The hacker group threatened to spread the network attack tool behind WannaCry
Shadow Brokers, a hacker group behind the network weapon theft and vulnerability exploiting tool used by the NSA, said it will release the stolen tools monthly. These are the tools that created the global cyberattack called WannaCry,
On an article, the group said it will begin its release in June and those who pay a Subscription will be able to access it. They also added that these are " network data from Russian, Chinese, Iranian or Korean missile programs, rocket launchers, as well as tools to exploit Windows 10 vulnerabilities, handset and data devices. whether stolen from the central bank ".
" In June, TheShadowBrokers announced the service" Discharging TheShadowBrokers data of the Month. "The group will offer a full-cost subscription model. The member wants to do with the data depending on their decision , "the group said.
The group did not give evidence that they had data, so it was probably a lie. They also criticize technology companies for not buying their data.
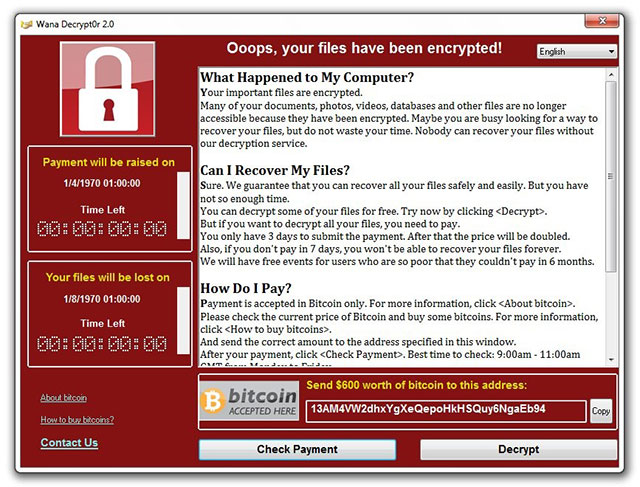
Leakage tool from Shadow Brokers behind the WannaCry attack
In early 2016, Shadow Brokers put the NSA hack tool online. They also spread more and more, including tools to exploit vulnerabilities on Windows machines, after failing to sell them in an online auction.

These tools were then used by a hidden attack group to spread the ransomware WannaCry, stirring up thousands of computers around the world, causing chaos in many large companies. Microsoft had to break the law to release patches for vulnerabilities in Windows, but many un-updated organizations were still exploited. The attack also prompted Microsoft to protest against the US government's use of exploitation tools.
"Attack" anyone, from China to Apple
Journalist Marcy Wheeler said the group's new statement about Windows 10 exploits could be a stressful effort between Microsoft and the US government. " Just threatening to leak another tool after launching two Microsoft exploit tools, Shadow Brokers will make the relationship between Microsoft and the government increasingly stressful ."
Shadow Brokers directly criticized Microsoft director Brad Smith and suspected he had contact with the NSA. They also voiced criticism of those from China and Apple for not buying their tools in the auction at the beginning of the year. " Intelligence agencies Five Eyes, Russia, China, Iran, Korea, Israel, Saudi, United Nations, NATO, no government or country buys it either. Cisco, Juniper, Intel, Microsoft, Symantec, Google, Apple, FireEye and all other security companies, nobody bought it . "
You should read it
- ★ 2 effective and free ways to check WannaCry
- ★ WannaCry remains one of the most dangerous global security threats
- ★ How to remove / fix ransomware WannaCry
- ★ Download and sell Windows patches for all versions to avoid being hit by a massive cyber attack, affecting 150 countries and still spreading
- ★ Prevent WannaCry variants by turning off this Windows 10 installation