Large vulnerabilities in iOS 12 allow hackers to access images and contacts when the iPhone is locked with a call
On iOS 12, there is a vulnerability that allows hackers to access the folder of images and contacts on the locked iPhone.
The amazing thing is that this vulnerability was discovered by a taxi driver while he was waiting for the customer. And Jose Rodriguez, who discovered iOS flaws in the past to Apple fix, shared a method to overcome this rather complex code in a video.
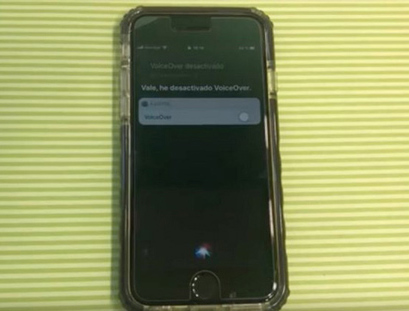
Attack operations
When physically accessing the locked iPhone, the attacker will cause the device to enter sleep mode by asking Siri to activate VoiceOver with the side button (Side Button) and using another device to call the iPhone. When the phone receive screen appears, touch the Message -> button and choose to create a custom message -> touch the plus (+) icon at the top right.
Next, the attacker uses another phone to send a text message or iMessage to the iPhone. When the iPhone receives the message, its screen will be double-tapped and the plus sign below will light up.
After a short period of time, the screen turns white and the message disappears. But an attacker can use VoiceOver's text selection box, which is still accessible to access the Messages interface. Swipe the screen multiple times so that VoiceOver displays Cancel and the initial Messages screen.
When adding a new recipient to the message section and selecting a number from the virtual keyboard, the call history and contact list will appear.
For contacts with the info (i) button displayed, the attacker can even view the contact's information by turning off VoiceOver and touching the (i) button. When performing 3D Touch operation on contacts, call options, messages, Add to Existing Contact (add to current contacts) and Create New Contact (create new contacts) will appear.
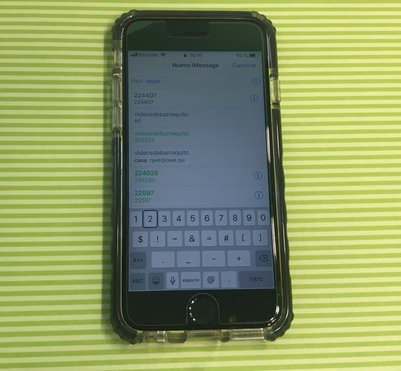
An attacker can add profile pictures to contacts by performing complex operations like the one related to the invisible user menu to access Camera Roll and other folders on the locked iPhone. .
The attacker can execute the method over this key on every iPhone, including the newly launched iPhone Xs.
To prevent this vulnerability, users can turn off Siri access from the lock screen by going to Settings -> select Face ID & Passcode (will be Touch ID and Passcode on iPhone with Touch ID support) -> at item " Allow access when locked "Siri off.
See more:
- The time-limited feature on Apple's iOS 12 is hacked by a 7-year-old child
- Errors after upgrading iOS 12 and how to fix it
- 5 security settings to do right on iOS 12
You should read it
- On iOS 12.3 iPhone Lock cannot change the ICCID code directly on the phone and this is a fix
- How to lock Zalo, set a password for Zalo to secure the message
- Easily bypass the iPhone's authenticity thanks to the vulnerability on iOS 11
- Forgot the TV PIN to get back?
- GitHub's machine learning tool can detect vulnerabilities in code
- iPhone Lock suddenly revived after nearly 1 year of 'covering projection'
 Hackers claim how good it is to hack Mark Zuckerberg's Facebook account?
Hackers claim how good it is to hack Mark Zuckerberg's Facebook account? The mystery of the strange game appeared on Google.com without anyone knowing the author or time appeared
The mystery of the strange game appeared on Google.com without anyone knowing the author or time appeared Opera Lab, the desktop browser that supports the Ethereum blockchain
Opera Lab, the desktop browser that supports the Ethereum blockchain A bug hunter's job, emerging job in the technological age
A bug hunter's job, emerging job in the technological age There is an official version of Opera Touch for iPhone, download and experience
There is an official version of Opera Touch for iPhone, download and experience FBI unlocked iPhone of suspects using FaceID
FBI unlocked iPhone of suspects using FaceID