Vault 8: WikiLeaks reveals the source code of the CIA malware control system
For the first time, WikiLeaks released source code for CIA's cyber attack tools.
The source code released today is tootkit called Hive, a system that allows CIA to control malware deployed on infected machines. From March to August this year, WikiLeaks has just released documents supporting the CIA's operations, thought to be hackers stealing and handing them over.
WikiLeaks declares Vault 8
Originally believed to be in the Vault 7 series, WikiLeaks now says that Hive is the opening shot for a series of similar releases called Vault 8, including source code for the tools mentioned in Vault. 7.
WikiLeaks' statement made cybersecurity security experts nervous when it recalls it in April, when The Shadow Brokers group released cyber-attack tools believed to be the CIA. These tools were then used for many malware families, notably three attacks on WannaCry, NotPetya and Bad Rabbit. The group also released a framework-like tool for transplanting and exploiting Hive as FuzzBunch.
Hive does not endanger end users
These tools are not dangerous to end users because they are not used to hack machines but only C&C servers, set up a backbone structure to receive and control commands that execute tasks on the victim machine.
The structure of Hive helps prevent communication with fake websites through many stages. Instead, the malware communicates directly with a fake website running VPS (Virtual Private Server) which looks very normal when opened directly on the web browser.
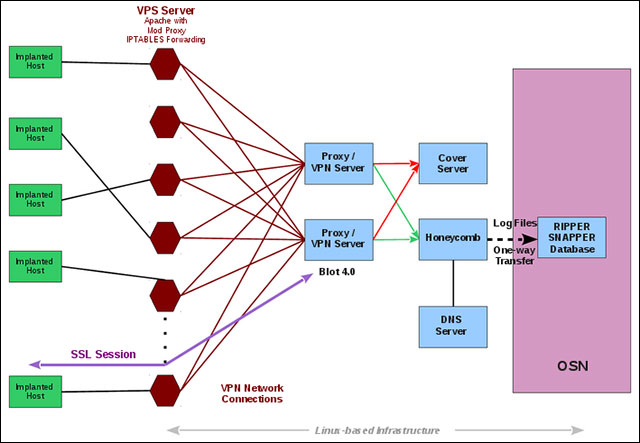
Hive operation diagram
But in the background, after being authenticated, the malware teaches to the web server (the fake website) and then passes the traffic related to the malware to the hidden CIA server called Blot via VPN. Blot will move to the operational management portal called Honeycomb.
Hive is widely released, anyone can download it. If WikiLeaks released the source code of 23 hacking tools in Vault 7, it is not known what will happen.
You should read it
- ★ NoCrack makes passwords safer with 'trap' fake vault
- ★ How to hide photos, videos, personal data on iPhone / iPad?
- ★ How to secure files in OneDrive with Personal Vault
- ★ How to protect files in OneDrive with 2FA with Personal Vault
- ★ Hack the company selling Israeli smartphone hack tools, hackers get the bitter end