Facebook Ads Manager becomes a victim of Trojan information theft
An unknown hacker group is distributing a Trojan stealing information disguised as a PDF reader that can copy Facebook session cookies as well as sensitive data from the Facebook Ads Manager. .
In particular, on November 30, MalwareHunterTeam found many websites distributing fake PDF editing program called 'PDFreader'. Executables distributed from this site are signed by a digital certificate issued by Sectigo for "Rakete Contenticineh".

VirusTotal then took over and identified this Trojan as Socelars, however it possessed some similarities with other Trojans, such as AdKoob and Stresspaint, in attempting to extract and steal Facebook data from Many different URLs. However, according to Vitali Kremez, the security expert who is responsible for analyzing this Trojan, there is not much similarity in code between this Socelars and other Trojans, so it can be confirmed that this is a specially developed Trojan. instead of upgrading from known Trojans.

Target Facebook Ads Manager
First, Socelars will attempt to steal Facebook cookie sessions from Chrome and Firefox by accessing the SQLite Cookies database. After the cookie is successfully retrieved, it will be used to connect various Facebook URLs where the information is extracted.
https://www.facebook.com/bookmarks/pages?ref_type=logout_gear
https://secure.facebook.com/settings
https://secure.facebook.com/ads/manager/account_settings/account_billing/
The account_billing URL will be used to extract the user's account and access_token, which will then be used in the Facebook Graph API call to steal data from the user's Ads Manager settings.
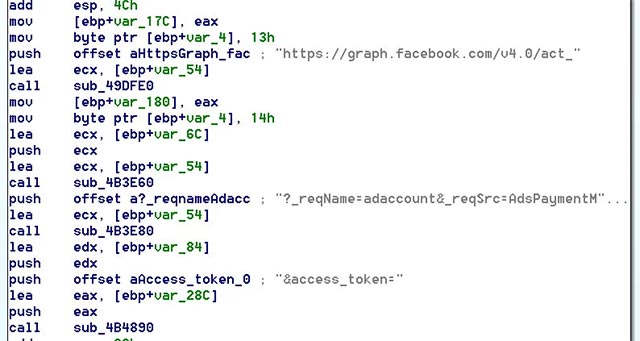
The call to the Facebook Graph API is as follows:
https://graph.facebook.com/v4.0/act_{account_id}?_reqName=adaccount&_reqSrc=AdsPaymentMethodsDataLoader&fields=%5B%22all_payment_methods%7Bpayment_method_altpays%7Baccount_id%2Ccountry%2Cc 7D% 2Cpm_credit_card% 7Baccount_id% 2Ccredential_id% 2Ccredit_card_address% 2Ccredit_card_type% 2Cdisplay_string% 2Cexp_month% 2Cexp_year% 2Cfirst_name% 2Cis_verified% 2Clast_name% 2Cmiddle_name% 2Ctime_created% 2Cneed_3ds_authorization% 2Callow_manual_3ds_authorization% 2Csupports_recurring_in_india% 7D% 2Cpayment_method_direct_debits% 7Baccount_id% 2Caddress% 2Ccan_verify% 2Ccredential_id% 2Cdisplay_string% 2Cfirst_name% 2Cis_awaiting% 2Cis_pending% 2Clast_name% 2Cmiddle_name% 2Cstatus% 2Ctime_created% 7D% 2Cpayment_method_extended_credits% 7Baccount_id% 2Cbalance% 2Ccredential_id% 2Cmax_balance% 2Ctype% 2Cpartitioned_from% 2Csequential_liability_amount% 7D% 2Cpayment_method_paypal% 7Baccount_id% 2Ccredential_id% 2Cemail_address% 2Ctime_created% 7D % 2Cpayment_method_stored_balances% 7Baccount_id% 2Cbalance% 2Ccredential_id% 2Ctotal_fundings% 7D% 2Cpayment_method_tokens% 7Baccount_id% 2Ccredential_id% 2Ccurrent_balance% 2Coriginal_balance% 2Ctime_created% 2Ctime_expire% 2Ctype% 7D% 7D% 22% 5D & include_headers = false & locale = it_IT & method = get & pretty = 0 & suppress_http_code = 1
Data that can be stolen includes session cookies, access tokens, account ids, promotional email addresses, related pages, credit card information (numbers, expiration dates), PayPal emails, balances. advertisements, spending limits, etc., are then compiled and sent to the attacker's Command & Control (C2) server.
More seriously, attackers can use these stolen Facebook cookies to access their accounts and use them to create their own malicious advertising campaigns.
This Trojan is silently executed and performs all its actions in the background, so users will not know that they have become victims of malicious code. Facebook has not yet commented on the incident.
You should read it
- ★ Malware can steal Facebook, Twitter and Gmail accounts
- ★ How to get Cookies and Facebook Token simple
- ★ It turns out Facebook has collected SMS and call information for Android users for years now
- ★ Instructions to block Facebook read theft messages on Android
- ★ Facebook wants to set up a wide area free Wi-Fi network