The most dangerous hacker groups today
Hacker groups create malware, then take advantage of security holes and attack millions of users and businesses.
In recent years, many new hacker groups have been born, and are considered dangerous. Below are the hacker groups that are considered the most dangerous today.
DarkSide
DarkSide is the group behind the attack that shook the US fuel industry in May, causing the Colonial Pipeline plant's fuel distribution network to be shut down, causing concerns about gasoline shortages.
In August 2020, DarkSide started to gain popularity. The group attacks large companies, causing them to experience problems and disruptions. The group will then demand ransom from the victims. Often such companies pay cyber insurance, so it's even easier for ransomware groups to make money.
DarkSide carries out ransomware attacks, meaning the masterminds often hide their identities to reduce responsibility. After receiving the victim's ransom, they will divide the money between them.
REvil
The REvil ransomware group is currently attracting attention because it is attacking Kaseya. Previously, REvil attacked the world's largest meat processing company JBS. REvil performed strongly in 2020-2021.
In April, REvil stole technical data about unreleased Apple products from Quanta Computer, the Taiwanese company that assembles Apple laptops. The attackers demanded $50 million in ransom to keep the stolen data from being published. It is still unclear whether this amount has been paid or not.
Clop

Clop was founded in 2019. Clop's typical attack method is 'double extortion'. Clop demands a ransom in exchange for a decryption key, restoring access to the stolen data to the victim. However, after that, Clop demanded more ransom so that they would not make the stolen data public.
Historical attacks show that victims who pay a ransom once are more likely to pay again. Therefore, hackers will tend to target the same organization, demanding more ransom each time than the last.
Syrian Electronic Army
Far from a typical ransomware gang, the Syrian Electronic Army has been conducting online attacks since 2011 for political purposes.
The group's attack method is to distribute fake news through reputable sources. In 2013, a fake tweet created by the Syrian Electronic Army appeared on Twitter of the Associated Press, causing billions of dollars to 'fly' from the stock market.
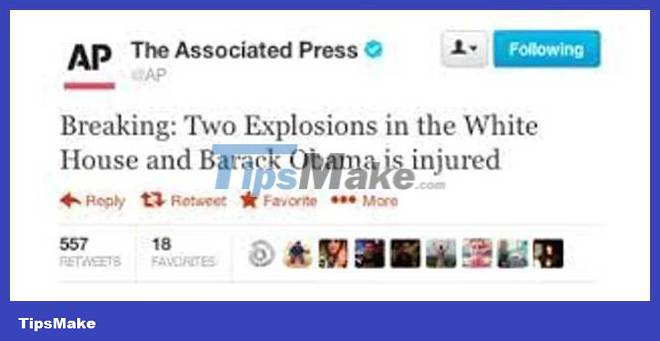
In fact, the Syrian Electronic Army's exploits make most people believe in the fake content they create.
FIN7
If this list had a 'super villain' name, it would be FIN7. FIN7, based in Russia, is said to be the most successful ransomware group of all time. FIN7 has been operating since 2012.
Many of FIN7's attacks went undetected for years. They exploit cross-attack scenarios and steal data for many purposes. For example, FIN7 demands a ransom, while also using the stolen data itself against victims, such as reselling the stolen data to third parties.
In early 2017, FIN7 was accused of being behind an attack targeting companies that provided records to the US Securities and Exchange Commission. This confidential information was exploited and used for ransom, which was then invested on the stock exchange.
Lazarus

This hacker group is believed to have been founded in North Korea in 1998, one of the longest-existing groups. The group's main targets are South Korea and the US.
Lazarus' most famous product is WannaCry Ransomware, which infected more than 200,000 Windows computers and caused $4 billion worth of damage.
Dragonfly
This group, also known as Crouching Yeti, Iron Liberty and Berserk Bear, was born in 2010 and is believed to be based in Russia.
Dragonfly is documented to have attacked infrastructure in North America and Europe, and used spear phishing to carry out attacks on third-party organizations with cyber security levels. lower.
Dragonfly is accused of being behind a DDoS attack using the BlackEnergy trojan targeting multiple electricity companies in Ukraine, causing thousands of people to lose power.
Morpho
Also known as Wild Neutron, Sphinx Moth and Butterfly, no trace of the group has been found so it is impossible to know about the group's origins.
Morpho has carried out attacks through zero-day vulnerabilities and stolen countless information from famous technology companies such as Twitter (X now), Apple, Facebook and Microsoft.
Lapsus$

This hacker group is believed to originate from the UK and was born in 2021. The group's goal is to extort money from organizations and public companies through social network attack techniques.
Lapsus$ recruited members on Telegram and used this channel to post stolen information.
Lapsus$ once attacked the Brazilian Ministry of Health, endangering millions of people receiving Covid-19 vaccines. In addition, this hacker group also attacked famous technology companies such as Microsoft, Samsung, Uber, Rockstar Games, Nvidia and Cisco.
NoName057
This hacker group was born a few years ago and is believed to have originated from Russia. NoNam07's most notable attack was on the Spanish Interior Ministry, causing the agency's website to experience various problems on election day.
You should read it
- ★ Chinese hackers use ransomware as bait to hide cyber espionage
- ★ 10 groups manipulating Chinese Internet virus
- ★ LockBit - The world's most dangerous hacker gang was destroyed
- ★ 17 skills needed to become a hacker
- ★ This is a group of hackers who have successfully hacked Tesla's autopilot system, they hacked Safari on Mac OS in just 20 seconds.