Google launches Backstory - New network security tool for businesses
Today, March 7, Google's one-year-old network security co-operation organization, Chronicle, officially announced its first commercial product, called Backstory, a security threat analysis platform. Cloud-based enterprise-level encryption, designed to help companies quickly investigate incidents, identify vulnerabilities, and detect potential threats.
In fact, the network infrastructure in most businesses regularly generates a large amount of data and daily logs, and it can become a useful information channel in determining as well as Find out the exact issues involved when security incidents occur.

- Google introduced Coral, the platform that supports building AI IoT hardware integration
Unfortunately, most businesses are unable to collect the necessary data on their own, or even if they do, they will not, in other words. there is not enough facility and ability to store that data for more than 1 or 2 weeks. That is why security analysts are always in a state of 'blind information' because they do not have the necessary data for analysis when a security incident occurred before.
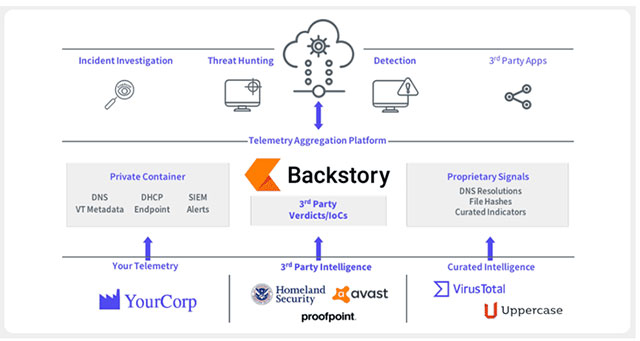
Backstory was created to neatly solve this problem, by allowing organizations and businesses to upload and store their "remote local security data" in a completely private way on a cloud platform. of Google, and take advantage of advanced data analysis and machine learning technologies to effectively monitor and analyze the detection and investigation of any potential threats. The Chronicle team said in a blog post as follows:
'Backstory will help normalize, index and correlate data, word itself and, at the same time, rely on third-party threat signals to monitor and provide instant analysis and related context. to risk activities. With Backstory, in less than a second, analysts can get information about every device running on the company's network, or contact any domain or IP address. '

- Chrome has a new Zero-Day vulnerability, allowing hackers to execute code remotely
Like SIEM solutions, Backstory will convert log data, such as DNS traffic, NetFlow, endpoint logs, proxy logs, etc. into meaningful information that can be searched and retrieved. used to help companies better understand the digital threats as well as online attacks aimed at them. This information is provided on a large scale, 'bringing a more complete picture of the threat panorama'.
In addition, Backstory also compares collected "intelligence-threat intelligence" data from various partners and sources, including VirusTotal, Avast, Proofpoint and Carbon Black, both here and there. are organizations owned by Alphabet Group.
"Backstory compares corporate network activity with a constant stream of intelligence, threat-related, and managed from a variety of sources, in order to detect potential threats immediately. In addition, the tool will also continuously compare any new pieces of information against business activity, thereby informing businesses of any historic access to names. Bad web domains, files infected with malware and many other threats, "the Chronicle team shared.
- Google and DeepMind apply AI to predict the output of wind farms
In addition, because Chronicle wants customers to collect and upload as much data as possible, Backstory will not be priced based on the volume of customer data, but instead, Chronicle will sell the license. based on company size:
"Building a system that can be analyzed remotely will not be useful if the amount of upload information is limited. Usually, suppliers will charge customers based on the amount of information they process. I think this is unreasonable because businesses tend to generate more data each year, if charged based on this, the bill for the security of companies will continue to increase, But it can't help them be safer. "
In a related move, Microsoft recently launched two similar security analysis services, called Threat Hunter and Azure Sentinel, and was called by Microsoft "the first localized SIEM in a cloud platform." Great, "to help companies detect, prevent and deal with threats on their networks.

- Google launched TensorFlow Lite 1.0 for mobile devices and embedded devices
Splunk, another company that also provides security analytics products, has seen its stock value drop 5% at the time of market closure · the door on Monday after Google announced its will officially launch Backstory service.