Data breach analysis with top 10 computer forensic tools
For many years, computer forensics has emerged as an especially important aspect in the field of computer science in general and high-tech investigation in particular. This is a high-tech investigation science based on data stored on computer devices such as hard drives, CD drives, or internet data. Computer forensics includes tasks such as detecting, protecting and analyzing information stored, transmitted or created by a computer or computer network, in order to make reasonable inferences to find cause, as well as explain phenomena in the investigation process. In other words, computer forensics help create favorable conditions for investigating Internet-related crimes. Unlike before, the influence of computers has expanded to all devices related to digital data, so computer forensics help investigate criminals using digital data to find out. those who are behind a specific offense. Those who do this work require extensive experience and knowledge about computer science, networking, and security.

- Endpoint Detection and Response threats, an emerging security technology
To serve this important area, developers have created a lot of highly effective computer forensic tools, helping security experts simplify the process of investigating data-related violations. number. The criteria for choosing the best computer forensic tool will usually be assessed by investigating agencies based on a variety of factors including the budget, features and team of existing experts that can be done. master this tool. Below is a list of the top 10 computer forensic tools that are trusted by many digital security agencies, please refer to the following.
Top computer forensic tools
- Digital Forensics Framework
- Open Computer Forensics Architecture
- X-Ways Forensics
- Registry Recon
- EnCase
- The Sleuth Kit
- Volatility
- Llibforensics
- The Coroner's Toolkit
- Bulk Extractor
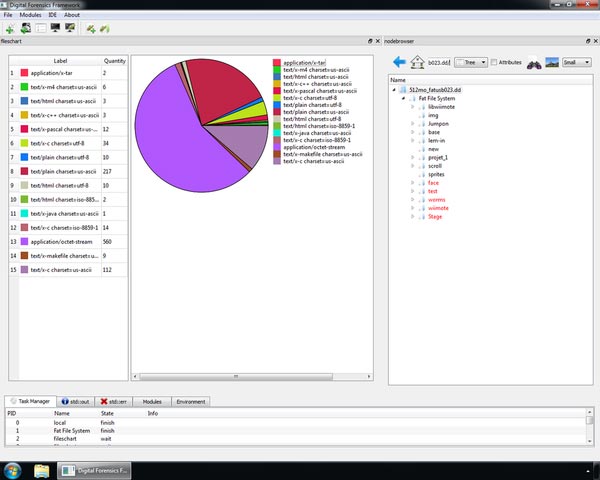
Digital Forensics Framework
Digital Forensics Framework is an open source computer legal tool that satisfies the criteria of GPL License. It is often used by experienced computer forensic experts without any problems. In addition, this tool can be used for a digital chain of custody, to access devices remotely or locally, on Windows or Linux OS, recover files that are hide or be deleted, quickly search for metadata files and many other complex tasks.
- Fileless malware - Achilles heel of traditional antivirus software
Open Computer Forensics Architecture
Developed by the Dutch National Police Agency, Open Computer Forensics Architecture (OCFA) is a computer forensic framework designed in modular form. The main objective of this tool is to automate the digital forensic process to speed up the investigation process and at the same time allow investigators to apply direct access to captured data. through the search interface and extremely easy to use browser.
X-Ways Forensics
X-Way Forensics is an advanced working environment for computer forensic assessors. It can run on most popular Windows versions such as XP, 2003, Vista, 2008/7/8, 8.1, 2012/10 *, 32 Bit / 64 Bit, standards, PE / FE. Of all the tools mentioned above, X-Way Forensics is considered to have the highest actual use efficiency, and often gives faster processing speed in tasks such as searching for deleted files, statistics search visits, and also provides many advanced features that many other tools do not have. In addition, this tool is also said to be more reliable, while saving costs during the investigation process because it does not require any complex database or hardware requirements. X-Way Forensics is completely portable and can run on a compact USB stick in any specific Windows system.

- 8 best storage management and monitoring software
Registry Recon
Registry Recon, developed by Arsenal Recon, is a powerful computer forensic tool commonly used to extract, restore and analyze registry data from Windows systems. This product is named after a French word 'reconnaissance' meaning 'recognizing and recognizing' - a concept in the military related to exploration of enemy territory. to collect tactical information.
EnCase
EnCase®, developed by the well-known software company OpenText, is evaluated as a gold standard tool for forensic security. This multi-purpose computer forensic platform can provide extensive visibility of information on all end points (endpoint) in some areas of the digital forensic process. In addition, EnCase can quickly 'excavate' the evidence and potential data from a variety of devices, and also generate corresponding evidence-based reports. Over the years, EnCase has maintained its reputation as the gold standard when it comes to computer forensic tools used in high-tech crime investigations, and at the same time voted as a medical forensic solution. Best Computer for 8 consecutive years (Best Computer Forensic Solution).

- 7 most popular email security protocols today
The Sleuth Kit
Sleuth Kit® is a UNIX and Windows-based security tool, which helps analyze computer forensics in depth. The Sleuth Kit® is a set of command line tools and the C library that allows you to analyze disk images and restore the file system from these disk images themselves. In fact, Sleuth Kit® is often used in Autopsy and performs in-depth analysis for many file systems.
Volatility
Volatility is the tool used to respond to incidents and analyze malware on the memory forensics framework. Using this tool, you can extract information from running processes, network sockets, DLLs and even hive registry. In addition, Volatility also supports extracting information from Windows crash files and hibernation files. This software is available for free under the GPL license.
Llibforensics
Libforensics is an official library for the development of digital forensic applications. It is developed in Python and comes with various demo tools to extract information from various types of evidence.
- The rise of Botnet IoT and how to protect smart devices
The Coroner's Toolkit
The Coroner's Toolkit or TCT is also a highly regarded digital forensic analysis tool, running on a number of Unix-related operating systems. The Coroner's Toolkit can be used to support computer disaster analysis and data recovery. Essentially, this is an open source set of many forensic tools that allow security professionals to perform post-infringement analysis on UNIX systems.
Bulk Extractor
Bulk Extractor is also one of the most important and commonly used digital forensic tools in the world. It allows to scan the disk image, file or folder of the file to extract useful information for the investigation process. During this process, Bulk Extractor will ignore the file system structure, so it gives faster speed than most other similar tools available on the market. In fact, Bulk Extractor is often used by intelligence agencies and law enforcement in dealing with cybercrime issues.
The above is a list of the most widely used top computer forensic tools in the world. Hope the information in the post is useful to you!
 How to detect fake microSD card
How to detect fake microSD card 5 mobile security risks you need to avoid
5 mobile security risks you need to avoid 5 tips to prevent SIM swapping
5 tips to prevent SIM swapping 5 ways hackers 'beat' fingerprint scanner
5 ways hackers 'beat' fingerprint scanner Is the phone 'brick' safer than Smartphone?
Is the phone 'brick' safer than Smartphone? Review VPN Surfshark
Review VPN Surfshark