Learn about the BackBox operating system
Any task can succeed or fail, depending on the tools at hand. For security professionals in particular, building the right toolkit can make things exponentially easier. Fortunately, with open source, you have a wide range of applications and environments at your disposal, from simple commands to complex and integrated tools.
However, the problem with a partial approach is that you may miss something that can create or disrupt something, or waste you a lot of time searching for the right tools. for work. Finally, it is always a good idea to consider an operating system specifically for penetration testing (aka pentesting).
In the open source world, the most popular pentesting distribution is Kali Linux. However, this is not the only tool you can use. In fact, there is another version of Linux, specifically aimed at pentesting, called BackBox. BackBox is based on Ubuntu Linux, which also means you have easy access to a host of other outstanding applications besides those already available.
What do you know about BackBox operating system?
- What is BackBox?
- What makes BackBox special?
- Install BackBox
- Use the BackBox
What is BackBox?
BackBox provides a simple way to ensure all security and network device backups are collected fully, stored securely and are available for recovery with just one click when needed. This security and network automation software also offers 1,000 other customized task automation features related to equipment maintenance, as well as dynamic warehouse management and pre-device health checks for over 160 supplier.
When BackBox is connected to all devices on the network, many routine and manual procedure management procedures become automatic or scheduled to help organizations save their time and effort. like saving time, money and resources.
What makes BackBox special?
BackBox includes a special hacking tool kit aimed at pentesting. These testing tools include items such as:
- Web application analysis
- Exploit experiment
- Network analysis
- The test for pressure
- Privilege escalation
- Vulnerability assessment
- Computer forensic analysis
- etc .
Also, one of the most significant differences between Kali Linux and BackBox is the number of tools installed. While Kali Linux offers hundreds of pre-installed tools, BackBox significantly limits that number to about 70. However, BackBox still includes many tools needed to get the job done, such as:
- Ettercap
- Msfconsole
- Wireshark
- ZAP
- Zenmap
- BeEF Browser Exploitation
- Sqlmap
- Driftnet
- Tcpdump
- Cryptcat
- Weevely
- Siege
- Autopsy
BackBox is in development, the latest version (5.3) was released on February 18, 2019. But how to use BackBox? Let's install and find out!
Install BackBox
If you've ever installed a Linux distribution, the BackBox installation is almost the same, with only a slight change. The BackBox is quite similar to any other setting. Download BackBox ISO, burn (burn) ISO to USB, boot from USB and click the Install icon .
The installer will immediately become familiar to anyone who has installed an Ubuntu or Debian version. Just because BackBox is a distribution exclusively for security administrators, doesn't mean starting and running this operating system is a difficult task. In fact, BackBox is an operating system that anyone, with any skill, can install.
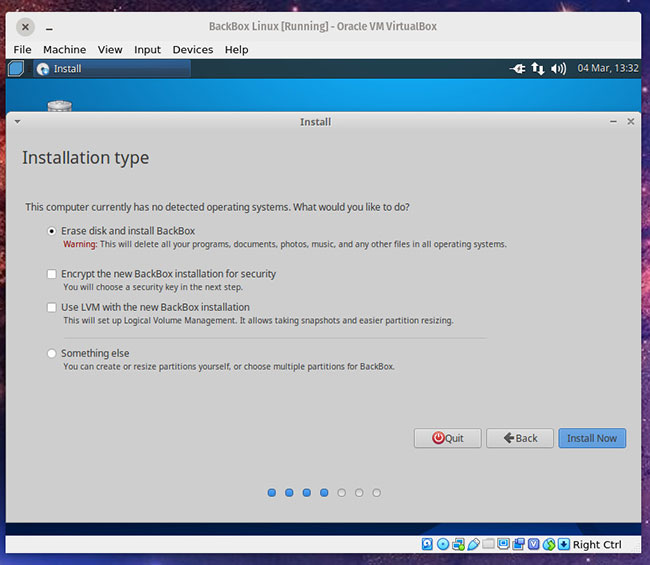
The hardest part of installation is the Installation Type. As you can see, even this step is quite simple.
After installing BackBox, reboot the system, unplug the USB and wait for the login screen to appear. Please log in to the desktop and get ready to continue.

Use the BackBox
Thanks to the Xfce desktop environment, BackBox is easy enough for new Linux users to navigate. Click the menu button in the top left corner to display the menu.

From the desktop menu, click on any favorites (in the left panel) or click on a category to display the relevant tools.

The menu items you might be interested in are:
- Anonymous - allows you to start an anonymous networking session.
- Auditing - the majority of pentesting tools are found here.
- Services - allows you to start or stop services like Apache, Bluetooth, Logkeys, Network, Polipo, SSH and Tor.
Before you run any testing tools, first make sure to update and upgrade BackBox. This can be done via the GUI or the command line. If you choose to use the GUI, click the menu on the desktop, then select System> Software Updater . When the updater completes checking for updates, it will prompt you if a new version is available, or if a restart is needed (after the upgrade).

If you choose manually, open a terminal window and issue the following two commands:
sudo apt-get update sudo apt-get upgrade -y Many of the BackBox pentesting tools require a deep understanding of how they work, so before trying to use any specific tool, make sure you know exactly how to use them. Working with some tools (like Metasploit) is a little easier thanks to BackBox.
To run Metasploit, click the menu button on the desktop and click on msfconsole from favorites (the left panel). When the tool opens for the first time, you will be asked to configure a few options. Just select each of the default options provided by pressing the Enter key on the keyboard when prompted. When you see the Metasploit prompt, you can run commands like:
db_nmap 192.168.0/24 The above command will list all ports detected on the network map 192.168.1.x.

Even challenging tools like Metasploit are made much easier on BackBox than other distributions (in part because you don't have to worry about installing tools). That alone is worth using BackBox.
Although the use of BackBox may not be as popular as Kali Linux, it still deserves attention. For anyone looking to perform pentest on many different environments, BackBox will make this job a lot easier than other operating systems. Try this Linux distribution and see if it will support you while conducting the security check process!
You should read it
- ★ How to check the pressure of a Linux system
- ★ Learn about Parrot Security OS
- ★ The Korean government is going to use the Linux operating system instead of Windows because of the expensive cost
- ★ 10 reasons to switch to Linux right in 2012
- ★ Instructions for installing Linux operating system on Chromebook