Series of DrayTek router models have security holes

Forescout discovered that more than 704,000 DrayTek routers have web user interfaces exposed on the Internet. The majority of affected cases are located in the United States, Vietnam, the Netherlands, Australia.
List of security vulnerabilities on DrayTek routers
Of the 14 new security flaws, two are rated critical, nine are critical, and three are moderate.
| CVE-2024-41592 | Regarding a buffer overflow in the "GetCGI()" function in the web UI, which could lead to denial of service (DoS) or remote code execution (RCE) when processing query string parameters. |
| CVE-2024-41585 (CVSS score: 9.1) | Relates to the case of inserting an operating system (OS) command into the "recvCmd" binary file used for communication between the host and client operating systems. |
| CVE-2024-41589 (CVSS Score: 7.5) | Using the same administrator credentials across the entire system leaves the entire system compromised. |
| CVE-2024-41591 (CVSS Score: 7.5) | Reflected Cross-Site Scripting (XSS) Vulnerability in Web UI |
| CVE-2024-41587 (CVSS Score: 4.9) | Stored XSS vulnerability in web UI when configuring custom messages after login |
| CVE-2024-41583 (CVSS Score: 4.9) | Stored XSS vulnerability in web UI when configuring custom router names to display to users |
| CVE-2024-41584 (CVSS Score: 4.9) | Reflected XSS vulnerability in web UI login page |
| CVE-2024-41588 (CVSS Score: 7.2) | Buffer overflow vulnerability in web UI CGI pages /cgi-bin/v2x00.cgi and /cgi-bin/cgiwcg.cgi leads to DoS or RCE |
| CVE-2024-41590 (CVSS Score: 7.2) | Buffer overflow vulnerability in CGI pages of web UI leads to DoS or RCE |
| CVE-2024-41586 (CVSS Score: 7.2) | Stack overflow vulnerability in /cgi-bin/ipfedr.cgi page of web UI leads to DoS or RCE |
| CVE-2024-41596 (CVSS Score: 7.2) | Multiple buffer overflow vulnerabilities in web UI lead to DoS or RCE |
| CVE-2024-41593 (CVSS Score: 7.2) | Heap-based buffer overflow vulnerability in ft_payloads_dns() function of web UI leads to DoS |
| CVE-2024-41595 (CVSS Score: 7.2) | Out-of-bounds write vulnerability in web user interface leads to DoS or RCE |
| CVE-2024-41594 (CVSS Score: 7.6) | An information disclosure vulnerability exists in the web server backend for the web user interface, which could allow an attacker to perform an adversary-in-the-middle attack. |
How to fix security holes on DrayTek routers
After receiving the report, DrayTek released patches for multiple router models to address the 14 vulnerabilities.
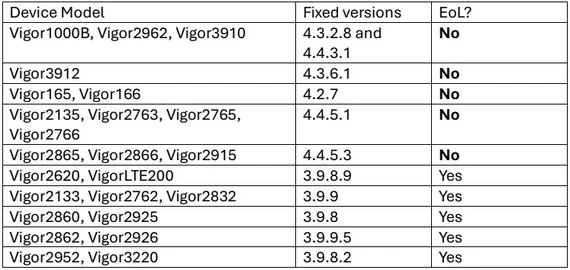
In addition to applying the latest software update, to fix security vulnerabilities on DrayTek routers users are recommended to perform the following actions:
- Disable remote access if not needed.
- Use access control lists.
- Use two-factor authentication when active.
- Check settings for arbitrary changes or added admin users.
- Disable SSL VPN connections over port 443.
- Enable syslog logging to monitor for suspicious events.
- Enable automatic upgrades to HTTPs pages on your web browser.
You should read it
- Warning: Jenkins exists a serious security hole that helps hackers gain control of computers of many Vietnamese businesses
- Skype blocked the security hole
- Google revealed a critical flaw in Qualcomm's Adreno GPU
- Discover a monster black hole 100,000 times bigger than the Sun, the second largest in the Milky Way
- 10 interesting facts about black holes in the universe (Part 2)
- Not yet released, but iOS 13 has a security hole that bypasses the lock screen
 Are complex passwords 'out of date'?
Are complex passwords 'out of date'? How to share text on Chrome as a link
How to share text on Chrome as a link Instructions for creating PowerPoint background color effects - Create a new background for slides
Instructions for creating PowerPoint background color effects - Create a new background for slides Things You Never Knew About Dragonflies
Things You Never Knew About Dragonflies How do criminals use CAPTCHAs to spread malware?
How do criminals use CAPTCHAs to spread malware? How to turn off OneDrive sync on Windows
How to turn off OneDrive sync on Windows