How to Make It Look Like You Are Hacking
Method 1 of 3:
Using the Command Prompt
-
 Open the "Run" function on your computer. You can do this by clicking the start menu and finding the "Run" function, or you can do a general search of your computer for "Run" and find it that way.
Open the "Run" function on your computer. You can do this by clicking the start menu and finding the "Run" function, or you can do a general search of your computer for "Run" and find it that way.- Windows users can use hotkeys to open Run feature in two keystrokes: ⊞ Win+R[1]
-
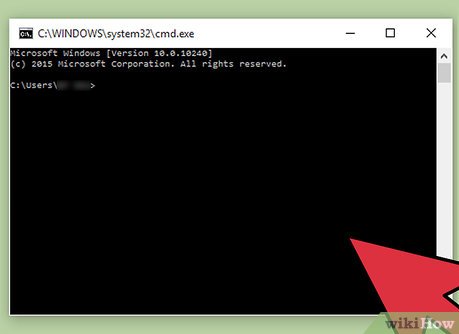
 Open the Command Prompt window. You can do so by typing in "Cmd" into the search box in your Run window. This will open the Command Prompt, also known as a Command Line, which is a text based way for you to communicate with your computer.[2]
Open the Command Prompt window. You can do so by typing in "Cmd" into the search box in your Run window. This will open the Command Prompt, also known as a Command Line, which is a text based way for you to communicate with your computer.[2]- Apple users can open the command line of the Terminal, the Mac version of Command Prompt, by using Spotlight search or a general computer search for "terminal".[3]
-
 Use the Command Prompt or Terminal to imitate hacking. There are many commands that can be used in Windows Command Prompt and Apple Terminal to execute commands or query for information. The following commands, while looking impressive, will not damage your software and are not illegal.
Use the Command Prompt or Terminal to imitate hacking. There are many commands that can be used in Windows Command Prompt and Apple Terminal to execute commands or query for information. The following commands, while looking impressive, will not damage your software and are not illegal.- Windows users might try typing the following commands, hitting ↵ Enter after each command, in relatively quick succession to make the process seem more complex:
- color a
- This will change your Command window text from white to green with a black background. Replace the letter following "color" with the numbers 0 - 9 or the letters A - F to change your Command Prompt font color.
- dir
- ipconfig
- tree
- ping google.com
- The Ping command checks if a device can communicate with another over a network (but the common person doesn't know that). Google is used as an example here, but you can use any site.
- color a
- If you own an Apple computer, you can use the following safe commands to fill your screen with what looks like professional hacking. Input the following into your Terminal window to achieve that effect:
- top
- ps -fea
- ls -ltra
- Windows users might try typing the following commands, hitting ↵ Enter after each command, in relatively quick succession to make the process seem more complex:
-
 Alternate between commands and windows. You can open a few Command Prompt or Terminal windows, using various commands to make it seem as though you are performing several highly complex, unrelated processes at once.
Alternate between commands and windows. You can open a few Command Prompt or Terminal windows, using various commands to make it seem as though you are performing several highly complex, unrelated processes at once.
Method 2 of 3:
Making a .bat File in Windows
-
 Open notepad. To make a .bat file, you will have to write plain text in a text editor and save it so that your computer reads this text as executable commands. Notepad or any other basic text editor will work to write a .bat file.
Open notepad. To make a .bat file, you will have to write plain text in a text editor and save it so that your computer reads this text as executable commands. Notepad or any other basic text editor will work to write a .bat file. -
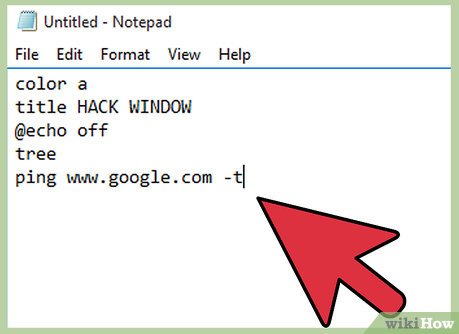
 Write the processes for your .bat file in notepad. The following text will open a window with green font, entitled "Hack Window." To change the title, you can change the entry following "title" in your notepad file to your preference. The text "@echo off" hides the command prompt, while "tree" will display a directory tree, making the hacking seem more realistic. The last line of text will ping google's server, which is not illegal yet looks like hacking to the untrained eye. Input the following text into your blank notepad document:
Write the processes for your .bat file in notepad. The following text will open a window with green font, entitled "Hack Window." To change the title, you can change the entry following "title" in your notepad file to your preference. The text "@echo off" hides the command prompt, while "tree" will display a directory tree, making the hacking seem more realistic. The last line of text will ping google's server, which is not illegal yet looks like hacking to the untrained eye. Input the following text into your blank notepad document:- color a
title HACK WINDOW
@echo off
tree
ping www.google.com -t
- color a
-
 Save your document as a .bat file. When saving your file, you will need to select "Save as." In the prompted dialogue box, name your file and end your name with ".bat". This will change your file from a text document to a batch file. Batch files contain text that gives your computer operating system a series of commands.[4]
Save your document as a .bat file. When saving your file, you will need to select "Save as." In the prompted dialogue box, name your file and end your name with ".bat". This will change your file from a text document to a batch file. Batch files contain text that gives your computer operating system a series of commands.[4]- This might not work on Windows Vista.
- You may receive a message warning you that saving a file with a .bat extension will remove all formatting. Click "Yes" to finish creating your .bat file.
-
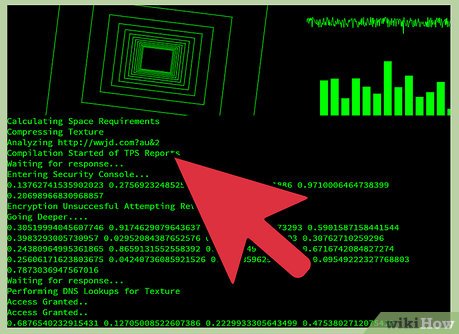
 Run your .bat file. Double click your .bat file in its containing folder to open a window that will look, for all intents and purposes, like you are performing some complex computer process, like a hacker.
Run your .bat file. Double click your .bat file in its containing folder to open a window that will look, for all intents and purposes, like you are performing some complex computer process, like a hacker.
Method 3 of 3:
Using Online Sites
-
 Open your web browser. Some websites are intended solely for the the purpose of imitating complex computer functions. Some of these are used for effect in movies or videos, or by users like yourself!
Open your web browser. Some websites are intended solely for the the purpose of imitating complex computer functions. Some of these are used for effect in movies or videos, or by users like yourself! -
 Check out hackertyper.net. This website creates hacker-like text at an rate that is sure to shock those watching. One issue you may have with using this site to trick your friends is that it produces hacker-esque code too quickly, which may ruin the effect.
Check out hackertyper.net. This website creates hacker-like text at an rate that is sure to shock those watching. One issue you may have with using this site to trick your friends is that it produces hacker-esque code too quickly, which may ruin the effect. -
 Open a separate browser window and visit guihacker.com online. Leave your window open to the site, which should display stereotypical hacker images: lines of numbers, rapidly changing measurements, a high noise sine wave. With this running in the background, you could claim:
Open a separate browser window and visit guihacker.com online. Leave your window open to the site, which should display stereotypical hacker images: lines of numbers, rapidly changing measurements, a high noise sine wave. With this running in the background, you could claim:- "I'm just compiling some data that I got from a friend's server to see if there are any errors in the code. It has to run for a few hours."
- "I'm running some analytic programs in the background so I can see, real-time, how my processor is handling the increased temperature from overclocking."
-
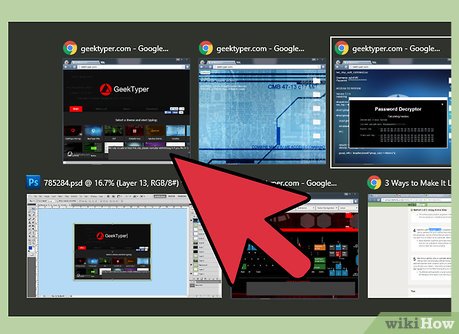
 Interface with geektyper.com's variously themed hack simulator. This site utilizes perhaps the most realistic hack-mimicking simulator. After arriving at the site homepage, choose a theme than proceed to type to prompt hacker-like text. You can even click on folders to run elaborate, albeit fake, processes.
Interface with geektyper.com's variously themed hack simulator. This site utilizes perhaps the most realistic hack-mimicking simulator. After arriving at the site homepage, choose a theme than proceed to type to prompt hacker-like text. You can even click on folders to run elaborate, albeit fake, processes.- Move between keystroke generated fake-hacker text and the fake processes that you can activate by clicking folders that will appear in your browser window after you choose a theme.
-
 Run these various sites in separate windows. Each of these sites has a slightly different feel and generates different styles of fake code/hacker text. You can alternate between open windows quickly by holding the Alt key and using Tab ↹ to cycle through your options. Type a few keystrokes into each window before Alt+Tab ↹-ing to a new fake-hacking browser window for improved effect. If the tabs are open on the same window, press Ctrl+Tab ↹.
Run these various sites in separate windows. Each of these sites has a slightly different feel and generates different styles of fake code/hacker text. You can alternate between open windows quickly by holding the Alt key and using Tab ↹ to cycle through your options. Type a few keystrokes into each window before Alt+Tab ↹-ing to a new fake-hacking browser window for improved effect. If the tabs are open on the same window, press Ctrl+Tab ↹.- Try different arrangements of open windows, or you can leave a few open in the background to make it look like you're a king hacker.
Share by
Marvin Fry
Update 24 March 2020