Learn about Sigcheck of Microsoft
Sigcheck is a command line utility that displays file version numbers,timestampinformationand digital signature details, including certificate strings.It also includes an option to check the status of a file on VirusTotal.com, an automated file scanning site with more than 40 antivirus tools and file upload options.
usage: sigcheck [-a][-h][-i][-e][-l][-n][[-s]|[-c|-ct]|[-m]][-q][-r][-u][-vt][-v[r][s]][-f catalog file] usage: sigcheck -d [-c|-ct] usage: sigcheck -o [-vt][-v[r]] usage: sigcheck -t[u][v] [-i] [-c|-ct] 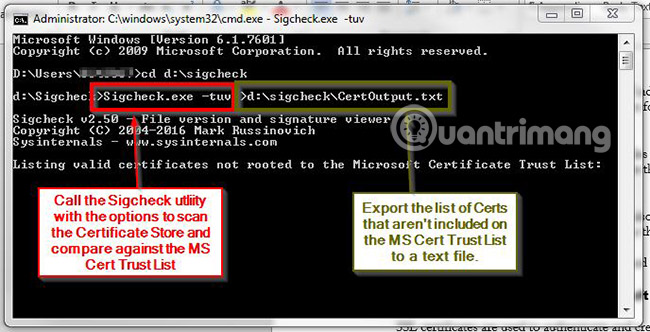
- Specify -tu to query the user store (the machine store is the default option).
- Combine with '-v' to Sigcheck to download Microsoft trusted root certificate list, and export only valid certificates that cannot be rooted in a certificate in that list. If the website cannot be accessed, authrootstl.cab or authroot.stl in the current directory is used instead (if available). -u If VirusTotal's checking feature is enabled, files that VirusTotal does not identify or detect non-zero (containing other digits) will be displayed, otherwise it will only display files signed only. -v [rs] - VirusTotal query (www.virustotal.com) for hash-based malware.
- Add 'r' to open the report for detected files that are non-zero.
- Files that are reported to have not been scanned before will be uploaded to VirusTotal, if the 's' option is specified. Note that it takes 5 minutes or more to get the scan results. -vt Before using VirusTotal features, users must accept VirusTotal's terms of service. Visit https://www.virustotal.com/en/about/terms-of-service/ for more details. If you do not accept the terms and ignore this option, the user will see a warning message appear.
One way to use this tool is to check the unsigned files in the WindowsSystem32 directories with this command:
sigcheck -u -ec:windowssystem32 Users should check any unsigned files.
Sigcheck tool runs on:
- Client: Windows Vista or later
- Server: Windows Server 2008 or later
- Nano Server: 2016 and above
Download Sigcheck.
Please refer to the article: The software's Certificate Checker is safe for more details on how to use Sigcheck.
See more:
- Learn about Microsoft Operations Studio from Microsoft
- Install SQL Server 2008
- What is Microsoft DirectX?
4.1 ★ | 29 Vote
 Synthesis of English abbreviations commonly used on social networks
Synthesis of English abbreviations commonly used on social networks Learn about Edge Computing: New boundary and border computing of the Web
Learn about Edge Computing: New boundary and border computing of the Web Some tools to help create online charts
Some tools to help create online charts The most important IT certificates
The most important IT certificates How is WDS Relay and WDS Remote different?
How is WDS Relay and WDS Remote different? Learn about TDP in CPU and why you need to care about it
Learn about TDP in CPU and why you need to care about it