How to close the port / Port 445 on Windows 2000 / XP / 2003 to Windows 10 to prevent ransomware WannaCry
Among the new ports used on Windows 2000, Windows XP and Windows Server 2003 systems, port 445 TCP is used for SMB services transmitted over TCP.
Note: Besides closing port 445, it is also necessary to update Windows patches to prevent hackers from "ripping" Ransomware WannaCry into computers.
SMB (Server Message Block) protocol is used for File sharing purposes on Windows NT / 2000 / XP / 2003 systems. On older Windows NT systems it operates at the high layer of the NetBT protocol (short for: NetBIOS over TCP / IP), using common ports such as ports: 137, 138 (UDP) and 139 (TCP).
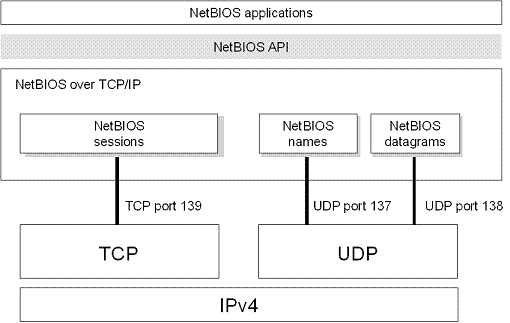
On the following systems: Windows 2000 / XP / 2003, Microsoft supports the ability to directly operate SMB over TCP / IP, no need to go through the support layer of NetBT. Because of this we get the File sharing transaction result done via TCP port 445.
Sharing files over the Internet via NetBIOS protocol is a very basic need, but these are potential dangers when your system connects to LAN, WAN or Internet. All information about your Domain, Workgroup and Computer names can be easily identified via NetBIOS and this port is also the center where the frequency of attacks is highest (as reported by SANS.Org, informed). Details: http://isc.sans.org/port_details.php?port=445).
The real concern of Network Administrators here is that only File sharing transactions should be allowed within the LAN-LAN.

If you are using a Router as an Internet gateway, make sure that you do not allow access from the Network outbound - outbound traffic and access from Inbound to inbound traffic, over TCP ports from 135 -139.
If you are using a firewall, correct the port function, block access via the same TCP ports from 135-139.
If you are using Computer with multiple -multi-homed machine NICs (for example, Computer is on a Network card), please disable NetBIOS operation on each Network card, or dial-up Internet modem -Dial-Up Connection Disables disable by interfering with TCP / IP properties of any Network cards that are not in the LAN-LAN.
How to disable NetBIOS over TCP / IP?
On Windows 2000 / XP / 2003, disable NetBIOS over TCP / IP as follows
Right-click the My Network Places icon on the Desktop and then select Properties . Continue Right-click on the Network Card icon you are interested in ( Local Area Connection ), select Properties .

Next, click on I Internet Protocol (TCP / IP) and Properties .

Now click on Advanced , and select WINS tab.

Here you can enable or disable NetBIOS over TCP / IP.

The changes take effect immediately, no need to restart the system.
At this point, logs of events on your computer will record an event (remember that you should not disable the service named: TCP / IP NetBIOS Helper Service, because log events will not be turned off). You can check whether this service is running or not, by entering the Services.msc command in Run to open the service management panel on the system, if the status bar notification is Started. service operated). See the picture to determine which service is running on the system.

Note: Computers running older operating systems before Windows 2000 will not be able to locate, search or set up file sharing and printing connections to Windows 2000 / XP / 2003 Computer systems when NetBIOS has been disable .
How to disable port 445?
You can easily disable port 445 on your computer. Follow these instructions:
1. Open the Registry -Registry Editor editor
2. At Run use the Regedit.exe command.
3. Find the following key in the Registry:
HKLMSystemCurrentControlSetServicesNetBTParameters

3. In the Window window on the right, select an option named TransportBindName.
4. Double click on the option, then delete the default value, and so the frame containing the value is blank.
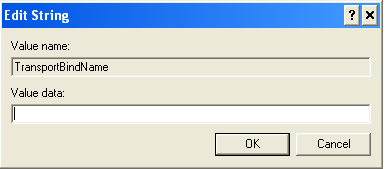
5. Close the Registry editor.
6. Restart Computer.
After starting and logging on to Computer, at Run, enter cmd and enter the following command:
netstat -an
Notice that Computer no longer listens at port 445.

Compare before proceeding to Disable port 445, the image below

How to use port on Client / Server
When does Windows 2000 / XP / 2003 use port 445, and when does it use 139?
For a simple explanation I use the two terms "client" to refer Computer to access network resources such as drives and shared files, followed by "server" Computer with available resources shared by the Client. . And to make it easier to visualize, remember the phrase NetBIOS over TCP / IP, simply NetBT.
If the client has NetBT enabled, it will always try to connect to the server at both port 139 and 445 simultaneously. If it receives a response from port 445, it sends a RST response to port 139, and continues the SMB communication session with only port 445. If it does not receive a response from port 445, it will continue to communicate SMB. only with port 139, if you get feedback from this port. If no response is received from the above ports, the connection intended to initialize will end (failed).
If the client has NetBT disabled, it will always connect to the server at port 445. If the server answers on port 445, the connection will be established and maintained on this port. If no response is received the connection ends. This is the case we mentioned when the server runs old operating systems such as Windows NT 4.0, for example.
If the server has NetBT enabled, it will listen on UDP ports 137, 138, and on TCP ports 139, 445. If NetBT is disabled, the server only listens on TCP port 445.
Ho Viet Ha - Owner Network Information Security Vietnam, Inc.
http://nis.com.vn
Email: networksecurity@Nis.com.vn
You should read it
- ★ All about WannaCry, Ransomware has been confusing for the past few days
- ★ Prevent WannaCry variants by turning off this Windows 10 installation
- ★ How to disable USB ports on Windows, Mac and Linux
- ★ How to update Win 7, update Windows 7 to the latest version
- ★ How to connect printer 2.0 USB port to USB 3.0 port on Windows 10