The 10 most devastating viruses in Internet history
The Internet has almost become a paradise for technology enthusiasts, a haven for gamers and a source of entrepreneurial profits. But the global information network is also the playground of the evil hackers.
There is a mind-blowing battle between network security experts and vandal hackers. The pressure on progress, profits leave more holes in the software and that creates more "jobs" for both sides.
With time, the battle of wits is becoming more sophisticated and demanding. Hackers realize that if only exploiting simple technical errors, the "door" to the computer will be much narrower. Therefore, they continually seek to entice and deceive users so they can trap themselves.
The 20-year history of the Internet has its own bold array of imprints. When linked together, only one software gap is exploited, the network of millions of computers shakes and the amount of damage is up to billions of dollars. Here are 10 worms and viruses that cause the worst vandalism in Internet history.
1. Jerusalem (another name: BlackBox)
Discovered in 1987, Jerusalem is one of the first computer viruses in the world and named after the city it was first detected.
Jerusalem virus is famous for its cold and devastating destruction: Clearing data and program files if executed on Friday 13th.

Activating the virus on Friday the 13th became a fashion for a hacker.
This is a virus spread on computers running MS-DOS operating system - the most popular operating system on PC before Windows 95 becomes a real operating system. When infected, all program files (with the extension .EXE or .COM) increase the file size because of the malicious code being inserted, except for the file COMMAND.COM containing the DOS resident script.
Jerusalem then spawned many variants of it, such as the Suriv virus, which deletes data files on machines at certain times of the year (usually lying on a quarter or Friday on the 13th).
By cleverly hiding the algorithm and the "naivety" of users before this kind of attack, Jerusalem's "lineage" became the most popular virus of that time. Their destruction gradually subsides when Windows becomes more popular.
2. Michelangelo
In 1991, thousands of MS-DOS computers stopped working because a virus automatically activated on the sculptor's birthday, Michelangelo - March 6. On this day, the virus will overwrite the entire hard drive and change the Master Boot Record (MBR - to identify and boot the hard drive) so that the hard drive cannot recover by Common tools such as FDisk or Format commands.
After March 6, 1991, about 10-20 thousand computers were reported to be destroyed. However, the actual number is many times higher than that number. The reason is because the information network at this time is not as popular as today.
The harms caused by Michelangelo virus are effective warnings for computer users. A year later, on March 6, 1992, antivirus software sales surged. Many people first ordered this type of software just because they did not want their hard drive to become "high-tech paperweight".
3. Storm Worm
Storm worm is one of the "young" malware on this list because it was "born" in mid-January 2007. Its name was named Storm because it spread through an email titled "230 people died when the storm hit Europe", hitting the computer user by the terrible Kyrill storm. raging on this continent.
Although it was discovered immediately after spreading three days, the Storm worm managed to control 8% of infected computers. All were "tied" to a ghost computer network (botnet), becoming a tool to steal server information, denial of service (DDOS) websites and continuously send emails to other addresses.
Storm was famous for "persistent" attachment to the system and it was difficult to remove. Once it has become a link in the botnet, computers are constantly being updated because DNS techniques are constantly changing. Therefore, the computer is "tied" to the network and difficult to remove completely.
As of September 2007, about 1-10 million computers worldwide are tied to botnets. They are infected from 1 out of 1.2 billion fake emails sent from other infected computers.
4. Sobig
In 2003, Sobig and its variants changed the attack tactics to create a new storm. Instead of attaching an executable file in the .EXE format, Sobig's malicious code is attached to the email with the file seemingly harmless .PIF or .SCR. But just by clicking on the computer immediately infected, Sobig activates its SMTP mail delivery service, retrieves the address in the directory and resumes spreading fake mail.
Fortunately, Sobig and variations are too dependent on websites to run related scripts. So they were removed. However, statistics after the "disaster", Sobig promptly "handled" 500,000 computers worldwide with losses of up to $ 1 billion.
5. MSBlast (Blaster)
In July 2003, Microsoft announced a Windows security vulnerability. Only a month later, this vulnerability was exploited. Deep MSBlast called by the author wrote it has wandered around the global computer with a message to Bill Gates, president of Microsoft software company: "Billy Gates did this. Stop making money and repair the computer calculate "(billy gates why do you make this possible? Stop making money and fix your software !!)
When infected, MSBlast automatically installs a server with the TFTP (Trivial File Transfer Protocol) and downloads the malicious code to this computer.

Self-defined file transfer protocol named TFTP, raging Blaster worm
over 25 million computers running Windows worldwide.
Within a few hours, about 7,000 computers were infected and MSBlast worm was detected. Microsoft worked day and night to release the MSBlast Worm Removal Tool (Windows Blaster Worm Removal Tool) in January 2004. Until then, about 25 million globally reported computers were "stuck" with the MSBlast worm.
Not mentioning the fate of the MSBlast worm, but 19-year-old Jeffrey Lee Parson (USA) had to sit in the cabinet for 18 months and 10 months under local supervision because of spreading the variants of MSBlast to about 50,000 machines. other.
6. Melissa
Deep Melissa has been very successful in destroying her computer for taking advantage of users who "like sex but don't want to spend anything". Many people hastily downloaded the List.DOC file from a discussion group called Usenet just because they heard the file contained a free access code to more than 80 hot porn sites.
The website has not seen it yet but Melissa almost knocked down the Internet at that time by sending email in bulk and continuously. It dives into MS Word version 97 or 2000 text editing software, steals the first 50 addresses in Outlook 97/98 contacts every time you open a text and start automatic spam. . Melissa also automatically inserts notifications from the TV program into the text, deleting important Windows system files.
It is estimated that Melissa worm has caused losses of up to 1 billion USD. The culprit of this deep code was David Smith (New Jersey, USA) who had to "peel off the calendar" for 20 months and pay $ 5,000 in fines.
7. Code Red
July 13, 2001 became "bad Friday" in its own right with the help of the Code Red worm. Taking advantage of a buffer overflow error on IIS servers (Internet Information Server - the feature of Windows that allows users to create a personal web server), Code Red replicates itself in memory until the flag Memory overflow pops up. Just wait, it enters and controls the server.
Code Red and its descendants, Code Red II, are known to be the most greedy worm in Internet history for "sipping" up to $ 200 million a day. Until they were controlled, they left a financial loss of up to $ 2 billion.
8. Nimda
Appearing in the fall of 2001, the worm has the reverse name of the word "Admin" (network administrator / computer) spread by email. On the one hand, they search for email addresses in the .HTML files in the draft folder (cache folder) when surfing the web. On the other hand, they get user email addresses by spoofing with MAPI services (Messaging Application Programing Interface - Application programming communication functions to send and receive messages in Windows).
Then all the related website files in the draft folder are then attached with a Java script so that Nimda can replicate itself. The hard drive is automatically shared without user permission. Guest accounts are limited access to the system because only current users are "openly" with full Administrator rights (system administrator - the highest user level).
In the first week of raging, research firms were able to keep up with the loss statistics that this Nimda worm caused up to 530 million USD. Months later, the report regarding the "crime" behavior continued to be sent.
9. ILOVEYOU (Other names: VBS / LoveLetter or Love Bug Worm)
Without emotional adventure, you will avoid many disasters, including being outside the attack of the second worst virus in Internet history. The defense simply erased a letter titled "ILOVEYOU" from a stranger.
Just click and open the "LOVE-LETTER-FOR-YOU.TXT.vbs" sexy attachment (the love letter for you / me), the code immediately scans the Outlook contacts and sends the letters Replication. The recipient will not be suspicious when the letter with the emotional title is sent from the address of his relative and accidentally becomes the next victim.
This simple joke cost an estimated $ 5.5 to $ 8.7 billion. About 10% of computers connected to the Internet worldwide are recorded to have "stuck" this worm.
Onel A. de Guzman, a virus author from the Philippines, was fortunate enough to get rid of all related charges because there were no provisions in the country to handle computer worm writing and distribution.
Immediately after this, the Philippine government immediately added anti-crime laws online. Vandalism on the Internet can be sentenced to between 6 months and 3 years of imprisonment, with the lowest fine being 100,000 pence (approximately 2,000 USD).
10. Morris Worm (another name: Great Worm)
Have you ever wondered "How big is the Internet world "?
In 1998, Robert Tappan Morris, a student at Cornell University (New York, USA), asked himself the question. After that, he wrote a software with only 99 lines of code to find the answer.
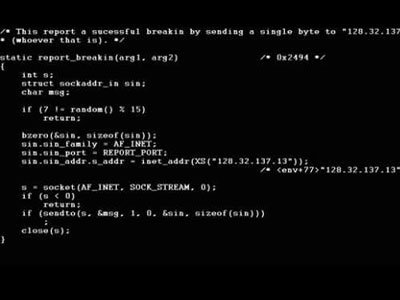
Morris's 99-line code nearly collapsed the Internet server system in the United States
Although Morris's motive was pure, a minor error in the 99 fateful commands when traveling had nearly "turned gold" the Internet server system in operation. Like an alien attack in a fictional film, more than 6,000 UNIX servers across the United States are pushed to an almost overloaded level.
Without the official damage figure caused by the Morris Worm, the estimate is also very wide: between 10 million and 100 million USD. Although the loss of money is not as big as Nimda, ILOVEYOU or Code Red, but Morris Worm is considered the " worst Internet worm / virus in the history " because of the server-targeted destruction, almost collapsing the network. global information.
Hung Hai