New phishing toolkit discovered that makes it easy to create fake Chrome browser windows
This fake window is designed to be extremely lifelike, and also comes with a series of login options familiar with Google, Microsoft, Apple, Twitter or even Steam. The example below shows the DropBox login form, allowing users to sign in with an Apple or Google account.

When you click the Login in Google or App button, a single sign-on (SSO) browser window will be displayed, prompting you to enter your credentials and proceed with your account login.
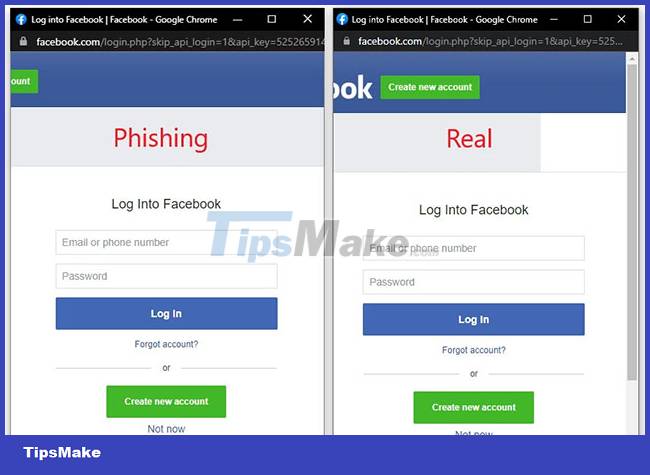
These windows are removed to show only the login form and a URL address bar of the login form.

Although the address bar is disabled in these SSO windows, you can still use the displayed URL to verify that a legitimate google.com domain is being used to log you into the site. The presence of this URL makes the form more trustworthy, and will make you feel comfortable, no doubt, when entering your login information.
In the past, threat actors have attempted to create these masquerade SSO windows using HTML, CSS, and JavaScript. But there's usually something slightly different about the windows, making them look suspicious rather than 'real' as in the case above.
Browser in the Browser Attack
The emergence of these fake browser windows leads to a new form of attack called "Browser in the Browser (BitB)". They use ready-made templates to create fake Chrome pop-ups, but are designed to look like the real thing, including custom URLs and address headers that can be used in phishing attacks.
Basically, BitB attack creates fake browser windows inside real browser windows (browser within browser), thereby helping to improve the persuasion of the phishing activity.
A security researcher with the nickname mr.d0x recently released examples of BitB attack samples (via GitHub). These include fake Chrome windows on both Windows and Mac, with variations in the appearance of dark and light backgrounds.
Malicious actors sometimes simply download templates, edit them to contain the desired URL and title, and then use an iframe to display the login form. Alternatively, it is also possible to add HTML for the login form directly. However, this process will require the hacker to know how to properly align the form using CSS and HTML.
Kuba Gretzky, the creator of the Evilginx phishing toolkit, tested the new method and showed how it works perfectly with the Evilginx platform. This means it can be adapted to steal 2FA keys in phishing attacks.
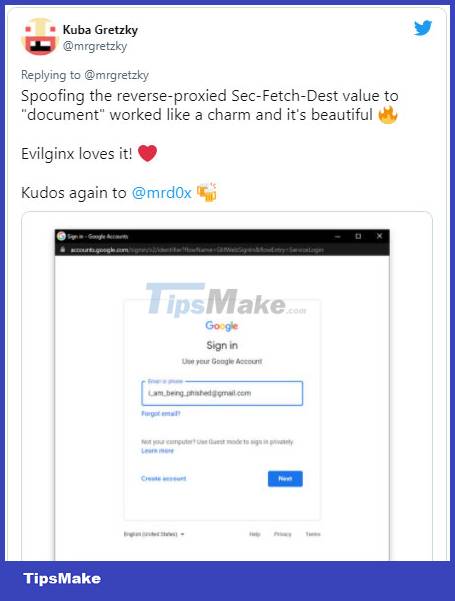
In fact, this is not a scam technique. In 2020, there have been many cases of fake game websites using the above technique to steal Steam login information.
You should read it
- ★ Microsoft Edge is the best browser to prevent phishing
- ★ [Infographic] How to recognize and prevent Phishing attacks
- ★ GitHub is under strong phishing attack, users pay attention to account security
- ★ Learn about the Adversary-in-the-Middle phishing attack method
- ★ What is IPFS Phishing attack? How to avoid?