Wikileaks reveals Cherry Blossom - the CIA's wireless device hacking system
Wikileaks has revealed a new wave of Vaut 7 leak - a detailed description of a framework being used by the CIA to track Internet activity of targeted systems by exploiting vulnerabilities in devices Wi-Fi.
The "Cherry Blossom" system is a framework designed by the US Central Intelligence Agency (CIA) with the support of the Stanford Research Institute (SRI International) - a US non-profit research institute as a part of the "Cherry Bomb" project.
Basically, Cherry Blossom is a firmware, which can be remote-controlled, "implanted" on wireless network devices, including routers, wireless access points (APs), exploit router vulnerabilities for unauthorized access, then replace the firmware with Cherry Blossom.
A leaked CIA handbook states that: An implanted device (called Flytrap) can be used to monitor Internet activity and bring software vulnerabilities to targeted attacks. .
Besides, WikiLeaks said: " Wireless devices themselves are compromised by implanting customized Cherry Blossom software on it, some devices allow the firmware upgrade via a wireless link. There is no need to physically access the device to infect it . "
Also according to WikiLeaks, CIA hackers use Cherry Blossom to attack wireless network devices on destination networks, then perform Man-in-the-Middle attacks to monitor and control traffic. Internet of users connecting.
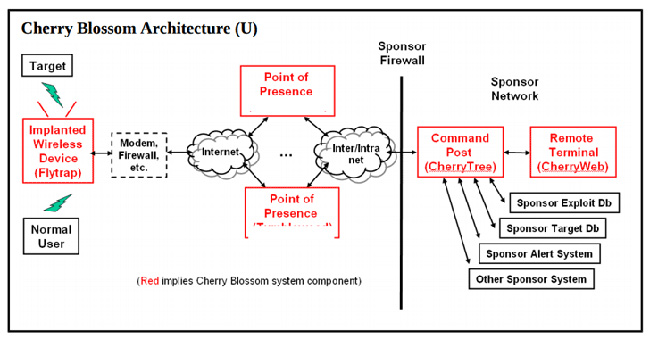
Cherry Blossom received instructions and tasks to execute malicious code from a server, called the CherryTree by the CIA. Once the wireless device has been controlled, it will send a report to this server, including the following contents:
- Monitor network traffic to collect email addresses, user names in chat applications, MAC addresses and VoIP numbers.
- Redirect users connected to malicious websites.
- Infecting malicious content into the data stream to spread malware and infiltrate connected systems.
- Set up VPN "tunnels" to access clients connected to WLAN / LAN networks of Flytrap to continue exploiting.
- Copy the entire network traffic of the hacked device.
According to the installation instructions, the CherryTree C&C server must be located in a completely secure facility and installed on the Dell PowerEdge 1850 virtual server, running Red Hat Fedora 9 with a minimum RAM of 4 GB.
Cherry Blossom can hack Wi-Fi devices from many providers
Cherry Blossom can exploit vulnerabilities in hundreds of Wi-Fi devices manufactured by the following vendors:
Belkin, D-Link, Linksys, Aironet / Cisco, Apple AirPort Express, Allied Telesyn, Ambit, AMIT Inc, Accton, 3Com, Asustek Co, Breezecom, Cameo, Epigram, Gemtek, Global Sun, Hsing Tech, Orinoco, PLANET Technology, RPT Int, Senao, US Robotics and Z-Com.
Leakage Vault 7 of the previous CIA
Last week, WikiLeaks revealed a CIA project called Pandemic, which allowed the organization to convert Windows servers into secret attack devices, silently infecting other computers in the same network. hack.
This tool is a long-term implant for Microsoft Windows computers, designed to infect Windows computer networks through the SMB (Server Message Block) file sharing protocol by replacing the online application code with The version of the software has been trojanized.
Since March, the spy group has released 11 installments in the Vault 7 series, including the latest leaks, last week's leak, along with the following rounds:
- Athena - A CIA spy software framework designed to control remote infected Windows computers and work on all versions of Microsoft Windows, from Windows XP to Windows 10.
- AfterMidnight and Assassin - These are two CIA reading malware frameworks specifically for the Microsoft Windows platform, designed to monitor and send reports of actions on infected remote servers and perform harmful actions .
- Archimedes - A Man-in-the-Middle (MitM) attack tool created by the CIA targeting computers on the same LAN.
- Scribbles - Is part of the alleged software designed to track classified documents, allowing intelligence agencies to track international whistleblowers and spies.
- Grasshopper - Disclosure framework allows this organization to easily create customized malware to infiltrate Microsoft's Windows system and bypass antivirus software.
- Marble - Revealed the source code of a secret anti-legal framework, basically an obfuscator used by the CIA to hide the true source of malware.
- Dark Matter - Focus on exploiting an organization's vulnerability, designed to target iPhone and Mac devices.
- Weeping Angel - A spy tool used by organizations to infiltrate smart TVs, convert them into secret microphones. The tool can record from a device via the integrated microphone and store or extract data from the record.
- Year Zero - A CIA hack program that declares other hardware and software popular.
You should read it
- ★ 8 best Wifi analysis and hacking software
- ★ WikiLeaks revealed malware of CIA hacks and spies on Linux computers
- ★ Vault 8: WikiLeaks reveals the source code of the CIA malware control system
- ★ Basic hacking techniques - Part II
- ★ Hack the company selling Israeli smartphone hack tools, hackers get the bitter end