Protect your computer right before the return of two extremely dangerous ransomware
Ransomare has been in operation for only a few years but it has spread everywhere, from large businesses and financial institutions to hospitals and individual users around the world - to cybercriminals. millions of dollars.
In the past few months, we have witnessed a series of scary ransomware attacks including WannaCry, Petya and LeakerLocker that confuse the internet world, causing many hospitals, telecommunications companies, banks to temporarily shut down door.
Before WannaCry and Petya, encrypted ransomware called Mamba and Locky caused global chaos last year. The bad news is, nowadays, they have come back with new variations that cause greater damage than ever before.
- How to use Kaspersky Anti-Ransomware Tool for Business
- Summary of effective Anti-Ransomware software
- The scary scenario of the spread of GhostCtrl malware on Android devices
Diablo6: New variant of Locky
First appeared in 2016, Locky is one of the largest spread ransomware, infecting organizations worldwide.
By tricking the victim to click on an attachment containing malicious code, Locky will encrypt most file formats on the victim's computer and network, and unlock them until the Bitcoin ransom is paid to those the attacker.
This Ransomware has returned to many variants and is distributed through Necurs and Dridex botnets.
Security researchers have discovered a new malware campaign, Locfaky's new variant of distribution named Diablo6 and targeting computers worldwide. An independent security researcher using the alias Racco42 found out that the new variant of Locky could first encrypt the infected files on the .diablo6 extension.
This variant of ransomware appears on the email containing the Microsoft Word file as an attachment. When opened, a VBS Downloader script will be executed and try to download Locky Diablo6 from a remote server file.
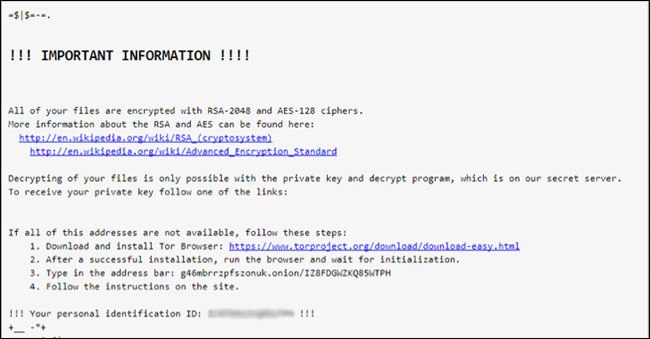
The ransomware will then encrypt the files using the RSA-2048 key (AES CBC 256-bit encryption algorithm) on the infected computer before displaying a message to instruct the victim to download and install. Set Tor browser and access the attacker's website for instructions and payment. The Locky Diablo6 variant requires money from 0.49 Bitcoin (ie more than $ 2,079) from the victim to retrieve the data.
Unfortunately, at the present time, we cannot restore encrypted files with the .Diablo6 extension so users need to be cautious when opening email attachments.
The return of ransomware Mamba
Mamba is another type of ransomware that is equally powerful and dangerous. It has the ability to encrypt the entire hard drive on the infected computer instead of just files that make the system unusable unless paid ransom.
Late last year, Mamba attacked the San Francisco City Transportation Agency (MUNI) network on the weekend of Thanksgiving, causing great delays for trains and forcing authorities to temporarily turn off ticket machines and ticket collection gates at some stations.
Currently, Kaspersky Lab security researchers have discovered a new campaign to distribute the infection of Mamba, targeting networks in countries such as Brazil and Saudi Arabia.
Mamba uses a legitimate open source Windows encryption utility called DiskCryptor to completely block the computer hard drives of targeted organizations. Therefore, there is no way to decrypt the data by the extremely powerful encryption algorithm used by DiskCryptor.
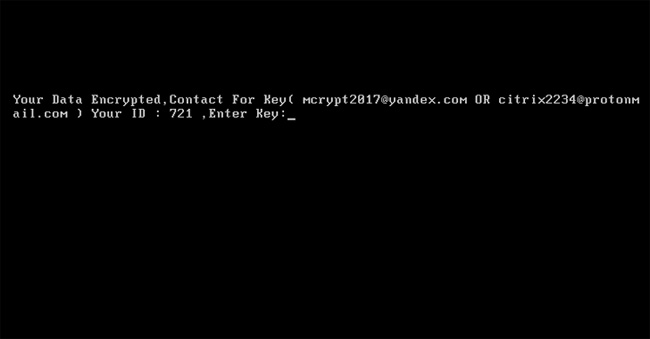
The message displayed on the infected screen indicates that the victim's hard drive has been encrypted and provides two unique email addresses and ID numbers to unlock.
How to protect your computer from ransomware attacks
Ransomware has become one of the biggest threats not only to individuals but also to businesses.
Currently, there are no codecs available to unlock data from Mamba and Locky, so users should follow the precautions below to protect themselves.
- How to get rid of root virus * .OSIRIS - Ransomware Locky?
Be careful with phishing emails : Always be alert to "uninvited" emails and never click on links within those emails unless the source is verified.
Back up data regularly : To closely capture important files and documents, back up your data regularly and store it on your device outside your computer.
Always update your antivirus software and system: This is also one of the most useful ways to protect your computer from ransomware infection.
You should read it
- ★ [Infographic] 7 effective ways to protect businesses from Ransomware
- ★ How to enable Ransomware Protection on Windows
- ★ How to use Acronis Ransomware Protection against ransomware
- ★ Warning: Ransomware is spreading through fake malicious Windows updates
- ★ How to get rid of root virus * .OSIRIS - Ransomware Locky?