Vulnerability on macOS helps hackers easily overcome security barriers
To protect users, software developers often warn them with dialogs that appear to confirm whether you want to perform a certain task. This protection method prevents malicious applications from being able to access and control with a wrong click of the user.
However, the MacOS security expert and a former white-hat hacker of the US National Security Agency have found a way to overcome these types of user alerts. The hacker discovered that the macOS interface allows converting keystrokes into mouse operations. Even when a user performs a double-click operation, macOS will recognize that as the command to click the OK button.
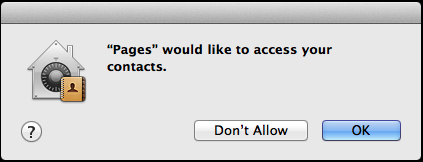
Warning occurs when suspicious software wants to access user information.
And just write a few more simple lines of code, your malware can bypass the user warning dialog and get access to geographic location, contact list and more without verification .
Hacker can only take advantage of this vulnerability to bypass the warning request verification and click OK but cannot break the user's password.

However, this finding also shows that the most basic protection mechanism can be cracked easily and manufacturers need to further enhance the security elements of the operating system.
The vulnerability can be fixed in the next macOS Mojave update.
See more:
- Foreshadow - the fifth most serious security hole in the CPU in 2018
- Millions of Android devices stick with security holes in firmware, hackers can exploit to lock users' machines
- iPhone and Android smartphone series stick with serious Bluetooth security error
- Hackers took control of 18,000 Huawei router devices in just one day