Microsoft Azure is being used to host malware and C2 servers
In recent times, Microsoft Azure cloud services have become an attractive address for malicious content for cyber criminals worldwide. From pure pattern scams to malware or even command and control services (command and control services) . all were found on the Azure cloud, apparently guys. Time has found an ideal storage location for your 'project-causing tool'.
In just last May, many major news sites and cyber security organizations simultaneously discovered and reported on two incidents related to malware stored on Azure. There is an extremely dangerous case with about 200 websites displaying scams following a technology support scenario that has been hosted on this very popular cloud platform.

- GandCrab blackmail extinguished after earning $ 2.5 billion worldwide
Another finding released last week by the BleepingComputer technology site has released a message regarding Azure being used to store phishing samples designed for Office 365 services. and Office 365 are both Microsoft products, this form of fraud appears as a legitimate login request, significantly increasing the success rate.
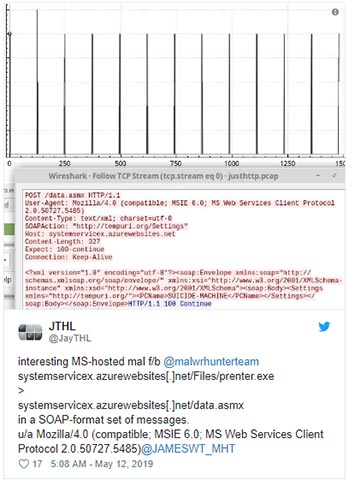
This may not seem like a coincidence when security researchers from the MalwareHunterTeam team and network security engineer JayTHL found malware on Azure and reported it to Microsoft on the 12th. 5.
- The Linksys smart Wi-Fi router was found to contain information leaks of connected devices
According to the discovery by network security expert David Pickett of cybersecurity company AppRiver, malware has been reported, but other malicious samples uploaded later are still available on the infrastructure. Microsoft Azure on May 29. From the above fact, it can be obvious that the Azure team did not detect the malware residing on their servers.
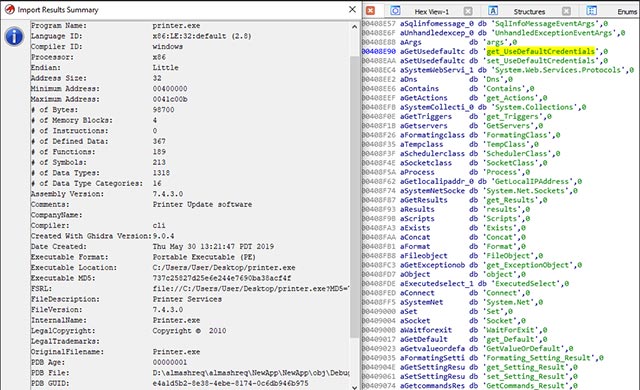
One of the malicious samples discovered - 'searchfile.exe' - was indexed by VirusTotal security service on April 26, and Windows Defender discovered it.
The same scenario happens with malware found by two research teams JayTHL and MalwareHunterTeam: 'printer / prenter.exe'. This is actually an unmodified mobile executable file, supposedly to better hide itself, to avoid detection by port security and endpoint solutions when downloading.
- UC Browser Android - lucrative bait for URL spoofing attacks
However, Windows Defender will boot and block this malicious file when users try to download them on the computer.
David Pickett said that when the malicious model 'print.exe' is executed, the command line (command line) will be called to run the C # compiler and thereby activate the payload of the malicious code.
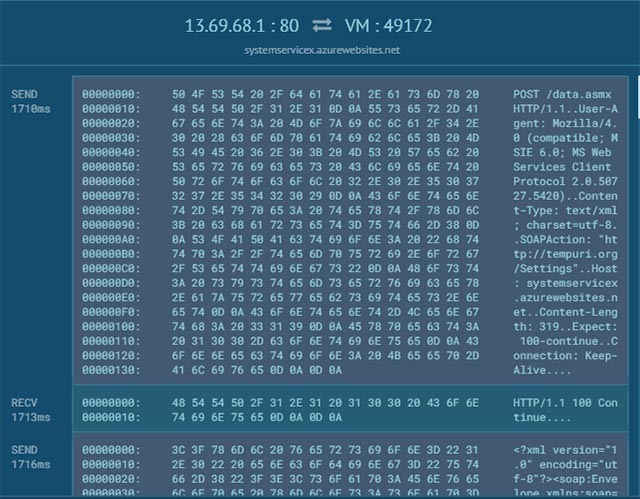
'After launching, this malicious agent will generate SOAP XML requests every 2 minutes to register as well as receive commands from the Azure poisoning control and web site at: systemservicex [.] azurewebsites [.] net / data [.] asmx, '.
- More than 4,000 Office 365 accounts are affected by account hijacking attacks
Meanwhile, JayTHL also detailed that this malicious model seems to be a simple agent that runs any command it receives from the command and control server (C2 server). According to this security expert, up to 90 bots can be controlled, if their ID numbers are created in sequential order.
In fact, Microsoft Azure will not be the first big name cloud platform to be abused to store malicious content. Similar services of Google Drive, Dropbox and Amazon, have also been victims of this malicious storage. Often, cyber criminals will invade, then try to take control of legitimate websites and use them to store malicious content, but of course these criminals will not hesitate to catch it. Any opportunity to make a profit, especially if there is little risk and does not take too much effort.
You should read it
- ★ Appeared software can penetrate iCloud, Google Drive
- ★ Bring Amazon Cloud Drive to your computer
- ★ 14 games on the App Store contain malicious code, iPhone users be careful
- ★ The battle between Cloud hosting services: SkyDrive, Dropbox and Amazon Cloud Drive
- ★ AWS and Azure dominate the cloud world, above all, no one wins