Bad guys can steal data by freezing RAM sticks with liquid nitrogen
RAM (Random Acesss Memory) is a temporary data storage of the device. The information stored on RAM will completely disappear if the device suddenly loses power.
However, with the cold boot attack technique, one can separate data from a RAM stick after it is turned off. This technique is an illegal hacking activity, used in forensic science, data recovery.
The cold boot attack technique is applied on DRAM. When a power failure, this type of RAM will not lose data immediately but will discharge slowly over time.

Theoretically, the discharge time of a DRAM bar is inversely proportional to the temperature. This means the colder the RAM is, the longer it will discharge.
At room temperature, DRAM takes only a few milliseconds to discharge. But if the temperature is below -50 degrees Celsius, this time can last up to tens of seconds. This amount of time is enough for engineers to remove the DRAM stick from the motherboard and place it on another computer. The data on it will be read through a type of software that can store this data on the hard drive.
One of the cooling methods people often use on microprocessors is liquid nitrogen.
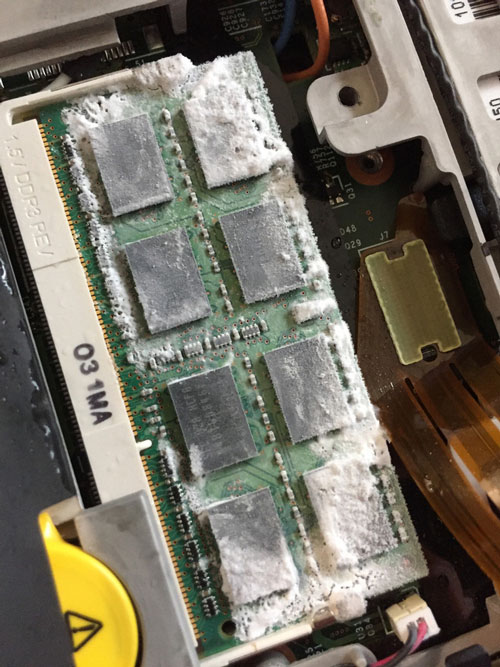
This technique can also be used to attack mobile devices. Usually mobile phones do not have a reset button, so in order to catch the reset system to enable cold start, we have to disconnect the phone battery. The phone then connects to the user's computer via USB and is flashed by an operating system that can "dump" data from RAM, and then store it on memory.

So to deal with cold boot attack technique, what methods do we have?
- Buy computers with soldered RAM sticks to the motherboard. This gives the attacker an opportunity to remove them from the machine.
- Encrypt the entire memory, but this requires changes from the operating system, software and hardware.
- "SEOM", or Secure Erasure Of Memory - forces the BIOS to clear all memory when the computer is not being used.

- 10 operating systems for security research preferred by hackers
- Viettel, VinaPhone, VNPT, Mobifone, FPT . block websites containing videos and 18+ images on computers and phones?
 Apple released smart cases for iPhone 11, iPhone 11 Pro and iPhone 11 Pro Max
Apple released smart cases for iPhone 11, iPhone 11 Pro and iPhone 11 Pro Max 10 programming languages booming today
10 programming languages booming today Gmail, Google Drive and Calendar will be built into Outlook.com
Gmail, Google Drive and Calendar will be built into Outlook.com Successfully developing an AI model that can predict a seizure with an accuracy of 99.6%
Successfully developing an AI model that can predict a seizure with an accuracy of 99.6% The number of users regularly reached a record high, Microsoft Teams surpassed Slack
The number of users regularly reached a record high, Microsoft Teams surpassed Slack Attendance for some operating system platforms will no longer be able to use WhatsApp in the near future
Attendance for some operating system platforms will no longer be able to use WhatsApp in the near future