Detected a new data theft campaign targeting AnyDesk users
International security researchers are currently closely monitoring the activities of a hacker group specializing in data theft and extortion called Mad Liberator. This group of hackers is currently actively deploying a malicious attack campaign targeting users of the AnyDesk remote computer access application, with the act of running fake Microsoft Windows update screens to distract while stealing. data from the target device.
Targeted at AnyDesk users
According to a report from cybersecurity company Sophos, researchers say the Mad Liberator attack begins with an unwanted connection to a computer using AnyDesk, an application that supports remote computer access today. Very commonly used in IT groups managing corporate environments.
It's unclear how hackers choose targets, but one theory that's getting a lot of consensus is that Mad Liberator will try potential addresses (AnyDesk connection ID) until someone accepts the connection request. .

Once the connection request is approved, the attacker drops a binary file named Microsoft Windows Update onto the compromised system, displaying a fake Windows Update welcome screen.

The sole purpose of this scam is to distract victims while the attacker uses AnyDesk's File Transfer tool to steal data from OneDrive accounts, network shares, and local storage.
During the fake Windows update screen, the victim's keyboard will be disabled to avoid interrupting the data extraction process.
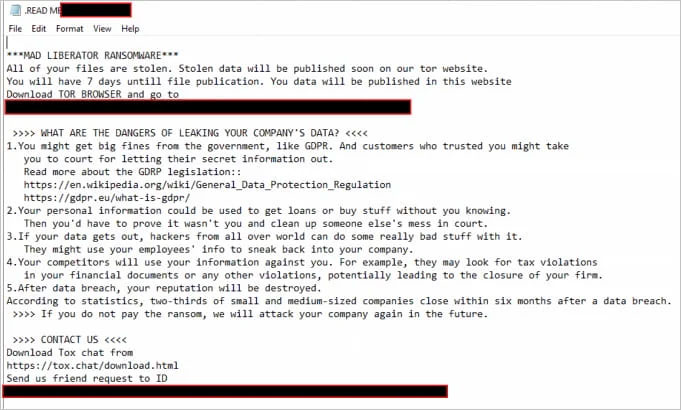
In the attacks Sophos detected that lasted about four hours, Mad Liberator did not perform any data encryption in the post-leak period. However, they still send ransom notes on shared network folders to ensure maximum visibility in corporate environments.
Sophos noted that it did not see Mad Liberator interact with the target before requesting an AnyDesk connection, and did not observe any phishing attempts in support of the attack.
Regarding Mad Liberator's extortion process, the hacker group states on their darknet site that they will first contact the compromised companies to offer "help" to fix security issues and restore files are encrypted if their monetary requirements are met.
If the victimized company does not respond within 24 hours, their name will be published on the extortion portal and given seven days to contact the threat actors.
After another five days of the ultimatum being issued with no ransom being paid, all the stolen files were published on the Mad Liberator website, which now has nine victims.