How does malicious code break into user PC (Part 2)
 How malicious code breaks into a user's PC
How malicious code breaks into a user's PC
The previous article covered in detail the way hackers actively infect malicious code on a user's PC. You can see that these are extremely dangerous attack techniques because users hardly know that they were attacked .
But that is not the only method of attack by hackers, they also have a different method that looks less dangerous but unfortunately the reality doesn't know anything at all. It is an attack method that requires user intervention. The limitation of this method is that the success rate is not as high as the proactive attack method.
The attack method requires user intervention also called 'social engineering' method. With this attack method, hackers can also attack users who have knowledge of malicious code and are extremely careful.
The term 'social engineering' is defined by the world security as 'confidence trick' - where users are tricked into doing certain actions that they are unaware of and also do not want to make.
The following will detail some of the 'social engineering' attacks currently being used quite commonly in hackers.
Clickjacking
In accordance with the definition of global security, 'clickjacking' is a user's attack technique of 'kidnapping clicks' when they operate on a web page displayed in a browser background. This attack technique is also known by the name 'site kidnapping' (Hijacking webpage).
Specifically, hackers will hijack a web site and then attach an invisible layer. This invisible layer can cover the entire web page or only occupy a very small area but always moves and stays just below the user's mouse cursor.
Thus, when users click on any point on the site, it also means they clicked to agree to activate the hackers' malicious code. Usually attack code that hackers attach will lead users to access malicious websites to help hackers actively attack malicious code on their PC as described in the previous article.
Malicious file sharing P2P
File sharing via peer-to-peer (P2P - Peer-to-Peer) is currently a popular method of sharing digital content - both legal and illegal content such as infringing software copyright or movies. And this is also a way to help hackers break into the user's PC.
Specifically, hackers will launch their malicious content on a peer-to-peer network. It may be a pirated application, a movie or music album that is very popular . If the user accidentally downloaded these files, the possibility of their PC being malicious is one thing. inevitable.
Conducting a search on the Internet, we can find a lot of guidelines on creating malicious content to bounce on peer-to-peer sharing that users can hardly distinguish and comfortably download without doubt at all.
Malicious ads
Perhaps this is one of the techniques that hackers are focusing on today, because they want to mimic similar successes that the online advertising industry has recently made.
The previous article presented how hackers take advantage of legitimate advertising systems to spread their malicious ads. In this section, we will see hackers directly advertising malicious links or their malicious code to the users.
First try doing a search on one of the world's leading search engines with keywords related to free download of a newly released game or software.
On the search results page, in addition to legitimate information links, there are also spoof advertising sponsorships that are provided free of charge to users of the said game or software version. In fact, it is a link that leads to malicious web sites that spread malicious code.
Advertisers have also recognized this type of attack and have implemented many preventive measures but it seems that they have not achieved much success because of the huge amount of advertising launched. Therefore, the opportunity to let malicious ads still occur regularly.
Fake security warnings
Another variation of malicious advertising is building a website that advertises for a fake service or product. Web sites like this often use the browser's Javascript processing capabilities to pop out a window with an almost identical design to the operating system's message.
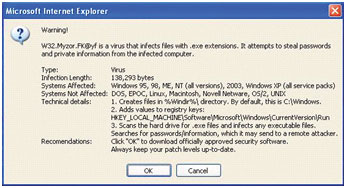
As shown in the picture below is a pop-up ad warning that the user's PC has been infected with malicious code and requires them to click on the link to download the system cleaning software. In fact, these warnings are fake. The purpose of hackers is to trick users into downloading their fake security software to clean up the notifications. Malicious code cannot be found but on the contrary, there is a new malicious code.
Blog Spam
Today blogs have also become a means for hackers to trick users into doing dynamic things that they don't want at all. Official blogs are often covered with URL links that lead to a malicious website.
This form of attack is a complete combination of 'social engineering' and malicious code that attacks browser security errors. The ultimate goal is to hack malicious code onto a user's PC.
The place where hackers often use to launch the most malicious link is the part that allows users to 'comment' on the blog owner's post. These comment benefits are often written with attractive leads to entice users to click on the associated link.
Other attack methods
Not only limited to the above attack methods, hackers also have many other methods to attack users. A form of attack is also worth mentioning here is the method of distributing links or file two by email.
But no matter which attack method to use, the goal of their end is how to make malicious code available to the user's PC. The user's PC then becomes a tool to help hackers continue to attack other users.
You should read it
- ★ Warning: The new Facebook virus, a malicious code that is spreading rapidly through Messenger
- ★ Detecting a Chrome extension infected with malicious code, stealing the password and the user's e-wallet key
- ★ Discovered a new line of malicious Android code that steals user data on the electronic application market
- ★ Warning: New malicious code is infecting about 500,000 router devices
- ★ 14 games on the App Store contain malicious code, iPhone users be careful