Keysight's security expert warns against the new cyber attack process

Mr. Phil Trainor, Director of Security Solutions Division of Keysight Technologies.
In the new information shared, Phil Trainor, director of security solutions division of Keysight Technologies, recently, Keysight's Applied Information and Threats (ATI) team has discovered a pattern. new network attack process. BreakingPoint Attack Campaigns - BreakingPoint's attack processes are a group of attacks named Strikes. When executed in the correct order, these attacks simulate part of the kill chain in practice.
In the latest StrikePack set of BreakingPoint's ATI team, labeled ATI-2020-18, there is a new attack procedure named 'Raccoon September 2020 Campaign' (September Raccoom Process / 2020).
According to information from CyberARK, Raccoon malware has been used in attacks since 2019. Racccon is designed to attack individual users and obtain user-specific information, including machine information. server, browser, and other sensitive information. To help customers recognize and prevent these attacks, Keysight has expanded its security capabilities by adding those attacks to the threat information library.
Detailed description of 'September 2020 Raccoom process'
Analyzing the new attack process, the Keysight Technologies team of experts said, the process simulates closely monitored malicious network communications when the malicious code is called and communicates to the control center. control & control (C&C) when executed. Malicious behavioral simulation was captured and observed in the field by ATI researchers, consisting of 6 attacks as shown in the figure below:
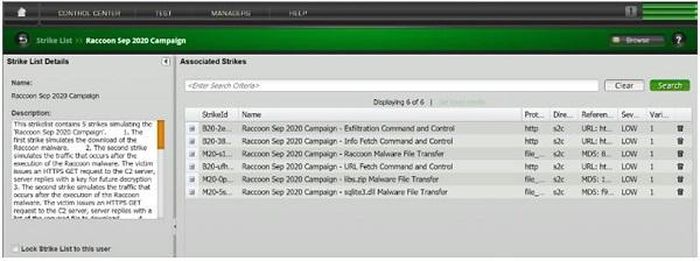
Operation Raccoon September 2020.
The first attack, M20-s1q01 , simulates the actions that are visible on the network if the user clicks on the malicious link and triggers the download of the malicious code. This attack made an HTTP GET request, which resulted in the download of the Raccoon malware over the HTTP transport protocol.
The second attack, B20-38801 , simulates the actions that can be seen on the network if the user opens the malicious executable. The victim sends an HTTP GET request and the attacker responds with an HTTP 200 OK Server Response command, the key decoded data is as follows:

Get the decryption key.
The third attack, B20-ufh01 , simulates an action observed on the network when the user opens the malicious executable. The victim sends an HTTP POST request containing the Base64 encrypted traffic, including bot-id, config_id and other information as shown in the figure below. The attacker responded with an HTTP 200 OK Server Respons response command and a URL link to the file to download.
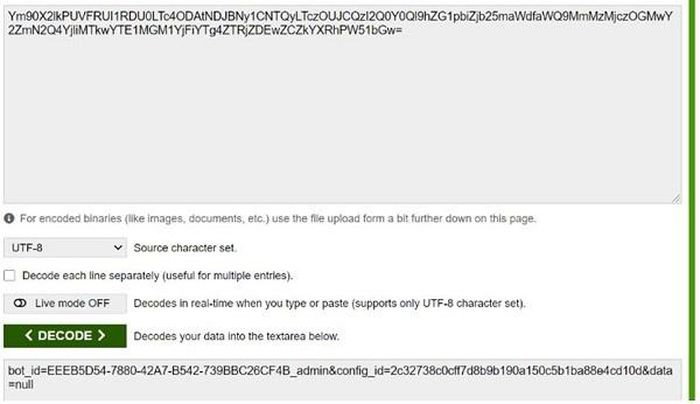
POST request with bot_id and config_id information.
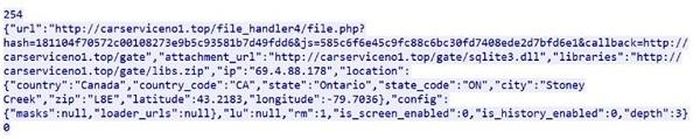
The attacker's response was accompanied by the URL of an additional file to be downloaded.
The fourth and fifth attacks , M20-5sr01 / M20-0pm01 , simulate the actions that would be seen on the network if the user opened the malicious executable. This attack made an HTTP GET request, downloading the sqlite3.dll / libs.zip files over the HTTP transport protocol.
The sixth attack, B20-2e301 , simulates the actions that are visible on the network if the additional files sqlite3.dll and libs.zip are downloaded. The victim sends an HTTP POST request containing a compressed text file containing the hostname, username and sensitive information such as cookies and passwords. The attacker responded with an HTTP 200 OK Server Response response.
The image below is the extracted text file obtained by the Raccoon malware. Here we can see detailed server information and identity files.
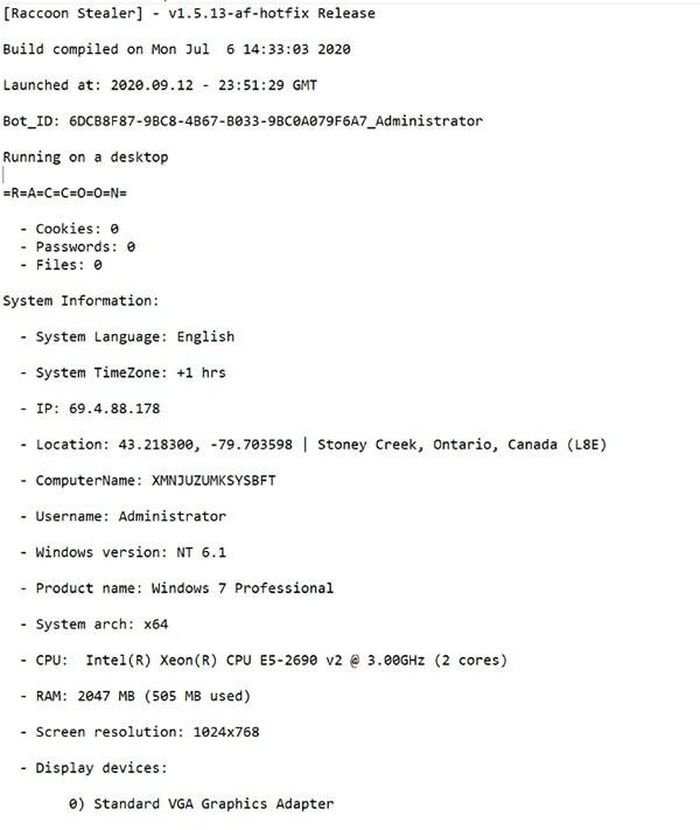
Details of data obtained by the Raccoon malware.
Sign up for a subscription service before being attacked
Research by Keysight experts shows that malicious code can hide in many types of files, including email and document files. Just one click is enough for a malicious infection, file encryption or data extraction to compromise the target system. Especially, when executed, sensitive information will be exploited from the victim's machine.
Also in the new information shared, the Keysight team of experts said, in addition to the technical details observed from this Racoon malware model, there are also many destructive effects that need to be seen from a business point of view. Assets can be stolen and sensitive information can be disclosed can also lead to additional attacks from this malicious object.
According to Keysight, the ATI team is constantly providing the latest, useful content in each version. As new threats emerge, we will continue to stay vigilant while researching and recreating how threats work so that our customers are ready to become aware of them in the future. .
Notably, Keysight's 'Application and Threat Intelligence Subscription' solution updates information about malware every day and every two weeks about application protocols and vulnerabilities. Security flaws for use in Ixia's testing platforms.
Its ATI research center also continually monitors for threats as they appear. BreakingPoint customers can now access continually improved threat attack (APT) attack processes, helping them test security security controls that have been deployed for development. show or prevent these attacks.
Mr. Phil Trainor has over 15 years of experience as a senior cybersecurity engineer for global technology companies and is currently the security solutions director for Keysight Technologies. Prior to assuming this role and before Keysight's acquisition of Ixia, he led Ixia's security business for the APAC region. Besides, he also leads the product orientation activities and business development of security solutions BreakingPoint Security of Ixia.