The hyperlink test command is being used by hackers to perform DDoS
Researchers have recently discovered that an HTML feature is to test the hyperlink auditing, or ping for short, being used by hackers to implement targeted DDoS attacks. to many different websites. This feature is often used by websites to track clicks on links, but is currently abused by an attacker to send a large number of web requests to these websites. , thereby forming DDoS attacks that cause site disruption.

- DDoS is ranked as the top threat for businesses in 2018
If you don't know, hyperlink checking is basically an HTML feature that allows websites to track clicks on links on their pages. To create hyperlinked or ping test URLs, you first need to create a regular hyperlinked HTML tag, but include the ping = "[url]" variable as shown in the image below.
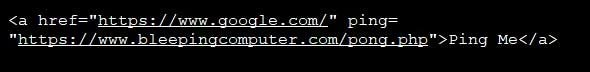
According to the above example, when a user clicks on the link, their browser will first connect to the website with the address https://www.bleepingcomputer.com/pong.php with a POST request and then, Navigate the browser to Google. This causes your browser to connect to 2 different websites while you only click 1 link.
For ping-receiving websites, administrators can check the POST request headers to see which site clicks originated from (Ping-From title), and also determine whether the link will lead to any website (Ping-To title).
Although not as popular as JS and tracking redirects, this feature is often used by Google in its search results sessions to track clicks on their links.
- Black Nurse - DDoS technology makes it possible for a normal laptop to take down a server as well
Ping is abused to perform DDoS attacks
In the new Imperva security research group, network security experts have discovered that HTML ping commands are being used by attackers to perform distributed denial of service (DDoS) attacks on many Different websites.
Accordingly, this form of attack is often done primarily by users with IP from China, and at the same time nearly all attackers are mobile users using the QQBrowser browser. During the study, Imperva discovered about 4,000 IP addresses, which involved sending about 70 million web requests in less than 4 hours.

- Danger: Hackers can target medical devices, change medical examination and treatment results
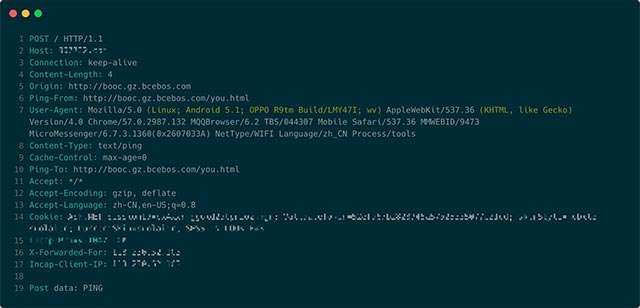
Strangely, all PING requests that Imperva observed show that both the Ping-To and Ping-From header values come from http:///booc.gz.bcebos address [.] Com. /yo.js?version=cc000001. The reason for saying this is a strange phenomenon because normally the link URL will be different from the URL where the link is clicked.
Below you can see a sample POST request extracted from this attack:
When checking the you.html page from Ping-To and Ping-From titles, Imperva's experts can understand what's going on. The you.html page (shown below) will load 2 JS files used to perform DDoS ping HTML attacks.
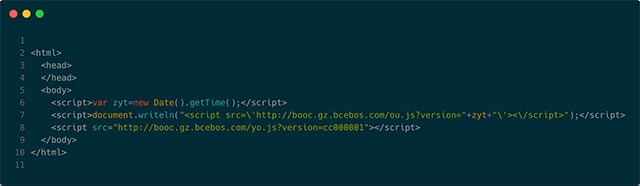
The ou.js file (shown below) contains a series of websites targeted for this DDoS attack.
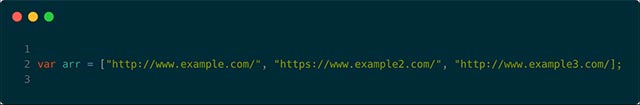
Meanwhile the yo.js script (shown below) will randomly select one of the sites above and create an HTML ping URL with that site as the target to ping. It will then programmatically click on the link, as shown by the link.click () command.
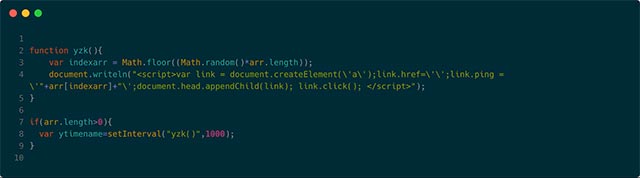
JavaScript will then create a new HTML ping URL and click on every second. Therefore, the longer the user is on this site, the greater the number of clicks they generate.
Imperva's team theory is that attackers have used social engineering and malicious advertising to direct users to pages that store these scripts:
"We found that user agents in requests are linked to a popular Chinese chat application, WeChat. WeChat uses the default mobile browser to open links in messages. Plus QQBrowser is very popular in China, so many users often choose it as the default browser for their smartphones.
Our theoretical point of view is that an attacker has used social engineering combined with malicious ads (malicious advertising) in order to trick WeChat users to open QQBrowser browsers without any doubt. Here is a scenario that we think is likely to have occurred:
- Step 1: The attacker injects malicious ads that are responsible for downloading a suspected website.
- Step 2: Link to legitimate websites with malicious ads in an iframe posted to a large group chat on the WeChat platform
- Step 3: Legal users access the site with malicious ads.
- Step 4: Executable JavaScript code will create a link to the ping attribute that the user clicks.
- Step 5: HTTP ping request is created and sent to the destination domain from the legitimate user browser ".
The good news is that at the moment, by disabling the hyperlink checking feature in the browser, we can easily prevent the abuse of the browser from being a factor in check attacks. Check hyperlinks as described above.

- Insider attacks are becoming more and more popular and difficult to detect
However, the worst problem lies in the fact that most popular browser platforms, except Firefox and Brave, are slowly establishing a hyperlink checker as the default feature that users won't have. Which is disabled.
Disabling the ping HTML command will be omitted soon
According to the information we know, Ping HTML will now become the default feature on popular browsers like Chrome, Edge, Safari and Opera, allowing hyperlinks to be checked by default and most still allow The user disables it. However, it is likely that future versions of these browsers will no longer allow users to disable hyperlink checking.
The inability to disable hyperlinked testing is not only a privacy-related risk but also a cause that many people fear will lead to bad consequences beyond the user's control. The case of DDoS attack is just one of them.
Going back to this ping-based DDoS attack, the most important thing now is that you should disable hyperlink checking on your browser. As mentioned, currently, the only browsers disable the hyperlink checking by default and continue to provide the option to disable this feature for Firefox and Brave users.
You should read it
- ★ This is a simple way to find and delete Hyperlink in Excel
- ★ Warning: DDoS attacks are becoming more dangerous both in scale and complexity
- ★ How many DDoS cases are reported in 2019?
- ★ Hyperlink (Hyperlink) in PowerPoint 2016
- ★ Telegram is heavily DDoS-heavy, but no significant damage is recorded