Many encrypted SSDs can be decoded without a password
Researchers at Redboud University have discovered a vulnerability in some solid-state drives (SSD - Solid State Drive) that can decrypt encrypted hardware without a password.
Carlo Meijer and Bernard van Gastel discovered that they could modify the firmware and use debug tools to change the drive's authentication password. They tested successfully on Crucial and 840 EVO's MX100, MX200, and MX300 SSD drives, Samsung EV3, T3 Portable, and T5 Portable.
Researchers say they can perform reverse engineering on these drives, reprogramming it to authenticate the password despite entering anything. 'In theory, security measures by hardware encryption are said to be equal or better than software. But in fact, we find many drives with weaknesses, allowing data recovery without needing to know the password. '
Windows BitLocker encryption software also automatically switches to hardware encryption if it is available, so it is broken in the same way. Meijer and van Gastel use three techniques to exploit these vulnerabilities.
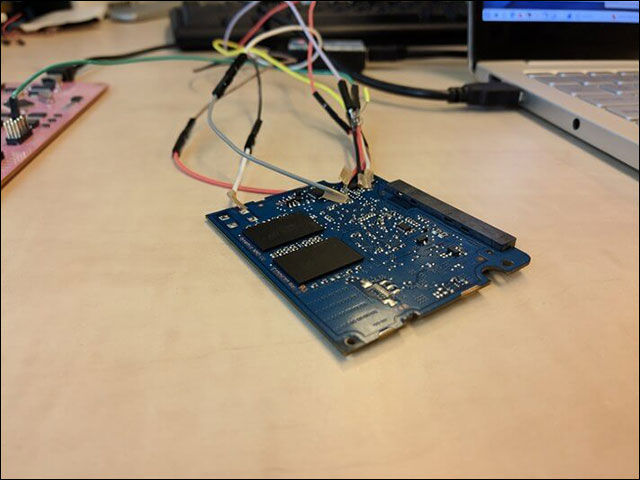
3 techniques for unlocking an SSD are encrypted
On Crucial's MX100, MX200 and 850 EVO, Samsung's T3 Portable, they hooked up to the drive's JTAG debug interface and edited the password. Type in any password to unlock the drive.
Crucial's MX300 also has a JTAG drive but is turned off by default. Instead they flash the drive with a fake firmware to authenticate using a blank password field. For the remaining drives, they reclaim the Data Encryption Key (DEK) with wear-leveling.
'Assuming DEK is stored without protection, this password is set by the user, and replaced that password with the encrypted variant'. 'Due to wear and tear, new variants are stored somewhere in storage chips, old addresses are considered unused. If not overwritten by other activities, DEK's unprotected variant can be recovered. '
Crucial and Samsung have been notified, Crucial has released patches for the firmware on the failed drive, and Samsung has updated the T3 and T5 Portable drives. With EVO drives, they encourage users to use encryption software.
See more:
- 9 best SSDs for gamers
- Review Samsung 850 EVO 500GB - The best removable SSD on the market today
- 7 mistakes easily 'kill' SSDs
You should read it
- ★ Instructions for USB encryption with VeraCrypt
- ★ Scientists have created the world's first unbreakable encryption chip, including quantum computers
- ★ Detecting a Google Drive vulnerability could allow hackers to trick users into installing malware
- ★ Google reinforced Google Drive data protection encryption
- ★ Top 20 best encryption software for Windows