Learn about PGP (Pretty Good Privacy)
Pretty Good Privacy (PGP) is a security protocol used by businesses and organizations to encrypt data over the network.
PGP combines both privacy and password authentication for encryption, as well as decrypting all types of files over the network, whether it's email, text files, multimedia, folders or partitions.
It is this flexibility, as well as the power of PGP in preventing unauthorized access to data, making it the most widely used encryption standard worldwide.
What is Pretty Good Privacy (PGP)?
- Pretty Good Privacy's development history
- What is PGP used for?
- How does PGP work?
- A brief example of PGP
- Is PGP secure?
Pretty Good Privacy's development history
Pretty Good Privacy was developed by scientist Phil Zimmerman in 1991. Phil Zimmerman is the one who wants to create an open source encryption platform that can be used by anyone in the world without paying the fees. too big.
The name is inspired by Zimmerman local grocery store, Ralph's Pretty Good Grocery. After a public release in 1993, PGP has been widely used as a standard for encryption.
Zimmerman first releases files for residents in the United States (download via FTP). However, scientist Phil Zimmerman wants anyone to have the opportunity to download these files, no matter where they live. An update was released in 1996, but the US government tried to prevent it from being widely available on the grounds that Zimmerman had no license to leave the US territory as prescribed.
Zimmerman released an update in 1996 through his established company, PGP Inc.
14 years later, Zimmerman sold PGP Inc to security giant Symantec Group. This is also an antivirus software developer currently responsible for updating PGP to protect email communications. Symantec Group has also developed an open source variant - OpenPGP, which is used in conjunction with the licensed version.
What is PGP used for?
PGP is primarily designed to encrypt email traffic. However, PGP can also be used to protect a variety of other text-based communications, including SMS, folders and disk partitions. PGP is also used as a way to secure digital certificates.
PGP works on a number of different standards, the most popular of which is OpenPGP open source standard. OpenPGP is widely used to secure desktop applications such as Outlook of Microsoft and Apple Mail on Macs. There is also a plugin developed by Google that allows using this standard on Chrome browser.
How does PGP work?
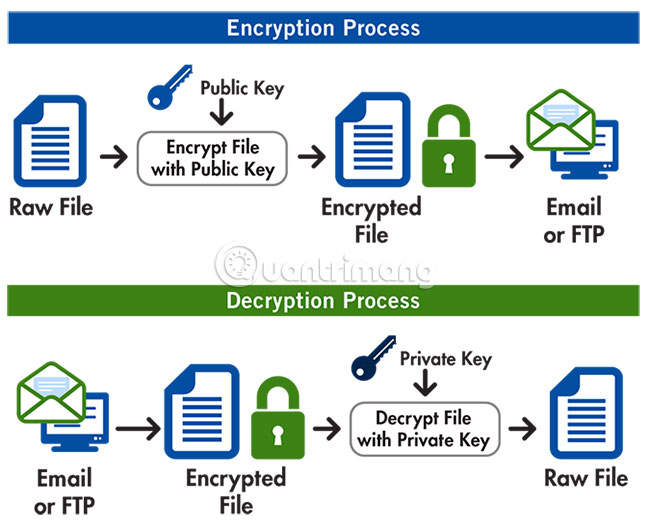
PGP works by placing encrypted layers of security on top of the application's text-based content.
In the case of email clients, PGP secures email content with encryption algorithms, shuffling text in a way that if it is blocked it cannot be read.
With the content of an email being tampered with, the corresponding key needed to 'unlock' the code is also encrypted, usually using the public key provided by RSA or Diffie-Hellman. Then the email is encrypted, along with the corresponding encryption key sent to the recipient.
When this packet arrives at the recipient's email client, the application will use private key to unlock email encryption and then decrypt the content.
A brief example of PGP
There are many software that apply OpenPGP standards. They all have different ways of setting up PGP encryption. One of the tools that works especially well with OpenPGP is Apple Mail.
If you're using a Mac, you can download GPGTools. This application will create and manage public and private keys for you. GPGTools also integrates automatically with Apple Mail.
When the keys are created, you will see the lock icon in the subject line, if you compose a new email in Apple Mail. This means that the email content will be encrypted using the public key you created.
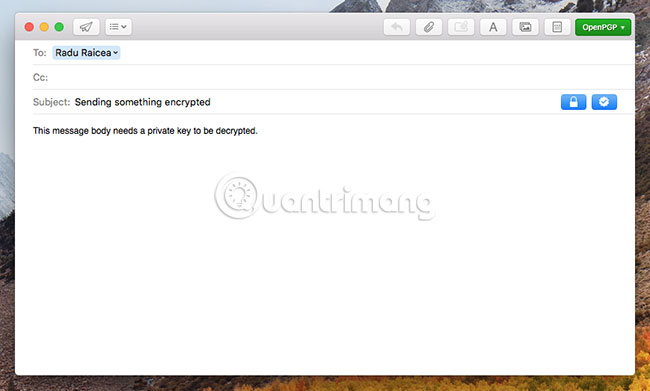
After emailing someone, everything will look like this. The recipient will not be able to view the content of the email until decrypting it using private key.
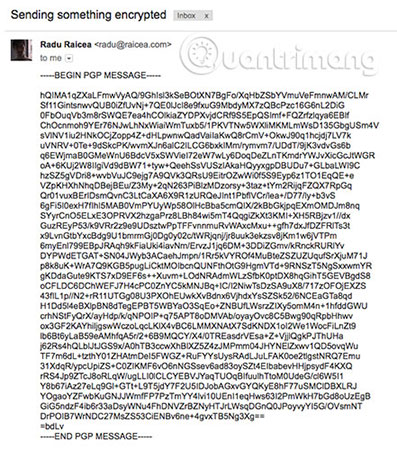
Note that PGP encryption does not encrypt the subject line of the email. Therefore, never put any sensitive information in the subject line.
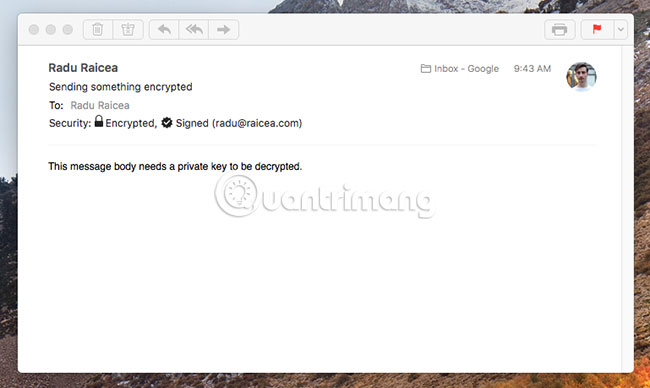
If you are using software that automatically decrypts email with a private key, such as Apple Mail, the content will look like this:
Is PGP secure?
There has been some controversy about PGP's security level. In 2011, researchers discovered that short encryption keys (32-bit or smaller) were not so secure that some people thought they had no security effects at all.
But this does not mean that PGP has serious security issues, but simply uses a long key (larger than 32-bit).
Recently, researchers have discovered an important flaw in PGP (and also the S / MIME encryption protocol) that can allow hackers to read plain text sent in emails.
This issue was discovered by Professor Sebastian Schinzel, a computer security researcher at the University of Münster. He was the one who found the vulnerability (called EFAIL) to abuse the content of HTML emails, such as embedded images, to infiltrate content with the requested URL.
Hackers block emails right from the start by listening to network traffic or more malicious techniques such as entering email accounts, email servers, backup programs, or client computers. After blocking the email, the hacker will change the content and send it to the victim. When the recipient opens the email, the email program decodes the content and sends plain text to the attacker.
EFF wrote in a blog post when it found this vulnerability as follows: 'Our advice, on behalf of researchers, is to immediately disable and / or uninstall automated solution tools. PGP-encoded email code "." Until the vulnerabilities described in this article are understood and fixed, users should arrange to use end-to-end secure channels, such as Signal, instead. Temporarily stop sending and especially read PGP encrypted emails. "
You should read it
- Growth is booming, reaching $ 38 billion but Zoom is facing security and privacy concerns
- Steps to adjust security settings in Microsoft Edge
- What is Privacy Dashboard on Android 12? Why can it be considered a 'breakthrough' in terms of privacy?
- Information security test has the answer P3
- Change the following 7 iOS settings to better Safari security
- Privacy practices on Google Chrome
 What is Maftask?
What is Maftask? Why is Windows slowing down after a period of use?
Why is Windows slowing down after a period of use? What is RFID? What role does RFID play in IoT devices?
What is RFID? What role does RFID play in IoT devices? Security vulnerabilities - basic insights
Security vulnerabilities - basic insights Build your own computer, build your desktop (P4): Install Windows and drivers
Build your own computer, build your desktop (P4): Install Windows and drivers Secedit command: generaterollback in Windows
Secedit command: generaterollback in Windows