A ransomware declared decommissioned and refunded the ransom to the victim
Immediately after officially announcing the end of operations recently, the team of administrators behind Ziggy ransomware has just announced that they will also refund the ransom data for victims.
This is clearly a strange move. It is not uncommon for a ransomware strain to publicly announce stopping working and even releasing the decoder publicly. However, declaring decommissioning and returning the ransom to the victim is certainly extremely rare in the world of ransomware.
Shutdown then refund
Ziggy malware was declared decommissioned in early February 2021. In a brief statement, the team of administrators behind the malware said that they felt "sad and regretful" about the troubles caused by many people, and "decided to release all the keys. available data decoding ".
Saying done, 24 hours later, on February 7, Ziggy's admin team publicly released an SQL file, which contained 922 decryption keys that victims of this malicious code could use to decrypt your file.
In particular, administrators also provide a decryption tool to make the data decoding process easier. Along with that is the source code for a decoder that can work without an internet connection - an extremely 'mindful' act.
The story culminated on March 19, when Ziggy ransomware's administrators said they wanted to return the data ransom they had earned to the victims. Many people were skeptical of this unbelievable decision. But after more than a week of silence, on March 28, the Ziggy administrators announced they were ready to revert payments to their respective victims.
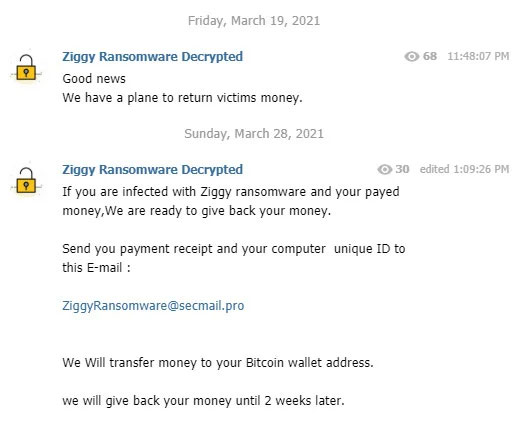
Victims of the Ziggy malware can contact administrators at ziggyransomware@secmail.pro, along with proof of the data ransom payment with bitcoin and computer ID. The Ziggy team pledges that the corresponding amount will be returned to the victim's bitcoin wallet after about two weeks.
It is still not possible to confirm the motive for the hackers to make a series of 'strange' decisions above. The people behind the malware say they feel 'repentant', but do not rule out the possibility of fear of facing law enforcement agencies for their offenses. out. Especially after much larger ransomware operations such as Emotet and Netwalker were recently 'shot down'.
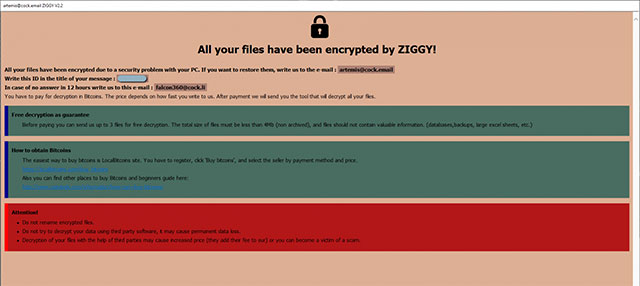
Whatever the real reason, these are welcome and beneficial moves for Ziggy's victims.
You should read it
- ★ Learn about Ransomware: 6 ransomware on computers
- ★ PureLocker - a very 'weird' ransomware strain that can encrypt servers
- ★ Detecting a new ransomware strain, not asking for data ransom, but only needing the victim to join the Hacker's Discord server
- ★ List of the 3 most dangerous and scary Ransomware viruses
- ★ How to remove Moba ransomware from the operating system