Discovered new ransomware on Mac computers
Currently, this type of malicious code is being spread on internet torrents in Russia with the name OSX.ThiefQuest.
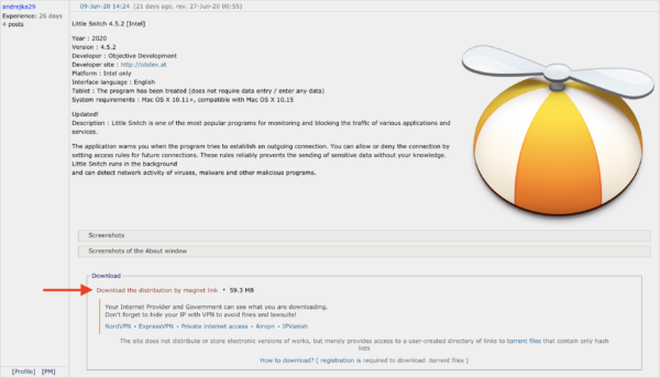
The malware link is posted on RUTracker - a Russian torrent sharing network
To trick users into downloading to the computer, hackers will encode malicious code OSX.ThiefQuest in an impersonation software called Little Snitch - software whose main function is to monitor and manage connections outside the internet. Widely used on MacOS devices around the world.
After deceiving the victim to download and install the software, this malicious code will create on the system files like a normal installer. More sophisticated, this installer also contains a script that is executed after the installation process is complete to make renaming and removing traces to trick users.
Once the infection is triggered by the installer, the malware starts spreading itself around the hard drive, leaving the victim's computer encrypted with important data for the next 3 days. More carefully, this type of malicious code also installs executable files in locations that easily cause users to accidentally activate such as in system startup files or daemon plist files. This action is to create a backup plan in case the previously launched attack program fails.
After the encryption process is complete, a blackmail file is created to show the user how to redeem encrypted data on the device.
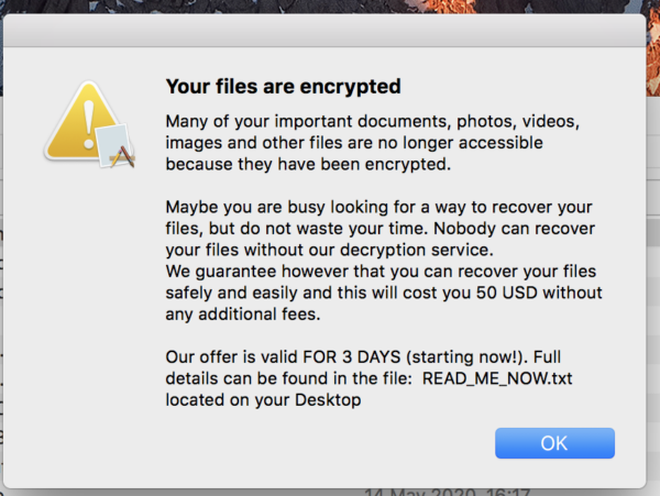
Image file extortion of hackers
The researchers even pointed out that the malware could open a reverse shell for the command and control server to perform remote code execution actions to take control of the computer. the victim.
In addition, OSX.ThiefQuest malware has been equipped with anti-malware techniques. In the case of a user using a malware analyzer or debugger for the computer, this malware usually will not show its full capabilities.
Security experts VSEC recommends that, to avoid being infected by viruses from software downloaded on the computer, users need to identify the source and only download from reputable sites, always read the terms and provisions of applications / software before downloading; periodically check the computer with virus scanning software to promptly handle existing problems.
In addition, VSEC experts recommend that for each important data, you should have at least 2 backups, one of which is always in an external memory that is not directly connected to your computer. anytime. If you have good backups, ransomware is not a threat to you.
Share by
Jessica Tanner
Update 06 July 2020
You should read it
- ★ What is Ransomware Task Force (RTF)?
- ★ Forecast 2021: The world of security will be devastated by ransomware '
- ★ STOP - Ransomware is the most active in the Internet but rarely talked about
- ★ Hackers can use Ransomware to attack and control robots
- ★ Detecting two unusual versions of ransomware, shows that the world of ransomware has become diversified