Keyloggers ... 'evil religion'
In the final period of this keylogger topic, we present the features of some keylogger programs of "evil religion" ie keyloggers in the most dangerous form today.
Keylogger "evil religion" is considered the supreme development step of the "karma" keyloggers. In addition to being full of features such as "hegemonic" keyloggers, "evil" keyloggers are also keyloggers equipped with a malicious program, often a dangerous Trojan capable of sending all Information collected by keyloggers is returned to its owner. Here are 5 popular "deviant" keylogger programs today.
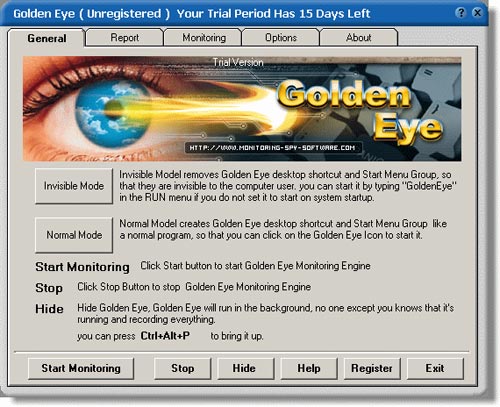
1. Golden Eye : Default setting in folder C: Program FilesA8GsdsApp ; The executable file is named AGSeiApp.exe ; Record keyboard information in HTML format, take screenshots in JPG format and contain stolen information in the ' Output ' folder located in the program installation directory; Use ALT + CTRL + SHIFT + P hotkey combination to hide or activate. In the installation directory of this keylogger, there is a file named kbhook.dll that contains a trojan named Generic.MRA capable of sending recorded information back to secret servers. This is one of the keyloggers that has features designed at the most detailed level available today.
2. Perfect Keylogger : Default installation in folder C: Program FilesBPK ; The executable file is named bpk.com ; Contains a dangerous trojan named PS.Banker.25.S located in the file named Inst.bin . When installed, this keylogger will try to put this trojan in the folder ' Temp ', located very deep in the ' Documents and Settings ' folder . This trojan records e-financial transaction passwords online to send to its owner. When the PS.Banker.25.S trojan is infected with the 'death' antivirus program, this keylogger tool is no longer working.
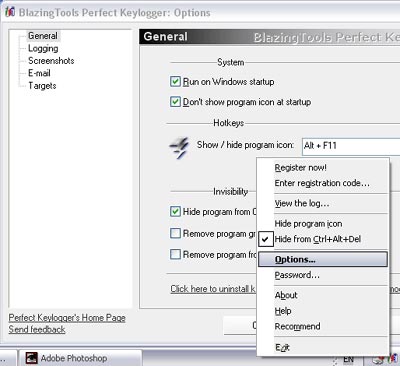
The user interface of Perfect Keylogger
3. Spy Recon : Follow other songs:
The 'righteous' keyloggers
The keyloggers ' publish ' in the default directory are C: Program FilesSpy Recon - Platinum ; The executable file is named svrsrn.exe ; Contains files that record the operation of the device as TXT in the ' Logs ' folder located in the installation directory; This keylogger contains a trojan called Trojan.Spy.Spyrecon.A hidden in cbt.dll file that can send all stolen information to an e-mail as well as send information directly to Its owner.
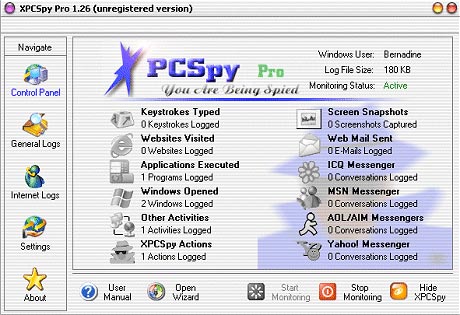
4. XPCSpy Pro : Default setting in the folder C: Program FilesXsoftware ; The executable file is called XPCSpyPro.exe ; Contains the screen capture file as a XSM file in the ' Screenshots ' folder located in the installation folder. This form of XSM file is actually JPG but this keylogger has been disguised as XSM; Note that keyboard operation in TXT file format and contained in the folder named ' Report ' is also located in the installation directory. This keylogger launches into a trojan computer called Trojan.Spy.Delf.DU , hidden in a file named systemout.exe and located in the WindowsSystem32 directory; Being able to send the recorded results to a certain e-mail address, and secretly send a copy to the author designed the trojan.
5. Fingerprints : the default installation directory is C: Fingerprints ; Once installed, Fingerprints will immediately launch a Trojan named Trojan.Spy.Agent.JF hidden in keyhooi.dll file into the Windows system32 directory; This keylogger will save its keyboard activity log file as a FLF file in the installation directory that can be viewed with NotePad; When the computer is networked, the trojan will secretly send the resulting FLF files to its owner.
HOANG HAI