Chinese hackers use ransomware as bait to hide cyber espionage
Threat analysts from Secureworks share that hackers use ransomware in espionage activities to erase their tracks and create a distraction for employees dealing with cybersecurity incidents.
Finally, the theft of business secrets is disguised as extortion attacks.
Strange ransomware campaigns
Two hacking campaigns analyzed by Secureworks are "Bronze Riverside" (conducted by hacker group ATP41) and "Bronze Starlight" (ATP10), both of which use HUI Loader to deploy remote access trojans PlugX, Cobalt Strike and QuasarRAT.
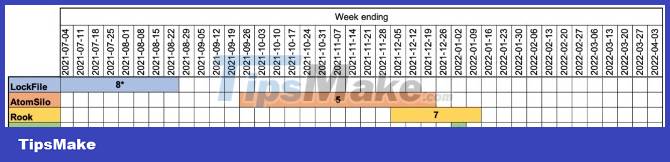
Starting in March 2022, "Bronze Starlight" leveraged Cobalt Strike to deploy ransomware families such as LockFile, AtomSilo, Rook, Night Sky, and Pandora.
In these attacks, hackers use a new version of HUI Loader with the ability to bridge Windows API calls and the ability to disable Event Tracing for Windows (ETW) and Antimalware Scan Interface (AMSI).
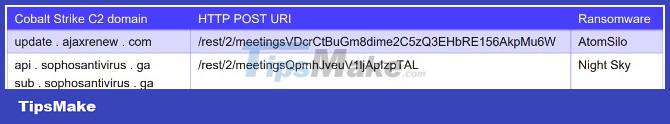
Cobalt Strike configuration for three separate ransomware AtomSilo, Night Sky and Pandora reveals a shared C2 (Command & Control server) address. Also, this year the same source uploaded to the HUI Loader on Virus Total.
The way LockFile, AtomSilo, Rook, Night Sky and Pandora work and victims are very unusual compared to purely financially motivated ransomware campaigns. Often they target a small number of victims for a short time and then suddenly abandon the campaign.
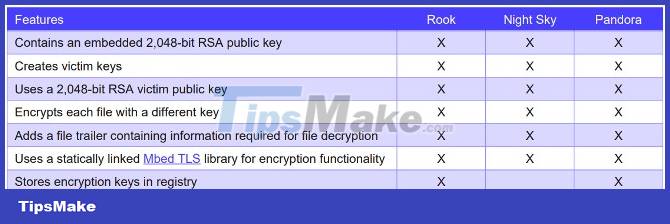
Secureworks also recognizes that there is code duplication between Pandora and the HUI Loader so this loose connection could point to a common pool.
LockFile and AtomSilo also look very similar while Night Sky, Pandora and Rook are all built from Babuk source code and also have many similarities in code.
These 5 ransomware campaigns left no mark on the cybercriminal community and never really became a significant threat. In addition, all of them were soon abandoned.
Therefore, it can be said that "Bronze Starlight" is creating short-lived strains of ransomware to mask cyber espionage activities, disguised as a ransomware attack.
In response, Secureworks recommends that organizations and businesses strengthen their ransomware detection and protection mechanisms. At the same time, when detecting ransomware, organizations and businesses should thoroughly check other aspects in parallel with ransomware removal.
You should read it
- ★ Security researcher identified Sharpshooter spy attacks related to the Korean hacker group
- ★ Vietnam Hacker forum was paralyzed
- ★ Detecting a new ransomware strain, not asking for data ransom, but only needing the victim to join the Hacker's Discord server
- ★ Defeat China's largest hacker training furnace
- ★ The hacker group threatened to spread the network attack tool behind WannaCry