Eternal Blues - NSA's EternalBlue vulnerability testing tool
Researcher Elad Erez has created a tool called Eternal Blues, which helps system administrators check whether their computers have EternalBlue vulnerabilities and are exploited. Erez released the tool on Wednesday, a day after ransomware NotPetya attacked thousands of computers around the world.
- What is Petya? What is NotPetya? Is it really ransomware or is it even more dangerous?
Like what WannaCry did last month, NotPetya also exploited the EternalBlue vulnerability to hack into computers. In hacking and cyber security, EternalBlue is said to be one of the strongest vulnerabilities ever seen. Evidence of its effectiveness and its ability to create easy hazards are two ransomware attacks that took place in just 2 months.
EternalBlue uses the CVE-2017-0144 vulnerability in the SMBv1 file sharing protocol. The Windows SMBv1-enabled computer by default will use the attacker's SMB (SMB packet) packet and allow them to execute random code on the user's computer.
Eternal Blues - Simple tool for users
Technically, an attacker can hack a Windows computer with just one SMB package, which is how it works on Erez's tool.
Eternal Blues will detect computers within the network connection and see if it is vulnerable to fake SMB packets without exploiting the error to run any code. When users open Eternal Blues, it will allow them to scan the LAN but Erez says that the tool can scan any Internet and not just the local network.
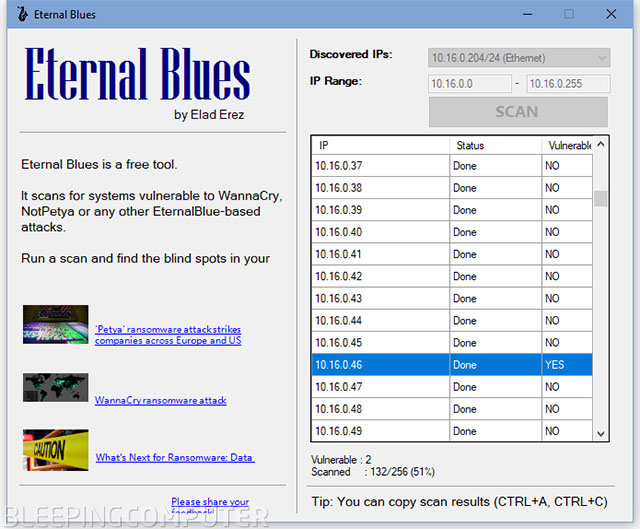
Eternal Blues screen software interface
Erez admits that his tool is not as advanced as NMap, Metasploit or other tools, but he intends to create a simple tool, with just one click to solve the problem, discover a hole Eternal Blue for users to know.
The subject of Eternal Blues are system administrators who know how WannaCry and NotPetya can attack computers and want to know if their computer network is vulnerable to updates when needed.
Anonymous data collection tool
Remember that this tool uses Google Analytics to collect anonymous data. The information obtained includes the number of scanned computers and the number of computers detected by each vulnerability. Erez said that the tool did not retrieve the hostname (hostname), IP address and other personal data.
Sharing with Bleeping Computer, Erez said that he will share some static data in the future. 'To date, there have been more than 350 scans from 50 countries in less than 24 hours.' Erez is currently the creative director at Imperva and created this tool as a personal project. Users can report bugs and download Eternal Blues on his personal blog site.
You should read it
- ★ IBM developed a new technology to patch security holes
- ★ Samba vulnerabilities allow hackers to invade thousands of remote Linux computers
- ★ The Mail app on iOS has serious vulnerabilities
- ★ Many serious vulnerabilities have been discovered that allow attackers to take full control of the 4G router
- ★ Microsoft warned about malicious spam campaigns using vulnerabilities in Office and Wordpad