write a letter or can be as complex as calculating the fuel consumption of a journey about to be launched on the moon.
Users also (wrongly) think that the software they buy is written with quality code. When you buy a software package, you often acknowledge that they will work as advertised and you won't think about how well the program will do its job.
The sad truth is that most software still has errors and these errors can threaten to affect the security and safety of any system they are operating on. These errors not only appear on computers we use every day, but also on other devices, such as mobile phones and medical devices and other services such as banks and finance, energy, and telecommunications.
Programmers are taught to write code - they are not taught how to write good code.
Organizations encourage programmers to write more code, rather than good code in the context of cheap code and rapidly developing code that dominate the market.
In particular, Web applications are more likely to be corrupted with certain types of vulnerabilities (eg Cross Site Scripting (XSS)) unless programmers attempt to block them. If the programmer fails to add the output encoding and confirm the appropriate input, this application will easily be attacked by default to XSS.
For a programmer, this software can act as a working target but never check how it works when they have some malicious code or are directly attacked.
Writing software, like driving a car, is a habit. Before someone teaches us how to drive safely, we hardly know the danger of driving and the skills needed to prevent or avoid accidents. Cars often have built-in safety mechanisms, but when driving, we will have to completely use safe driving skills.
How bad is this problem?
In 2008, the vulnerabilities discovered by commercial software increased significantly - by 13.5% compared to 2007. The severity of vulnerabilities also increased with 15.3%. The vulnerabilities of moderate severity have increased by 67.5% and nearly 92% of the holes in 2008 can be exploited remotely.
Of the total number of vulnerabilities discovered in 2008, only 47% of the vulnerabilities could be patched by vendor patches. By the end of 2008, 74% of the disclosed web application vulnerabilities this year did not have a patch to patch them.
Web applications are also of Achilles Heel of Corporate IT Security. Every year, the organization spends millions of dollars on the security of its software structure - a significant part of its annual budget. Software security expenditures focus on detecting the current vulnerabilities in the software being owned by the organization and finding ways to reduce the risks of using them. Rewrite the software, even if it fixes a bug or fundamentally changes the way the software works, as well as affects its annual expenditures. Bad code also adversely affects performance whenever the application or system fails, resulting in a direct or indirect loss of business. Other Web application vulnerabilities also adversely affect brand, reputation, data theft and service rejection issues.
Build your own software security!
Software vulnerabilities appear in the software because together with the specifications, deployment and inspection rounds, the requirements for software security are not concerned and distracted. Software is only secured when it is designed for security - most of the attempts to upgrade security after problems are even more complicated than when they were considered right away. opening development.
To be able to migrate around developing security software requirements, security should be built into the development cycle and start with a management tool supported by Secure Coding Initiative to improve the way Think of what an organization will do and develop software for everyone to use - from home use or sale to someone.
Any initial security code must meet all the steps of a software development cycle. Security programs are safe by design, throughout development and by default. With any initial change, education always plays an important role. Education is the 'foundation stone' for any effective intervention to upgrade software quality. Priority is based on those with experience in developing secure code software; as well as the need to train safety design and code management to help analysts, designers and developers better understand how incomplete, decisive analysis Bad design, and bad code writing actions are responsible for software and system vulnerabilities.
Once knowledge has been disseminated, SDLC attendees will act differently and begin to act as internal monitoring and balancing mechanisms to help capture the problem earlier as well as help reduce development costs. and increase system quality.
Education needs to prepare people with basic knowledge of Web application vulnerabilities, make them familiar with hacking tools, and prepare them with new tools and skills to help them perform their work. I am better.
In the early days of software development, studies have shown that the cost of correcting errors and holes in the design is much lower when these problems are detected and corrected with requirements and stages. design rather than after they start producing software. So, if you integrate security methods with the development cycle as soon as possible, the price of the software will be cheaper.
Security methods are common improvements and any organization can and should accept them with their current environment. There is no direct way to implement these methods - each organization will have to tweak and customize them to suit their development and operating environment. These upgrade methods also add many explanatory and structural tests into the system. Currently, there are many methods to develop remarkable software security, such as Secure Development Lifecycle (SDL) from Microsoft, Touchpoints of Cigital, and a method we will test in this article, called CLASP.
Comprehensive, Lightweight Application Security Process (CLASP) - Lightweight, comprehensive application security process.
The Open Web Application Security Project Team - OWASP - (Open Web Application Security Project) is an open organization created to allow organizations to understand, develop, use and store trusted applications. . One of their more prominent projects is the Convenient, Lightweight Application Security Method - CLASP - (Comprehensive, Lightweight Application Security Process).
CLASP is a set of predefined processes and tools that can be integrated into any software development process. This process is designed for users to be easy to use as well as very effective.
CLASP uses an approach, a record of the activities that organizations should perform. CLASP has a lot of extensions available to users and open source security sources that make these activities more practical and achievable.
Consider CLASP as a source library to avoid rotation when you encounter the need for a new process or new ideas in software security development.
CLASP provides extensive specific information on:
- The concepts behind CLASP to get started
- 7 Best Practices - the best habits - help define CLASP
- High-level security services, serving as a platform
- The main security principles are for software development
- Summary Roles are related to software development
- Activities to complement the development process in order to build more security software
- Technical and instructional maps of CLASP process
- Guide Code to help programmers and editors when they look at the code
You can get a free copy of CLASP in book form or from the OWASP CLASP Wiki.
Implementing good practices for software application security requires a reliable process to guide a programming team in creating and deploying an application that can withstand security attacks. . Within the software deployment project, CLASP Best Practices is the basis of all software development activities related to security. Here are 7 best habits:
Best Practice 1 : Set up recognizable programs
Best Practice 2 : Perform app reviews
Best Practice 3 : Capture security requirements
Best Practice 4 : Implement security development habits
Best Practice 5 : Develop methods for fixing vulnerabilities
Best Practice 6 : Identify and manage
Best Practice 7 : Provide instructions for security operation
Key security concepts and techniques can be alien to your company's software programming team and those involved in application development and deployment. Therefore, it is necessary to disseminate knowledge to relevant people. Identified programs can quickly be deployed, use external expertise, and return by making sure that software security enhancements are implemented effectively. Here are some tips with security identification:
Giving knowledge sessions to all members of a team
Before team members can identify security-related issues, you must make sure they have enough knowledge with such issues. This can be done well with a training program. Everyone in the team should embrace the training introduction to the basic security concepts and security development processes used within the company.
Promote awareness of regional security settings
Everyone on a development project should become familiar with the security requirements of the system, including a basic attack risk pattern. When these data are printed, they need to be distributed and presented to the team members. In addition, you should also try to attract and encourage the opinions of everyone on the team.
Establish accountability for security issues
Traditional accountability in programming organizations is based on calendar and characteristics. Security should be 'treated' like other properties.
Assign a security project commander
A great way to increase security awareness in a development cycle is to appoint a team member to become a security project leader, specifically a dedicated, security-experienced person.
Set reward mode for controlling security issues
Accountability is essential in raising awareness of security, but there is still a more effective way of establishing a bonus mode for those who complete their work in the security area. For example, we can reward someone who has done a good job for a long time - particularly if the result is always associated with this person.
The way of checking and evaluating functions is usually done by an analyst who checks or by QA but can expand the entire SDLC. CLASP provides detailed instructions in evaluating applications:
- Identify, deploy, and implement security tests
- Search for security issues not found by performing a review
- Search for security risks introduced by the operating environment
- Working as a protection mechanism, capturing errors in design, technical testing, and deployment
- Perform security analysis of system requirements and design
- Evaluate as systematic risk in an effective time and cost mode by analyzing requirements and design
- Identification of high-level system risks is evidenced by documentation in both requirements or in secondary data
- Identify inappropriate or inappropriate security requirements
- Evaluate the security impact of non-system requirements
- Performing source level security review
- Search for security holes during deployment
- Research and evaluate the security situation of security solutions
- Evaluate security risks in 3rd party devices
- Determine the effectiveness of a technology
- Confirm the contributions of security sources
- Confirm the existence of the software by the security policies that were previously defined
In addition, it is also important in the scope of application updates and improvements to identify steps to identify, evaluate, and correct vulnerabilities. CLASP instructions can be found for:
- Emphasis on security issues has been reported
- Ensure that the identified security risks during deployment have been reviewed
- Managing security issues reveals the process
- Communicate effectively with external security researchers when identifying security issues in the released software, enabling more effective containment technologies
- Communicating effectively with customers when it is confirmed that the security issues in the software have been released
You cannot manage things you cannot measure. However, making efforts to manage standards effectively can be a difficult task to implement. Nevertheless, the benchmark is an important factor in the overall application security effort. They are important in evaluating the general security situation of your company at the moment, helping to focus your attention on the most serious vulnerabilities, and to indicate the effectiveness - or inefficiency - when you are first. invest in security upgrade.
- Manage security measurement standards
- Assessing the security situation of the development project being implemented
- Mandatory accountability for inappropriate security
Security does not end when an application is completed and deployed in a product environment. The tips and instructions below on security requirements will help users ensure that your organization makes good use of the built-in capabilities.
- Develop a security guide
- Provide stakeholders with documentation of security practices that help ensure product security
- Provide data for using security functions within the product
- Specifies the database security configuration
- Defining the default security configuration for database sources is implemented as part of the implementation
- Identify configurations that are 'recommended' for database sources deployed by a third party
Programming organizations should have a process that they use to perform programming. The most effective way to do that is to build a team of technical processes from the members of the programming team so that they have ownership in the process.
Here are the recommended steps to use to form a technical process team:
Develop a guideline on technical process tasks
Provide documentation of the process team's goals. It would be reasonable for all team members to sign this instruction manual.
Identify a head
The process team should clearly identify a leader who will direct the work and then pass on this orientation to the members. This means that the team will be responsible for all aspects of the technology and activities implemented in conjunction with the previous activities of this new security process framework.
Determine who contributes extra
Just like the process leader, people who are good at spreading should be well-used as those who make the most significant contribution.
Clearly state the rights and responsibilities
Clearly document the rights and responsibilities of each team member.
Create CLASP process instruction documents
Now is the time to make a decision for a process framework. Can a process guide part of CLASP be usable? This decision and guidelines for the results process need to be documented and approved before being translated into deployment documents.
Review and approve before implementation
Set up a test point before deployment. In particular, there will be a major direction of the process to be implemented. The objective of this point is to solicit feedback on whether the framework has been written to replace the goal of the previously placed process. The working team should not continue to carry out project implementation documents until approved by the organization or company.
Record any problem
Problems that occur during the formation of a technical process team should be carefully documented. These issues need to be added to the technical process or process implementation plan - suitable for managing risks.
While SDLC methods - with corresponding security utilities from start to finish - will do the job, it should be clarified that the measurement standard and measurement are essential to be sure. You are on the right track.
Evaluate the success of the security development program
At the end of the article, we will dive into OWASP's two security management software, Open Software Assurance Model (OpenSAMM) and Building Security in Maturity Model software (BSIMM).
OpenSAMM
SAMM is an open framework that helps organizations accurately represent and implement a strategy for adapting and transforming software security with a number of risks faced by organizations. OpenSAMM provides well-defined tutorials and templates for software development and deployment, along with handy tools for self-assessment or planning.
SAMM is intended to help small, medium and large organizations can use it when they use any SDLC. This template can be applied to organizational expansion, for small businesses, or even an individual project. OpenSAMM includes a 96-page PDF file with detailed descriptions of the main activities and corresponding security procedures. You can download this file for free on the OpenSAMM website.
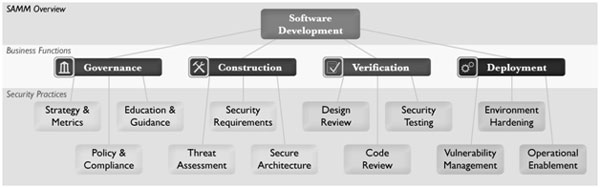
When using OpenSAMM, a company can benefit from:
- Evaluate software security habits in your organization
- Build an application security balancing software in a well-defined iteration
- Prove specific improvements to your security program
- Identify and evaluate security-related activities in your organization
Building Security in Maturity Model (BSIMM)
Building Security in Maturity Model is designed to help you understand, evaluate and plan a software security idea. BSIMM was created in a process of understanding and analyzing data from nine leading software security initiatives and was approved and edited with data from 21 additional software security initiatives.
If used appropriately, properly, BSIMM can help you identify the steps you should take to effectively accomplish your goals.
BSIMM has listed technical processes arranged in four areas:
1. Governance : technical processes that help streamline, manage, and evaluate a software security initiative.
2. Intelligence : Technical processes created from collections are used in implementing software security activities in the organization. These collections include initial security guidelines and organizational chain models.
3. SSDL Touchpoints : Technical processes have a combination of analysis and assurance of several software development components along with processes. All security methods are included in these technical procedures.
4. Deployment : Technical processes have a common between traditional network security and software to protect organizations. Software configuration, protection and environmental issues have a direct impact on software security.
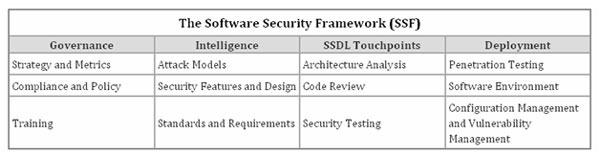
To help you start working with BSIMM, there are many free resources available on the BSIMM website so that users can gather information in MS Excel format and develop a project implementation plan in MS Project. The spreadsheet will help you learn, share the action information section in BSIMM, while the Project file will allow you to copy or click - and - drop actions to be able to sort them by clusters or groups according to your preferences. use. After you have completed your own evaluation, you can build a spider web chart from the results and compare them with other results in a similar or similar industry. BSIMM Begin research tool is a useful tool to be able to start with BSIMM. This research is based on the Web, focusing on 40 of the 110 actions included in the full BSIMM that allow you to have some idea of how your basic software security operations compare to other Methods implemented by other organizations.
Software security for managers: Summary
Sẽ không có sự khác biệt nào về đường lối bạn sử dụng nhằm triển khai một mã bảo mật – khi bạn cố gắng tiến tới các cải tiến, nỗ lực của bạn rất đáng khen ngợi. Trong khi có bất kì một phương pháp nào có thể giúp bạn thực hiện những điều trên, chuẩn đo và các phương pháp đánh giá là thiết yếu giúp đảm bảo rằng bạn đang đi đúng hướng trong việc bảo mật hệ thống và bảo mật phần mềm.