Detection of new utility backdoor leaves many Linux distributions vulnerable to attacks
Are you a Linux user? If so, you'll want to be aware of a security issue affecting many of the most popular Linux distributions, like Arch, Debian, Fedora, etc.
Backdoor XZ Utils is a serious problem affecting millions of Linux systems, and here's how you can keep your hardware safe.
What is Backdoor XZ Utils?

XZ Utils is an open source file compression and decompression utility suite widely deployed on Linux systems, similar to ZIP. Before the discovery of the backdoor, this utility had a good reputation for effectiveness in the Linux community.
The backdoor in XZ has attracted a lot of attention because of the popularity of the tool and the way attackers penetrate the open source ecosystem.
The backdoor attack appears to be a long-term battle, with attackers taking years to execute. The attacker, using the name "Jia Tan" but whose real identity is unknown, approached XZ's original developer, Lasse Collin, who was behind on software updates. According to Rob Mensching, Collin, for health reasons, eventually gave up maintenance to the attacker.
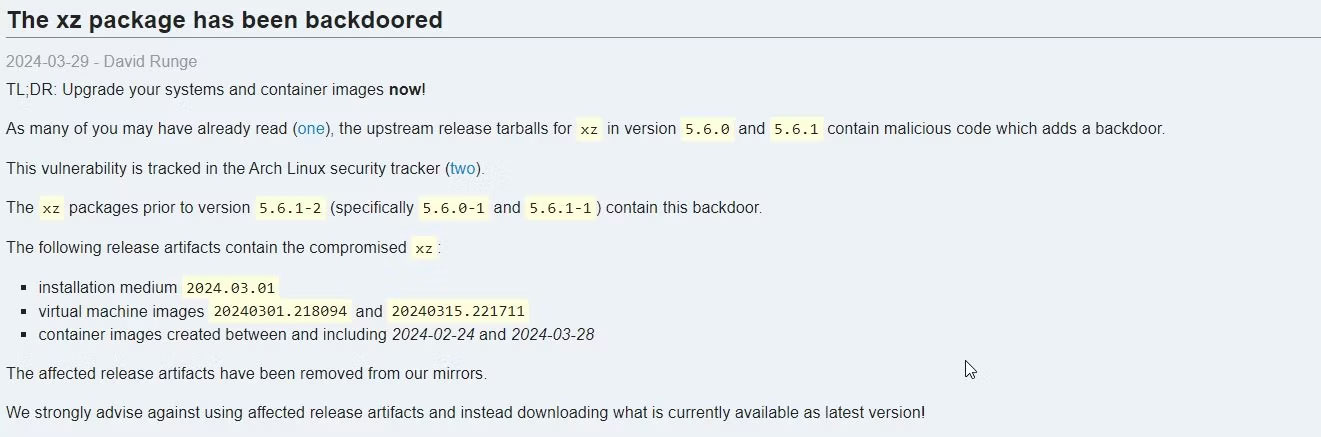
The suspected attacker then inserted a backdoor to connect to SSH, which is widely used on Linux systems for remote access. This may have gone unnoticed until Microsoft developer Andres Freund noticed that SSH was performing worse than it should. The problem originates from versions 5.6.0 and 5.6.1.
Backdoors allow attackers to remotely take control of systems, and with the popularity of XZ and SSH, this could lead to a large-scale attack. After discovering the XZ backdoor, GitHub terminated the main developer's account and the project's homepage also disappeared.
The attacker's apparent success in covering his tracks and the sophistication of his take on the role of an open source developer has led to speculation by security researchers that the backdoor may have been created by a nation-state. as caused by Russia or China, although according to Wired, there is still no definitive evidence.
Which Linux distributions are affected by the XZ Utils backdoor?
Backdoor XZ is primarily aimed at Red Hat and Debian/Ubuntu distributions, as these are the most widely deployed distributions in enterprises. However, distributions that include newer software, such as Arch Linux, Gentoo, Fedora, and the Testing and Unstable variants of Debian, are most affected because they are more likely to include corrupted versions. XZ influence.
Since enterprise Linux deployments tend to favor stable distributions, they appear to be unaffected for now. Debian said the Stable version, available for download from its website by default, is not affected. Red Hat Enterprise Linux and Ubuntu also appear to be unaffected.
How to protect Linux computers from XZ Utils backdoor
The best way to protect yourself in the short term, regardless of which distribution you use, is to keep it updated through your package manager's update utility. Upon discovering the XZ backdoor, Linux distributions quickly took action, releasing system updates to downgrade the version of XZ Utils installed on the system if necessary. Advanced distributions like Arch also urge users to update as soon as possible.
The attack raises worrying questions about the governance of open source projects. Like many other open source projects, XX Utils is a widely used software, maintained by a non-profit developer. A similar issue led to the Heartbleed bug affecting OpenSSH in 2014.

Projects like these are a component of most Linux distributions, and such open source projects are also common in commercial software. If you check the "About" section of many popular software programs, like Spotify or Google Chrome, you'll see that they also use many open source components internally. XZ Utils is included in Chrome.
Developers use these tools because they make their work much easier (they don't have to write every part of the program from scratch).
Going forward, users and companies will have to reassess their relationship with the open source software they rely on. This could range from closer scrutiny of open source developers as well as finding ways to compensate developers, as Rob Mensching suggests.
It's almost certain that there will be more scrutiny of open source development in the wake of this attack.