How secure is Bluetooth?
If you regularly watch the news of network security over the past year, you'll encounter some attacks via Bluetooth. For example, the BlueBorne vulnerability is scary for smartphones using Bluetooth to connect external devices. This question raises the question: How secure is Bluetooth?
Types of Bluetooth attacks
It may seem strange that someone can attack the device via Bluetooth, but when accessories can be connected via Bluetooth, you can access all features via this Bluetooth connection. Hackers can use it to do:
-
Bluejacking is a type of attack against hackers using Bluetooth to send spam messages to people in the Bluetooth activity area.
-
Bluesnarfing is a type of attack against hackers using Bluetooth to gain unauthorized access to personal data and information on the device.
-
Bluebugging , usually done on phones with an outdated Bluetooth interface, allows devices to be paired without user consent, then controlling the phone's features.
Although Bluetooth has errors and it is not completely safe, but you as a user can take many measures to prevent this attack from happening.
How hackers perform attacks via Bluetooth
In order to find ways to stop these attacks, we need to know how hackers do these attacks. To do this, hackers need a device that is playing Bluetooth connectivity. Here's how to make Bluetooth connectivity: a device that plays its 'presence' and allows users to make requests to connect.

There are many security measures built into Bluetooth to prevent others from connecting without permission. If you've ever set up a Bluetooth connection, you'll know that you have to do 'pairing' by telling each device to connect to each other. This prevents people who don't know how to connect with you. Of course, hackers have no method of breaking into Bluetooth if this is enough to stop them.
The problem is that you need to turn on Bluetooth to play a connection to a Bluetooth enabled device, which creates a way for hackers to access the device. Therefore, the solution here is to track what is connected.
Stop playing Bluetooth connectivity
In Undiscoverable mode
You may have seen this option in your device's Bluetooth settings, asking if you want the device to 'be detected'. This makes the Bluetooth device constantly signal its presence so that other gadgets can connect. If a utility cannot find the device, it cannot connect. You only enable this setting when you want to connect your computer or phone to another Bluetooth enabled device.
See also: What to do when the device does not receive a Bluetooth device?
After pairing is complete, you can leave your device undetected, meaning it is hidden from other devices. The accessories you paired can continue to connect to your device even when you are in Undiscoverable mode because they have done 'meeting' and 'secret handshake' so there is no need to search for each other. half. Each device has its own way of becoming 'undiscoverable' so check your manufacturer to see how to do this.
Leaving the device in this mode will make it difficult for hackers to access your Bluetooth. If they have the means to connect to "undiscoverable" devices, they still need you to turn on the Bluetooth and know the device's Bluetooth name.
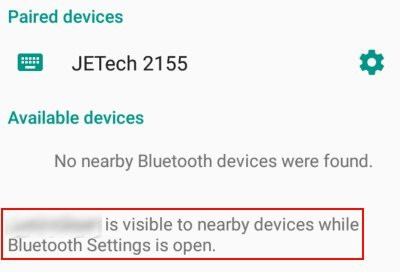
Some devices are designed to automatically control when its Bluetooth name is played, making it safe for you. For example, an Android device only plays its name when you are on the Bluetooth Settings screen to find other devices. When you exit this screen, the phone will stop playing the connection.
Turn off Bluetooth
After using the Bluetooth device, you can completely turn off your Bluetooth adapter. This not only saves battery power for mobile devices, but also makes hackers unable to access the device via Bluetooth. Laptops and smartphones often have a quick way to turn on and turn off Bluetooth, as a button on the device or to turn on / off in the operating system.

How secure is Bluetooth?
Although Bluetooth has vulnerabilities (like other popular wireless communication methods), it's easy to keep yourself safe from hackers. Just keep your device undetected and after pairing off Bluetooth completely when not in use. That way, you can avoid becoming a victim of attacks.
See more:
- 5 things you can do with Bluetooth
- What is Bluetooth 5? What benefits does it have for our lives?
- Fix 3 common errors of Bluetooth connectivity