New variant of ransomware Arena Crysis appeared
Researcher Michael Gillespie has discovered a new variant of ransomware Crysis / Dharma that adds the .arena extension to the encrypted file. It is not known exactly how this variant was distributed but before, Crysis was spread by hacking Remote Desktop Services and manually installing ransomware.
When installed, it scans the computer for certain types of files and encrypts them. When encrypting the file, it will add the extension in .id- [id]. [Email] .arena format. For example, a file named test.jpg will be encrypted and renamed to test.jpg.id-BCBEF350. [Chivas@aolonline.top] .arena.
Remember that this ransomware will encrypt the network drive mapped (map) and the shared network has not been mapped. So make sure you have the shared network locked so that those who really need access have the right.
Below is an example of an encrypted directory.

The folder with the files has been encrypted by Crysis
The file is encrypted with the variant of Crysis Arena Ransomware
When encrypting the file, it will also remove all copies, so you cannot restore it. It will delete them by running vssadmin delete shadows / all / quiet.
The Crysis Arena variant will also create 2 more extortion notes. One is the info.hta file that is run by autorun. And one is a note named FILES ENCRYPTED.txt.
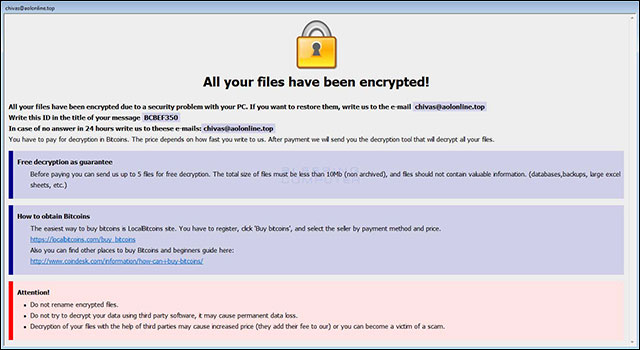
Note on the info.hta file of extortion code
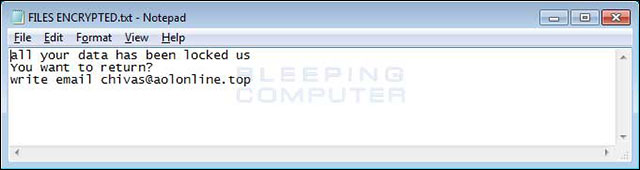
Note on the TXT file
Both of these notes contain instructions to contact chivas@aolonline.top to guide payment.
Finally, the blackmail code will set itself to automatically start when you log into the machine. This allows it to encrypt newly created files since the last execution.
Unable to decode the Crysis Arena extortion code
At this point, the malicious file Crysis Ransomware will not be able to decrypt (without losing money). The only way to recover is to backup or if you are lucky, via Shadow Volume Copies. Although Crysis tries to delete Shadow Volume Copies but in a few cases, it can't do that. Therefore, recovering encrypted files from Shadow Volume Copies is always suggested as the last way to save.
How to protect against Crysis?
To protect yourself from Crysis or any other ransomware, create your own habits of using computers and security software. First, always back up your data with reliable tools to prevent it when needed. Security software that can detect malicious code like Emsisoft Anti-Malware or Malwarebytes may also be useful.
Finally, don't forget to create a habit of keeping safe when using a computer like:
- Data backup.
- Do not open the attachment without knowing who sent it.
- Do not open the attachment until it is confirmed that the person sent it.
- Scan files with virus detection tools like VIrus Total.
- Be sure to update Windows as soon as they are published. Update programs, especially Java, Flash and Adobe Reader. Older programs that contain security vulnerabilities are often exploited, so always use the latest version.
- Be sure to install security software.
- Use passwords that are difficult to guess and do not use the same password for multiple pages.
- If using Remote Desktop Services, do not connect directly to the Internet but connect via VPN.
IOC information about Crysis Arena Ransomware
Hash
ARENA SHA256: a683494fc0d017fd3b4638f8b84caaaac145cc28bc211bd7361723368b4bb21e
Note on file FILES ENCRYPTED.TXT
có dữ liệu bạn đã được khoá US
You want to return?
write email chivas@aolonline.top
Notes on INFO.hta file
Tất cả tập tin bạn đã được xác định!
Tất cả tập tin bạn đã được xác định due to một vấn đề bảo mật với PC. Nếu bạn muốn phục hồi them, ghi vào chúng vào e-mail chivas@aolonline.top
Đang ghi ID này trong danh sách của thông báo của bạn [id]
Trong việc có không có quyền trong 24 thời gian us ghi vào sựese e-mails: chivas@aolonline.top
You have to pay for decryption in Bitcoins. Hãy thay đổi giá trên làm thế nào bạn ghi vào Us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying bạn thể đăng nhập US vào 5 tập tin cho free decryption. Số kích cỡ của tập tin phải là ít hơn 10Mb (không phải được tạo), và tập tin nên không chứa thông tin giá trị. (databases, backups, large excel sheets, etc.)
How to obtain Bitcoins
Easiest way to buy bitcoins is LocalBitcoins site. Bạn cần phải đăng nhập, hãy chọn 'Buy bitcoins',
https://localbitcoins.com/buy_bitcoins
Bạn có thể tìm các địa chỉ khác cần mua Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
Không thể chuyển đổi tập tin tập tin.
Không thử thử decrypt dữ liệu với phần mềm khác, nó có thể có cơ sở dữ liệu loss.
Decryption của tập tin của bạn với trợ giúp 3 bên ngoài có thể tạo giá trong (chúng thêm chúng để chúng) hoặc bạn có thể là một người victim của scam.
You should read it
- Ransomware can encrypt cloud data
- General guidelines for decoding ransomware
- What is Ransomware Task Force (RTF)?
- [Infographic] 7 effective ways to protect businesses from Ransomware
- STOP - Ransomware is the most active in the Internet but rarely talked about
- How to decode ransomware InsaneCrypt (Everbe 1.0)
 Watch out for the risk of spreading the virus from Facebook Messenger on Windows, MacOS and Linux
Watch out for the risk of spreading the virus from Facebook Messenger on Windows, MacOS and Linux WireX DDoS Botnet: tens of thousands of Android phones are hacked
WireX DDoS Botnet: tens of thousands of Android phones are hacked LabVIEW vulnerability allows hackers to attack your computer
LabVIEW vulnerability allows hackers to attack your computer The new Gazer - the back door targets the ministries and embassies around the world
The new Gazer - the back door targets the ministries and embassies around the world A hacker in the United Kingdom found a way to temporarily encrypt the WannaCry malware
A hacker in the United Kingdom found a way to temporarily encrypt the WannaCry malware Warning with 4 dangerous variants of WannaCry malware
Warning with 4 dangerous variants of WannaCry malware