What are Five, Nine, and Fourteen Eyes? What purpose do they appear?
Before diving into this article, we should understand what VPN is, if not, you can refer to the following article: VPN theory - What is virtual private network?
Those who are interested in VPNs may have heard or even unfamiliar with terms like the previous Five, Nine, and Fourteen Eyes. A cult Hollywood movie has also mentioned these terms as SPECTER by James Bond, but in addition they are not mentioned much in the media, mass media. The film accurately describes the information it mentions about these networks, although this information is quite sensitive because they address issues related to international intelligence alliances, including agreements governing data collection (espionage) and sharing secrets between governments. However, don't worry if you haven't heard about it, most people in the world are like you.
Five Eyes
Five Eyes include Australia, Canada, New Zealand, United Kingdom and the United States. It was officially known in 1946 with two key members at the time, the United Kingdom and the United States, and gradually expanded to other countries in 1948. Since then it has only grown in scope and regulation. The tissue does not incorporate additional members, and now the members of the network can automatically share a large amount of intelligence data together, from phone records to spy satellite data.
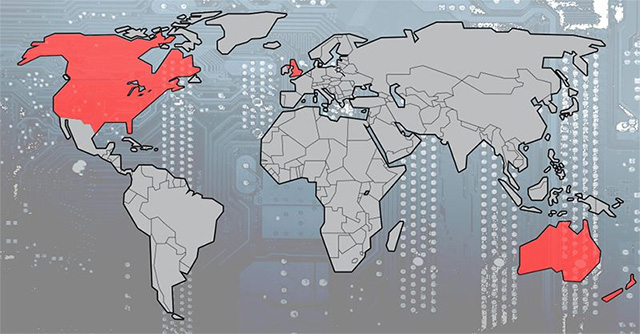
Historically, the existence of this alliance was extremely secretive, although there was leakage information, but this information was well managed to keep doubts about the existence of the network. share this intelligence for quite a long time. Even the office of the Australian prime minister, one of the original signatories of the agreement, was unaware of the existence of Five Eyes until 1973. Eventually, the agreement was confirmed in 2005. with the full text of the original UKUSA agreement that was released in 2010, although it was not until the Snowden service took place in 2013, its complete information was discovered.
So what is the main purpose of this network? Perhaps we cannot know the details, but it is understandable that this network possesses some very sophisticated technologies for both purpose-based and dragnet monitoring purposes. More specifically, "dragnet" means "analyzing data unchecked for later analysis."
This network often focuses on SIGINT, also known as signal intelligence, so if you communicate electronically via wave signals, network with someone, an intelligence agency can are listening to your conversation. The Five Eyes agreement means that each member state has access to the database and technology of another country, mainly through an updated database system that automatically concentrates, distinctive The name 'Stone Ghost' allows each country to access the intelligence of four other countries.
Most countries in this agreement agree not to allow their government to follow their citizens without going through legitimate channels, but the Five Eyes agreement has an interesting flaw not known because people unintentionally or unintentionally miss, it is a country that is not followed by citizens of their country, but other countries can. So a simple way to circumvent the law is to ask another country to follow its citizens and then ask them to share that information. Although there is not much data on the frequency of follow-up incidents, there have been many confirmed cases, including cases with New Zealand Prime Minister and John Key, and in 2015 Princess Diana entered. 1990s of the last century.
Nine and Fourteen Eyes
While Five Eyes is the closest intelligence alliance, with their automatic data sharing agreements, Nine and the Fourteen are less prominent intelligence networks. There is very little accurate information about how these networks work in real terms, but perhaps, these intelligence networks use slightly narrower intelligence data sharing channels, for example. For example, they probably won't have direct access to Stone Ghost.

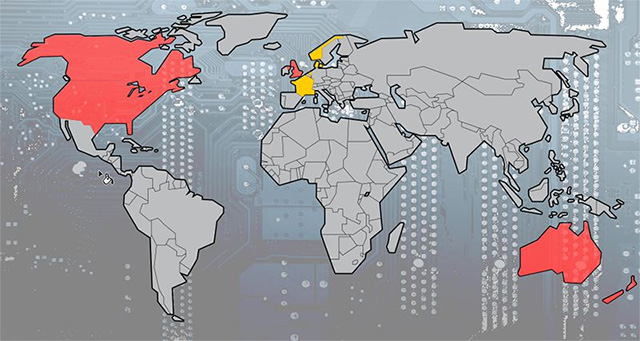
Nine Eyes includes Five Eyes, plus Denmark, France, Netherlands and Norway. We don't know much more about them, there simply aren't many official documents or documents that have been controlled. However, we can also assume that Nine Eyes is mentioned in James Bond's SPECTER film is a somewhat accurate description of Nine Eyes in practice.
Fourteen Eyes
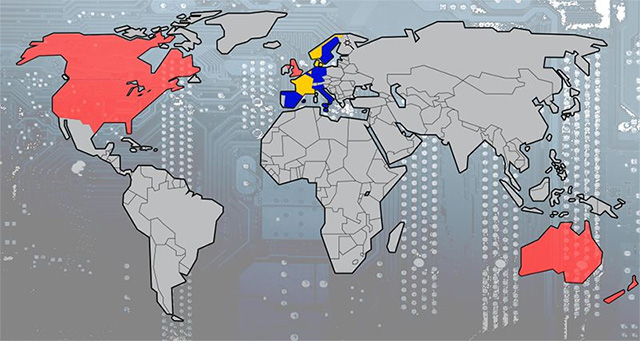
Fourteen Eyes is an intelligence alliance consisting of Nine Eyes plus Germany, Belgium, Italy, Spain and Sweden, and is in a separate group due to their membership ties in SSEUR, or SIGINT (signal intelligence) Seniors Europe, an intelligence coalition mainly operating in Europe. Like Nine Eyes, it is difficult to know exactly how different their access to personal data is, but according to Edward Snowden, Germany, Sweden and Japan it is obviously possible. permission to use XKeyScore, 'one-stop shop to access NSA information'. If a country in Fourteen Eyes has access to 'one stop shop for access to the NSA's information', the high rate is that they get more information.
Non-Eyes agreements
Although not related to "Eyes", there are in fact many signed agreements that allow countries to share information with each other. SIGINT Seniors Pacific (SSPAC) also includes India, Singapore, Korea and Thailand. This network can be compared to other countries in Fourteen Eyes because they are just another branch of SIGINT Seniors.
The US also uses hierarchical intelligence cooperation systems, classifying countries as Level 1 (Comprehensive Cooperation - Five Eyes), Level 2 (Collaborative cooperation - 16 countries, mainly in Europe), Level 3 (Limited cooperation - with countries like France, India and Pakistan) and Level 4 (Individual cooperation - countries hostile to US interests).
Last but not least in the world of large-scale intelligence alliances is a collection of third-party SIGINT partners from the United States, including thirty-three countries scattered across Africa and Europe. Asia and Europe. Previously, many high-ranking government officials, or even leaders, might not know that they were part of the deal, since these agreements were often set up directly with the agencies. newspaper and almost 'rarely interrupted by political diplomatic disorders'.
What do these networks earn and affect us?

The 'Eyes' and other intelligence partners hold all kinds of mechanisms to operate surveillance activities enough to write a very thick book. In general, although their technology is often described as an invasive surveillance tool, it is possible to collect most of the information sent via any type of line or signal or stored on any connected device. Internet connection. In addition, agreements in sharing also include media intelligence, such as defense, people and geospatial intelligence.
The 'Eyes' agreements and other intelligence partnerships allow relevant countries to access information in much more detail than they collect themselves. These shared tools and programs have been used successfully many times in the fight against terrorism, which is why these programs continue to be deployed, but the regular data of these Citizens are often scanned, stored, analyzed and shared by the program, which is an infringement of privacy.
Now, though, the activities of these intelligence networks are somewhat more widely known, but the things we don't know are the majority. However, it is not so that the scope of operation of these networks is affected. In September 2018, there were reports of a memorandum of understanding that Five Eyes states issued, indicating that they were considering breaking the coding, or by studying. their common or by legislative-based methods, such as forcing companies to provide access to encrypted or built products at the back. That obviously is not conducive to protecting privacy and can be a major problem for network security.
In general, unless you are a political activist, a criminal, a privacy guard or a conspiracy theorist, this does not directly affect your life. However, in the future, these alliances may affect some public policies and cause major technological problems.
The era for VPN has arrived?
If you are looking for a VPN, you are often advised to set a VPN that is beyond the control of 'Eyes', and to be more secure you will also want to avoid the management of third-party countries three and SSPAC. If your VPN is built on these factors, your privacy has improved a lot more than the average, but there is no guarantee that your data is completely invulnerable. The wide range of influences has been rooted in decades of the above-mentioned intelligence sharing agreements.
A multi-hop VPN is also a good way to ensure no one can interfere with the data you transmit over the Internet, but it's slower and more expensive. Tor (The Onion Route) is always a good choice, but if you really care about information security, you should also use to combine them with a VPN, because traffic between exit nodes Tor and destination servers are not encrypted and some nodes actually run and are monitored by intelligence agencies.
- 11 best VPN software
summary
Conspiracy theorists claim that there is a worldwide surveillance network but there may also be one day when things break out that there really is not just one but some. But for what each of us can know, it is simply the information that we consider private but not necessarily. It was a kind of 'privacy under control'. Since information about leaked intelligence control, new agencies and agreements may have been established, and new tools can be developed using advances in human intelligence. create and blockchain that we've seen in the last few years. Now, although it is sometimes reported, what we know about how intelligence agencies intervene in private data sources is still too small and it is becoming more sophisticated thanks to existing technologies. great.
See more:
- Google Account security guide with Google Authenticator
- What to do if Google Chrome warns an unsafe website?
- How does IP address and MAC address work in parallel?
- How to use ASCII characters to create strong passwords
You should read it
- ★ Things to know about a network intelligence analyst
- ★ 10 websites are indispensable for those who want to improve intelligence
- ★ Deep Learning - new cybersecurity tool?
- ★ Watching pictures painted by artificial intelligence, everyone thinks that is the work of a true artist
- ★ 6 steps to start learning artificial intelligence programming (AI)