Steal encryption key AES256 thanks to PC's electromagnetic emission
The device exploits a side-channel attack known as Van Eck Phreaking and is built specifically to recover the encrypted key segment from the AES256 algorithm.
The attack performed at a test price of € 200 / $ 230
Such attacks often use expensive equipment, but researchers say they can do it for as little as € 200, equivalent to $ 230.
The tools needed to get the encryption key include magnet antenna, external amplifier, band pass filter and SDR with USB port. The team says that small items can fit in other pockets, laptop bags or any small bags. They thought the attacker could bring these items near the computer or encryption processing equipment, thereby stealing from electromagnetic waves.
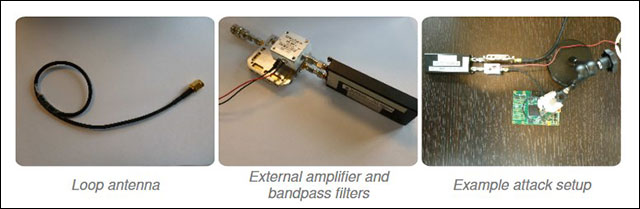
The tools needed to perform an attack on the encryption key
If the device puts about 1 meter around the hacked machine, it will take up to 5 minutes to get the encryption key segment. If the distance is shorter than 30 cm, the device only needs 50 seconds. Theoretically, the closer the attacker is to the target, the stronger the electromagnetic wave, the shorter the time needed to steal the encryption key.
Device encryption key prediction device
Inside, the device works by recording electromagnetic waves exiting the computer next to it, calculating the power consumption skyrocketing.
'This is useful because part of the electricity consumption is dependent on the amount of data that the device has to handle', the researchers say, 'this is the data we exploit to get the key segment' .
Experts say they can determine cascblock where the encryption key is applied through the surge in power consumption needed to calculate, using the AES256 algorithm. Once discovered, they will move on to the next step '.

The tool is set up inside the sealed box
Now we will get the key by correlating and predicting [.] like attackers, we don't know the key [encryption] . but we can make predictions and correlations. with all 256 values available from the key segment. The value with the highest correlation will be the correct value. In this way, we only need a few seconds to guess the correct value for each byte (256 choices per byte, with 32 bytes totaling 8192 guesses). Conversely, a properly used trial and error attack with AES256 will require 2256 guesses and will never be completed.
Only test attack in the laboratory
Theoretically, the device is ready to attack network encryption devices in data centers or air-gap networks, and even regular computers.
However, the group's experiment only performed in isolated environments, where both the target and the attack tool were separate from external electromagnetic waves. It is not clear whether the attack in the real environment will produce the right result, because it will be affected by the electromagnetic waves of other surrounding devices.

Attack environment in the laboratory
This study was documented in the name of TEMPEST Attack taking AES . Van Eck Phreaking attacks were also carried out earlier in similar reports. A group of scientists from Israeli University also used a similar attack to get the encryption key from a computer in the next room, through a thin wall. Another project by Australian and Israeli researchers took encryption keys from electromagnetic waves of Android and iOS devices.
You should read it
- Top 5 best USB encryption software
- Top 20 best encryption software for Windows
- What is Zero-Knowledge Encryption? Why use this type of encryption?
- Discover the difference between symmetric and asymmetric encryption
- Adiantum, Google's new encryption method helps ensure safety for all Android devices
- What is data encryption? Things to know about data encryption
 IBM's new mainframe is faster, encrypts everything, effectively hides the source code for the business
IBM's new mainframe is faster, encrypts everything, effectively hides the source code for the business Apple's new Emoji is coming with many character and expressive animations
Apple's new Emoji is coming with many character and expressive animations The fourth largest virtual currency trading platform was hacked, leaving many people losing bitcoin and ethereum
The fourth largest virtual currency trading platform was hacked, leaving many people losing bitcoin and ethereum Why does iOS 14 become Apple's smartest software of all time?
Why does iOS 14 become Apple's smartest software of all time? HEIF - New image format will take the throne?
HEIF - New image format will take the throne? OpenBSD will create its own kernel each time you reboot the machine, giving you better security
OpenBSD will create its own kernel each time you reboot the machine, giving you better security