How to set up an internal RADIUS Server - Part 2
 How to set up an internal RADIUS Server - Part 1
How to set up an internal RADIUS Server - Part 1
Network administration - Small businesses can save costs and increase security by using an access point with an attached RADIUS server. In this article we will show you how to set up a RADIUS server via ZyXEL NWA-3160.
In the first part of this series we introduced the initial IP configuration so that an AP can join the network. In addition, we enabled the internal RADIUS server and entered the user and AP information, created a self-signed digital certificate that we installed on the server and the machines. his calculation. So far, the server-side installation has been completed, and in this section we will configure the APs and PCs with the appropriate settings. Our goal is to provide enterprise-level WPA encryption with 802.1x authentication so that you can have a secure wireless network but reduce the cost and setup time.
Activate WPA / 802.1x on APs
The first step that we need to do in this section is to configure the APs (wireless routers that exist on the network) to use the WPA Enterprise encryption method and set the 802.1x / RADIUS settings. With more advanced APs, such as the NWA-3160, you need to use their profiles. Security and RADIUS settings will be used for each profile. Basic APs and wireless routers will have all the encryption and 802.1x settings on the Wireless or Wireless Security tab, as shown in Figure 1 below.

Figure 1
In the following section, we will explain exactly how to configure the ZyXEL AP, which are the instructions that must be taken when setting up any wireless AP or Router:
- Enable WPA encryption: Select WPA-Enterprise or WPA2-Enterprise (in some cases only written under the name of WPA or WPA2 ), depending on the version supported by the wireless clients. Some APs support complex mode, when both WPA versions can be used simultaneously.
- Choose the algorithm or cipher type: Select TKIP if using WPA , AES if using WPA2 , or both ( Auto ) if using WPA-mixed mode.
- Enter the RADIUS server IP address: This is the IP address of the NWA-3160 hosting its internal RADIUS server.
- Enter the RADIUS server port: If the NWA-3160's internal RADIUS server port does not change from the default, enter port 1812 ; otherwise enter the optional port.
- Enter the shared secret: Enter the password created for the specific AP, defined when the trusted AP is entered in the ZyXEL AP.
To configure WPA-Enterprise for NWA-3160 to use the internal server for authentication, follow the steps below:
- Log in to the web configuration utility, click the Wireless section and select the RADIUS tab.
- For the Primary RADIUS Option , select the Internal button (see Figure 2 below) and click Apply .
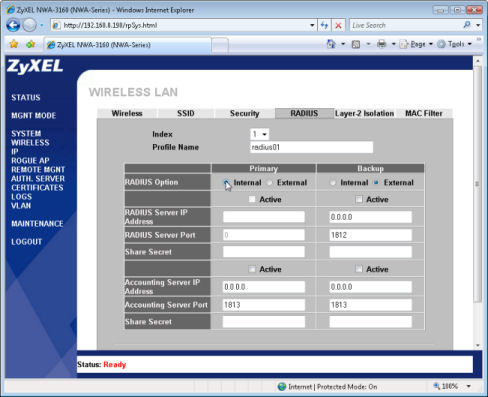
Figure 2
- Select the Security tab
- Select security01 and click Edit .
- With Security Mode , select WPA and click Apply . Now ZyXEL AP will be set up to use its RADIUS server for 802.1x authentication.
If there are many NWA-3160s available online, follow the steps below to use the NWA-3160:
- Log in to the web configuration utility, click the Wireless section and select the RADIUS tab.
- For Primary RADIUS Option , select the External button and check the Active checkbox.
- Enter the IP address of the ZyXEL AP hosting the RADIUS server, enter the server port (default is 1812 ), enter Shared Secret for this particular AP and click Apply . See the example in Figure 3 below.
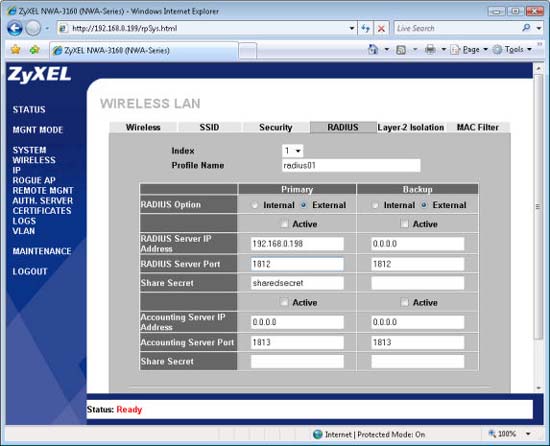
Figure 3
- Select the Security tab
- Select the security01 profile and click Edit .
- With Security Mode , select WPA and click Apply . This AP will be set to use the internal RAIDUS server of another ZyXEL AP.
Configure the wireless client with WPA / 802.1x settings
When all network infrastructure components are set by the appropriate authentication and encryption settings, you can configure the wireless clients. In Windows, this job requires administrators or users to create a profile (or a preferred network entry) for the network, to set 802.1x settings. After this initial configuration, users can connect to the network like any wireless network, enter the name and password of the household to access the network.
Follow these steps to configure the appropriate settings for Windows XP:
- Double-click the wireless network icon in the system tray. If this icon does not exist, you can click Start, Network Connections , right-click the wireless connection and select Properties .
- On the Local Area Connection Status window, click the Properties button.
- On the Local Area Connection Properties window, select the Wireless Networks tab.
- If an entry already exists or has the SSID of the WPA wireless network, select it and click Properties . If no entry exists first, click Add .
- On the Association tab in the Wireless Network Properties window:
- Enter the desired network name or SSID, if you add a new entry.
- Select WPA or WPA2 for the Network Authentication field, based on the version set on the RADIUS server.
- Select TKIP for the Data Encryption field if using WPA or AES if using WPA2 .
- In the Authentication tab (see Figure 4):
- Choose Ensure Protected EAP (PEAP) for EAP Type .
- Uncheck both other checkboxes, except for the RADIUS server set up for any special situations.
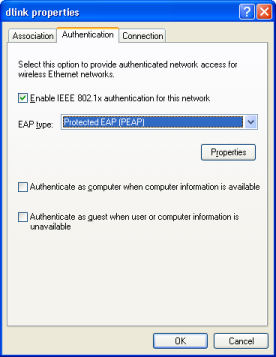
Figure 4
- In the Authentication tab, click the Properties button and follow the steps below on the Protected EAP Properties window (see Figure 5):
- Select the first checkbox, Validate server certificate.
- Uncheck the second checkbox, Connect to these servers.
- Select the CA certificate installed on the AP's internal RADIUS server from the list. If the AP's self-signed certificate has been used, it will start with NWA-3160, then the AP's MAC address.
- Select ' Secured password (EAP-MSCHAP v2) ' for the Select Authentication Method field and click the Configure button. In the dialog that appears, uncheck the option named Automatically use my Windows logon name and password (and domain if any) , and click OK . Figure 5 shows both of these windows.
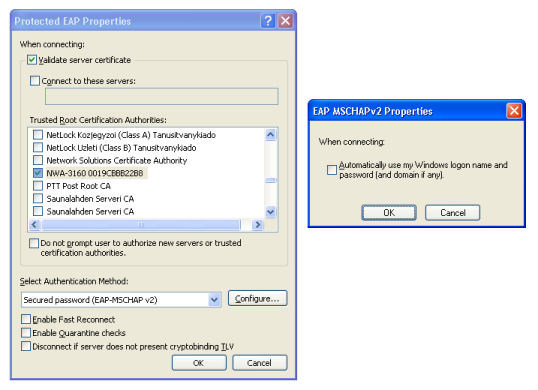
Figure 5
- Click OK on each window to save the network settings.
The network configuration in Windows Vista is almost the same, here are the steps:
- Right-click the network icon in the system tray and select Network and Sharing Center .
- In the Network and Sharing Center window, click the Manage wireless networks link in the left pane.
- If there is a network entry or SSID of a pre-existing WPA wireless network, double-click it and skip step 6. If no entry exists, click Add and proceed with the steps as usual.
- If adding a new entry, click Manually to create a network profile in the window that appears, enter the settings for the network and click Next .
- In the Successfully Added window, click Change connection settings .
- In the Wireless Network Properties window, select the Security tab and follow the steps below:
- Ensure the encryption and security types are set up correctly, based on the version set on the RADIUS server.
- Uncheck or select the desired box to save the username and password when connecting.
- Choose Ensure Protected EAP (PEAP) for network authentication .
- Click the Settings button and on the Protected EAP Properties window, follow these steps:
- Select the first checkbox, Validate server certificate.
- Uncheck the second checkbox, Connect to these servers .
- Select the CA certificate installed on the RADIUS server from the list. If the AP's self-signed certificate has been used, it will start with NWA-3160, then the AP's MAC address.
- Select Secured password (EAP-MSCHAP v2) for the Select Authentication Method field and click the Configure button.
- With the Select Authentication Method field , select Secured password (EAP-MSCHAP v2) and click the Configure button. In the dialog that appears, uncheck the option named Automatically use my Windows logon name and password (and domain if any) , and click OK .
- Click OK on each window to save the network settings.
Connect to WPA / 802.1x wireless network
After configuring the network settings in Windows, select the network from the list of available wireless networks, just like when connecting to other Wi-Fi networks. A message in the lower right corner of Windows will appear for you to enter the login criteria; Click on that message. In the Enter Credentials dialog box that appears, enter the username and password for the account set up on the AP's internal RADIUS server, leave the Logon Domain field blank, and then press Enter .
Conclude
In Part 1 we configured the ZyXEL AP's internal RADIUS server; In this article, I have shown you how to set up APs and clients. If all goes as planned, your computers will be able to connect to the 802.1x network or WPA right now. Although thieves will not be able to crack this encryption, you need to remember to secure the username and password and should change the login credentials regularly to avoid being leaked.