Honda's database leaked, revealing many 'deadly' weaknesses in the intranet system
The publicly accessible ElasticSearch database has revealed a huge information store related to the giant automaker's global intranet, showing potential security holes in the The database as well as the 'fragile' code system of this reputable corporation can be abused by potential attackers.
Huge data warehouses posted on ElasticSearch contain about 134 million documents with the amount of information equivalent to 40GB, involving more than 300,000 Honda employees worldwide.
- Hacker took control of the London Police Department website, posting "unacceptable" content.
 The leaked database contains 134 million internal documents of Honda
The leaked database contains 134 million internal documents of Honda
"The information available in this database looks like an internal repository, containing information regarding production lines, customer data, and especially employee information. Honda around the world It is also necessary to mention some other important information such as host name, MAC address, internal IP, operating system version, patched version and software status. security of the end point of all the devices operating in this Japanese car manufacturer's network, 'said Justin Paine, security researcher who discovered an unusual data warehouse.
- What is email encryption? Why does it play an important role in email security?
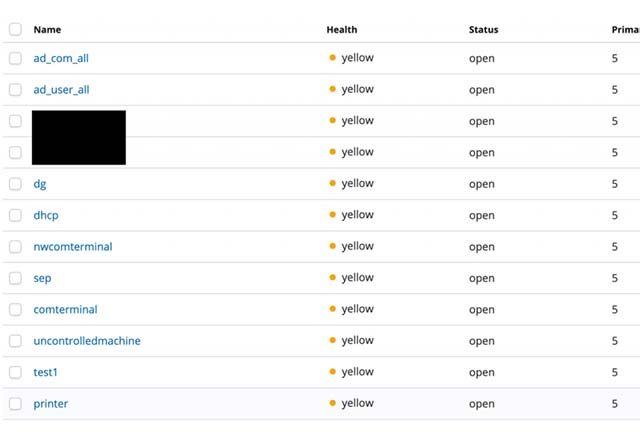
List of data disclosed
The data was revealed
The unsecured ElasticSearch database has revealed a huge amount of very specific information about hundreds of thousands of Honda employees, such as their name, email, last login, as well as information about the provider's network. security system endpoint, operating system, operating system version, server name and security patch status.
Not only that, there are about 3,000 data points stored in a statistics table called "unrollrollmachine", which contains a list of computers on Honda's intranet that do not use security software. End point - Fatty bait for cyber criminals.
"If the attackers are trying to hack into Honda's network to access the 'unrollrollmachine' list, they will be aware of what devices in the network are less likely to identify / block. Their attacks, in turn, suggest an attack on computers that do not use endpoint security software in the system, which is an open door for hackers to infiltrate the internal system of Honda, a cybersecurity disaster will be a consequence of the money, 'added Justin Paine.
- ProFTPD remote code execution vulnerability affects more than 1 million servers worldwide
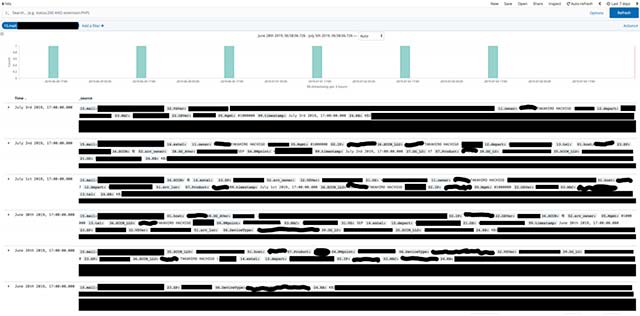 Important information regarding the CEO of Honda has also leaked
Important information regarding the CEO of Honda has also leaked
More dangerous, this database also contains data on computer systems used by senior company figures, such as CFOs, CSOs and CEOs, to department heads and directors. subsidiary companies, which can allow attackers to easily find and access disclosed information and use them in attacks targeting senior positions in the business.
In the above example, many important information regarding the CEO of Honda has been exposed, such as his full name, account name, email and his last login date. Along with that is the "MAC address of the computer the CEO is using, information about the applied Windows KB / patch, operating system, operating system version, endpoint security status, IP and type of device".
- Detects many security vulnerabilities in Lenovo server infrastructure
The database was revealed in 6 consecutive days
After Justin Paine analyzed the database activity for a 30-day period, the security expert discovered that the data was being updated every day, with about 40,000 new entries containing employee information. Honda is working at factories and offices around the world, along with the network, security and current operating system status of the computers they are using.
Honda's leaked database of information equivalent to about 3 months of the company's operations (starting March 13) was found by Justin Paine on July 1. And after a few days of trying seeking to contact individuals responsible for managing Honda's confidential information to inform their findings, Justin Paine finally made contact with the car company's security team. Japan on the morning of July 6 last. Thus, this database has been left open for about 6 consecutive days.
- Overview of building enterprise security detection and response system
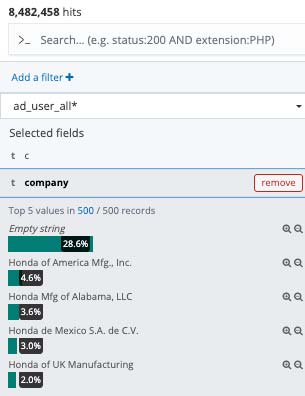 The list of Honda's subsidiaries is found in the leaked data base
The list of Honda's subsidiaries is found in the leaked data base
After receiving information from Justin Paine, Honda's security team immediately gave the system maintenance for about 10 consecutive hours, and sent a thank you note to this security researcher for providing them. Information about vulnerable databases, part of the letter content is as follows:
'Honda would like to express my deepest thanks to you for finding and providing information about security holes in our system. The security issue he pointed out could potentially allow external malicious agents to gain unauthorized access to some of Honda's cloud-based data, including many personal-related information. Our members as well as active devices in the network. We investigated the system access log and did not find any download sign of a third party data. At the present time, there is no evidence that data is leaked, except for screenshots sent by him. In the future, we will implement appropriate plans in accordance with relevant laws and regulations, and will continue to implement proactive security measures to prevent similar incidents in the future. Thanks again for your contribution! '
- Hacker successfully stole 100,000 photos from border control database
 Honda sent a thank you note to Justin Paine and immediately started to fix the problem
Honda sent a thank you note to Justin Paine and immediately started to fix the problem
'I guarantee that I will not name the main end-point security service provider, responsible for protecting Honda's machines, but the leaked data clearly shows the information about the security service provider as well as Any device in the system that owns endpoint security software is turned on and updated. What makes this database particularly dangerous if it falls into the hands of hackers is that it can accurately indicate the location of weaknesses in the Honda intranet system, 'concluded Justin Paine.
You should read it
- ★ Learn about terminal security (endpoint security)
- ★ Insider attacks are becoming more and more popular and difficult to detect
- ★ Detected the archive containing data of thousands of Zoom accounts on the dark web forum
- ★ Data of more than 20 million Taiwanese citizens leaked on the dark web
- ★ Awareness and experience - the most important factor in every network security process