More than 1.7 billion cyber attacks in 2013
2013 has occurred more than 1.7 billion cyber attacks worldwide, and the future trend will be mobile attacks.
Mobile is a fast growing IT sector. In 2013, security issues around mobile devices have reached a new level of increase in both quantity and quality. If 2011 was the year the mobile malware started to attract attraction to hackers, then in 2013, these malicious software became more complete and sophisticated.
These mobile threats
Obad is perhaps the most remarkable discovery in the mobile sector, being distributed by many methods, including a pre-established botnet. Android smartphone if infected with Trojan-SMS.AndroidOS.Opfake.a will turn into a mirror, it sends text messages containing malicious links to all phone numbers in the directory .
Mobile botnets offer a significant advantage over traditional botnets: smartphones are rarely powered off, most access is always available and only waiting for an attack command. Common tasks that botnets perform include mass spamming, DDoS attacks and stealing personal information, all of which do not require performance and are easily implemented on smartphones.
Applications with vulnerabilities are exploited by hackers
According to Kaspersky Lab , 90.52% of the attempts to exploit the discovered vulnerability target Oracle Java. The second position belongs to the Windows component, including Windows operating system files that have vulnerabilities, not considering Internet Explorer and Microsoft Office . Most attacks on Windows target a vulnerability discovered in win32k.sys.

Some applications with vulnerabilities are exploited by hackers
Third place is the vulnerability on Android. Cybercrime or users themselves use vulnerabilities on Android to gain device control ( root ). Recently, there is information that Chrome browser for Nexus 4 and Samsung Galaxy S4 has a flaw and may be exploited in the future.
Online threats
The number of online attacks worldwide increased from 1,595,587,670 in 2012 to 1,700,870,654 in 2013.
Compared to last year, the growth rate of browser-based attacks has decreased. The number of these attacks was disabled in 2013 by 1.07 times compared to 2012, while 2012 was 1.7. The main tool behind browser-based attacks is still the update package containing vulnerabilities, giving cybercriminals the chance to infect malicious code with their computers quite easily.
In order to carry out 1,700,870,654 attacks on the Internet, cybercriminals used 10,604,273 unique servers, 4 million more than in 2012. In 2013, there was a slight change in ranking 10. the leading country distributing malware compared to 2012, in which the US ranked first, while Vietnam appeared at the 8th position.
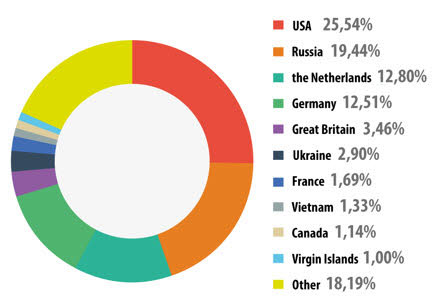
Ranking countries accounts for the largest proportion in spreading malicious code.
Predict 2014
Alexander Gostev, Head of Security, Global Research and Analysis team, Kaspersky Lab , commented: "The Internet has begun to break down into national fragments. The leak of Snowden has boosted demand for regulation. The next step is likely to be an attempt to limit access to foreign data in countries, as this trend further develops may lead to the collapse of foreign services. Currently internet, breaking into dozens of different networks ".
Some countries have applied or are planning to apply laws prohibiting the use of foreign services. In November, Germany announced that all communications between German authorities would be completely locked in the country. Brazil has announced plans to build an alternate internet channel so that it will not use the route that goes through Florida (USA) .
You should read it
- ★ Warning: DDoS attacks are becoming more dangerous both in scale and complexity
- ★ How many DDoS cases are reported in 2019?
- ★ Most cyber attacks focused on these 3 TCP ports only
- ★ Network security challenges in 2014
- ★ Download and sell Windows patches for all versions to avoid being hit by a massive cyber attack, affecting 150 countries and still spreading