FBI Begins Investigation of a Serious Internal Cybersecurity Incident
The US Federal Bureau of Investigation (FBI) is said to be conducting a comprehensive investigation into all malicious cyber activity taking place on the agency's internal network. Federal law enforcement said it prevented an "individual incident" from being assessed as serious, and is working to explore its overall scope and impact.
" This was an isolated incident that was prevented. Because of the ongoing investigation, we do not have any further comment to provide at this time," the FBI representative said in a statement. solstice.
According to initial reports, this was essentially a hack involving the FBI New York Field Office's computer system, which is used to investigate matters related to child sexual abuse.
Earlier in November 2021, the FBI's email server was also hacked and abused by hackers to distribute spam emails impersonating the agency's own reports.
After the attack, malicious actors sent out tens of thousands of spam messages impersonating the FBI from the email address eims@ic.fbi.gov and in batches. This is a legitimate email address associated with the FBI's Law Enforcement Enterprise Portal (LEEP).
Preliminary investigation results show that these emails have reached at least 100,000 mailboxes. But according to SpamHaus, the nonprofit organization that tracks spam, this is a very conservative estimate because the actual campaign "has the potential to be much larger."
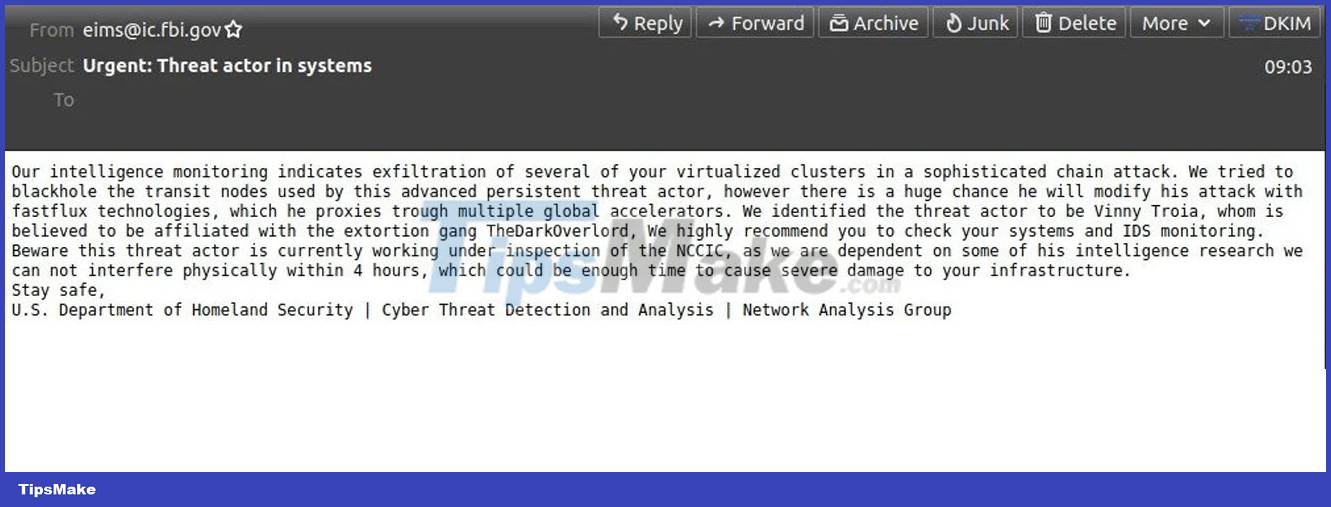
The hack is believed to have stemmed from a temporary software misconfiguration that allowed malicious actors to abuse LEEP to send spoofed emails. LEEP is the FBI's IT infrastructure used to communicate with state and local law enforcement partners across the United States.
However, although the illegal email originates from a server operated by the FBI, that server is dedicated to pushing notifications to LEEP and is not part of the FBI's public email service. No malicious actor can access or compromise any data on the FBI's network.