Advanced Twitter account security guide
Surely you used your phone number to authenticate two Twitter accounts. However, if you want to really secure your account, you should consider creating an application-specific password.
This job is extremely simple, you just need a computer, a mobile phone and a third-party authentication application.
Some typical applications:
- Duo Mobile
- Google Authenticator
- Authy
The reason why you should do this is because it's safer. Validating Twitter 2 elements by SMS can be attacked when someone hijackes your mobile account. (For example, an attacker may require a new SIM for your account from a service agent). Meanwhile authentication by application is more difficult to attack even when you change phone numbers or lose access to the device.
How to set up the validator using a third-party application to create an application-specific password
1. From your computer, click the profile icon.
2. Click Settings and privacy .

3. Click the Review your login verification methods button in Security .
4. Enter the password then click Confirm .

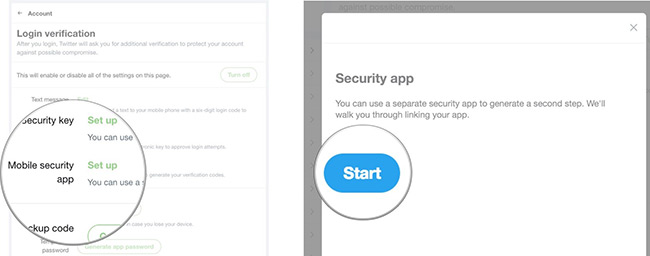
5. Click Set up next to Mobile Security app .
6. Click Start after reading the instructions. You may be asked to verify the password. Otherwise, the QR code will pop up on the screen.
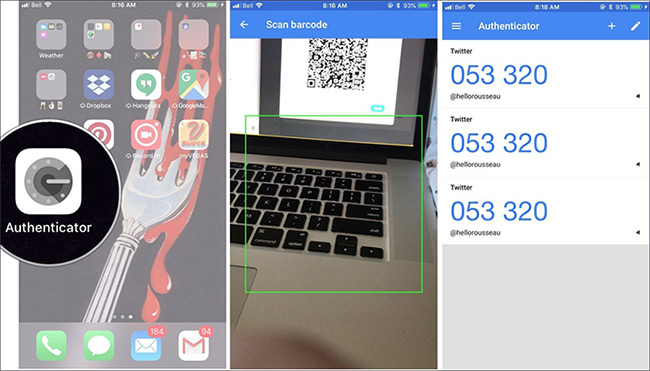
7. Launch the third-party authentication application from the phone.
8. Scan the QR code. You will then see a 6-digit security code appear on the phone screen.
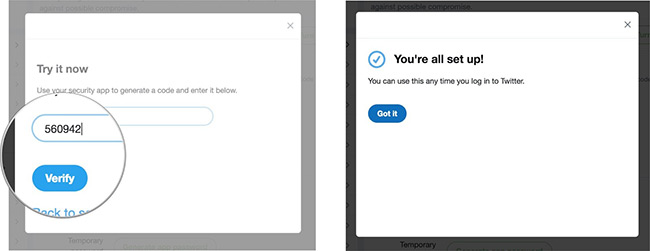
9. Enter this code in the text field in the pop-up window on Mac and click Verify when done.
Now you can use the application to generate verification codes for your Twitter account.
See more:
- Guide to securing 2 layers of Facebook
- Instructions for enabling 2-layer authentication for iCloud on Apple devices
- 2-layer security for Gmail how?
- How to activate 2-step verification of WhatsApp account