Data security risks for Sharepoint
Jesper M. Christensen
Network administration - Microsoft Office SharePoint Server 2007 (MOSS) and Windows SharePoint Services 3.0 (WSS) give companies the ability to collect data from various sources and publish these data on a centralized location. so users can access. But what do SharePoint administrators need to consider to ensure that important information is not disclosed widely to the general public?
In this article we will focus on the difficult challenges of protecting data on sites, links and SharePoint sites along with the information provided through links to systems. backend (via BDC and manually created data links). This article is primarily for readers who are network administrators and servers and SharePoint designers and publishers.
Why need to protect information?
There are many different 'inputs' about what we need to consider when 'publishing' content on SharePoint intranet sites. Sometimes it will be difficult to control or control this existing information if the structure of the content and secure access to the content is not well planned from the beginning. As the intranet grows, then designers and content providers must learn how to use SharePoint for team collaboration, document management, and dynamic reports. This content is also available to other employees and this is the main question for this issue: What information are they allowed to search and read? SharePoint puts all the information and has a centralized structure that really supports the employees and teamwork processes but can also be a major security hole if it is not properly protected. .
Let's start with an example scenario:
A company A provides effective key performance indicators (KPIs) on their SharePoint site to provide their leadership members with how to implement and deploy departments on a page. web. The developer has created a data connection to the financial database to extract data from here. The board members also have a blog on the same site as the site where they comment on the KPI weekly.

Figure 1: What is hidden behind the web?
In this example, the designers must ensure financial data connectivity so that only the necessary information is extracted from the database and must ensure that only the members of the commissioner are New leaders can access data and blogs. Board members must know the importance of configuring this security to ensure that the policy is followed. The worst case scenario is that designers will use BDC with a complete access account to the financial database and make it searchable - unlimited access to the site for any Who. In such a case, every user can search for financial data as well as read it and blog comments on the intranet.
Ensuring the intranet is a safe place is a well planned task. If everyone from the chief architect works to the average user knows about this and understands why and how to secure the content (and follow that policy) then your intranet will be a Safe location for data storage.
How to avoid trouble with company data?
When we talk about data security risks, there is a question: 'How can anyone avoid watching or even copying important information of anyone? we'. Today it is very difficult to protect 100% of people who cannot copy and retrieve your important data outside the company. But this is still possible, but how many companies have such restrictive security policies around the world is not that much.
SharePoint infrastructure has a very useful feature that we really appreciate: Users cannot view restricted content. This is a way we might need! And with Information Rights Management (IRM) added, we have a real user control. However, how is the data removed from SharePoint and where is it used? Obviously a SharePoint backup contains a lot of information, so keeping this information in a certain location does not allow users to access indiscriminately. However, if users have access and read content, they can fully exercise their rights here.
Internet browser
-
Copy-paste data into an application
- Export data to an XML file through the URL (owssvr.dll) protocol
Office products
-
Connections and exports can be made to Office applications.
- 'Connect to Outlook' can make data exposed offline and exported.
Other programs
- Calls can be made to SharePoint farm, either via Windows Powershell or other applications.
Copying data can be a problem and tools must adapt to employees. We can hide links and word pages for your users, but you need to set the permissions properly on lists, items and document libraries, . to avoid copying. or loss of important data.
Determine where to check or tighten security
So far, we have learned why it is necessary to secure such intranet networks. Identifying where to test and tighten security is a next challenge - a major challenge - and perhaps more technical. At this point, Microsoft SharePoint is a difficult problem that we need to solve. However, working with individual components can be made easier. As you can see in Figure 2, we have divided into separate sections for different data, how it is connected in SharePoint architecture and communication directions arrows. We have simplified some components and features but brought you a picture of what to look for in your own environment. If you need more details, please visit Microsoft TechNet to get the complete diagram.
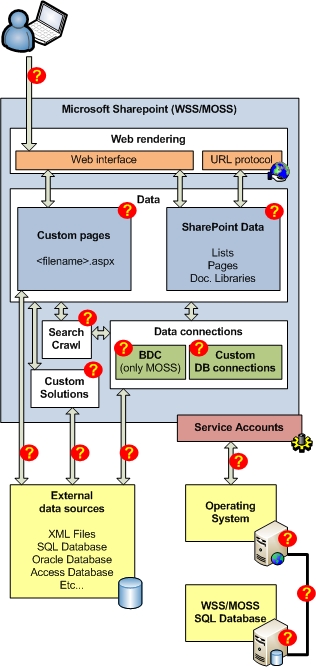
Figure 2
Notice the question marks? These are places where different security levels need to be set. We will begin explaining some review from the top of this diagram.
- When a user accesses SharePoint intranet:
- What type of evaluation must be used?
- Should traffic be encrypted using SSL?
- SharePoint data created by lists, pages and document libraries.
Should access to some or all of them be restricted according to different levels?
No Access
Readers
Publishers / Editors
Administrators
Are site administrators or SharePoint Service Providers (SSP)?
- Customizable pages may contain configured data connections.
- Make sure the terms are set on the pages or files.
- Customized solutions can include access codes in many areas.
- Choose to install only the solutions you trust.
- Select the appropriate security level when installing the solution.
- How to search
The default content account has the right to read all web applications in the system.
Read access configuration for the following components:
- SharePoint sites outside the server system
- Enterprise data category applications
- Website
- Shared files
- Public folders of Microsoft Exchange Server
- The note
- Access to BDC data
- Choose the right level of access security for users to ensure that important information is not disclosed to everyone.
- Choose the right assessment method for BDC connection.
- If you configure search methods, consider accessing the searched data.
- Customized database connections can be made by designers.
- Ensure that connections are only available to employees who need this information.
- External data sources
- Do data connections use other important information?
- Are important certificates used more accessible than necessary?
- Use the authentication method Pass-through / Single Sign-On (one-time login) if possible.
- If RevertToSelf is used, remember that this option will use the Application Pool account to access the data source.
- Service accounts
- Use only the minimum privileges for service accounts.
- WSS / MOSS servers
- Make sure the server has an antivirus program for operating systems and SharePoint.
- Fix server errors with security patches as needed.
- Use a firewall to limit the risk of attack.
- Protect the physical server.
- Keep secret for non-administrators.
- MOSS SQL database server
- Guaranteed server for anti-virus capabilities for operating systems and SharePoint.
- Fix server errors with security patches as needed.
- Use a firewall to limit the risk of attack.
- Protect the physical server.
- Use SQL alias and non-standard ports for communications - especially if DMZ is used.
- Network communication
- Encrypt communication between servers if possible
Use the image and list above to check the 'health' status of the intranet and discuss the decisions made for your SharePoint system. This is not a complete list but you can consider it as a guide to secure your server system.
Conclude
In this article, I have explained why the need to control data access and which scenarios to avoid. There is also an introduction to how to identify security vulnerabilities and security considerations on specific parts of a SharePoint intranet.