Security with ICT Infrastructure in Vietnam: Security overview - Part I
Lesson 1 - Security Overview
Today INTERNET - a technology that completely changes people's lives, brings many benefits but under the eyes of TipsMake.com, Network Security experts are clearly INTERNET with many potential threats.

The network has become popular and spread to every corner. This common terminology is the default term that refers to Computer Networks. People benefit from this technology, so the whole world can exploit it. Of course, many bad guys will also conspire and know how to hang on the very lucrative bait.
The concept of SECURITY is formed. The Security issue becomes urgent. If you notice that most of the SECURITY network or system are attached to INTERNET, it is impossible not to ignore this problem in the local computer network. The set has had a lot of problems to say, but in this article I don't want to go into it
Normally Model SECURITY will have 12 Components with 12 corresponding products to help a company with ICT infrastructure work well and effectively:
1.Bandwidth management
2.Desktop Security
3.Email/Spam Protection
4.Firewall
5.Wireless Security
6.Gateway Security
7.Invasion Detection and Protection
8.Internet Reporting
9.Log Correlation and Analysis
10.URL Filtering
11.Network Identity
12.Vulnerability Management
It can be said that this division is not completely covered, but it has been classified by the world's leading security companies such as nFORCE, eTrust, CA, .
The following model can show the full set of these products
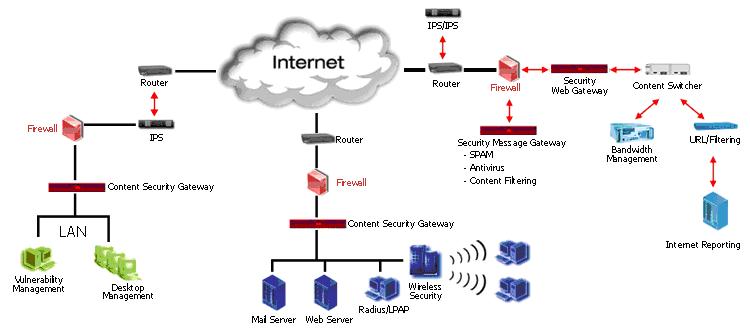
Through the above model, we see that each component has a different effect, but all are compatible and effective sensor operation on the POLICY of the administrator.
So with any model - to protect your network, the Administrator needs to ensure that all the above components can say that his network is safe at least until the moment at the current technology cycle (technologies that can be developed on ICT in the world today)
Bandwith Management - Bandwith Management - It's easy to understand when someone doesn't feel annoyed when the network is as slow as a tortoise. But no one cares about why. Only the Administrator manages all day. If the good knowledge they can easily recognize this may be the cause of some 'bandwidth overflow' attacks that cause stagnation and congestion on the network traffic. Administrators in this work such as GJPSoft, Solarwin, Bandwith monitor . these software can control the packets on the moving network, . Of course, if the combination of specialized devices can be detected The starting point of the stranger causes this trouble .!
Desktop Security - Probably every user is bored when he has to worry about protecting his machine before the uninvited people. Of course, the software will protect the computer on the occasion of producing series and palanquin channels when pointing have enough money to invite it to protect themselves. A simple reason is that the security software comes with operating systems of Microsoft, Linux, etc., are not enough, or roughly done. let yes
Referring to the topic EMAIL / SPAM : There is nothing to say that Mailserver but not blocking it is miserable . (User), all kinds of spam are flooding the world, good, bad, innocent , malicious . there is enough.The most common type is Advertising letter - heaven . just plain looking for selling products only. make hundreds of bad guys cry .!SPAM Protection - a job worth caring about
What about FIREWALL - firewalls . Does everything burn?Usually it burns even the smart ones. The higher the technology Firewall devices, the more difficult it is to configure. But the change will be smarter to know where the enemy is. In Vietnam products are secreted to PIX, . of CISCO, Netscreen Firewall / VPN, . of Juniper, and products of Checkpoint .
What about Wireless Security, Gateway Security . From the Administrators' names, what it is. But what is known about security is that it is still SSID, PKI, Frequency and working standards, etc. with Wireless. As for Gateway Security, most of the big guys like Symantec are well-known and reputed to compete in this market: Its most important job is to analyze and self-study malicious threats from the internet while still need to simplify administration. URL Filtering !A small lane of Gateway Security, however, has been separated to show that it is necessary to control malicious links, which is an important part of the INTERNET era.
Invasion Detection and Protection, .Internet Reporting, Log Correlation and Analysis: In the standard of a Management System.The work of error control, error detection and private protection, report writing, data analysis, . Is one of the extremely important things. It is like the captain of a submarine, only 1 link Arguments, wrong judgment will lead to unfortunate consequences
Network Identity: in the world of Infoblox (www.infobox.com) is one of the leading application developers of this network identifier technology. Controlling most of the potential and shortcomings of the network through it precise control is the main task of Infobox products,. This is a typical company for this part
Vulnerability Management : This concept is ambiguous, but IT people will have to understand that it is similar to how to choose the route with the lowest price and the most optimal. We still have not found the concept of Vietnamese for this component, we are temporarily understand that it is the management but the damage caused by poor security, thereby having specific strategies to overcome .! It is possible to cover the concept of Network Identity, Invasion Detection and protection in its entirety because the ultimate goal of this component is to build a perfect Policy for ICT infrastructure based on existing defects.
Usually the major security firms in the world offer their own products and technologies that cover all of these components in order to compete in the security technology market.
Big companies are present in Vietnam through representatives and exclusive agents such as Cisco System, Triend Micro, RSA Security, Nokia, Tripwire, Checkpoint . Currently many new companies are emerging to be trusted. in Europe and Asia region with these markets such as, nForceSecure System, CP Secure, Fijian Software, .
Security market in Vietnam is entering the transition period when the basic communication infrastructure has formed clearly, the need to use more and more devices of the digital age . The time has come. need to correct and refine your System, If not secure, we will lose many things .!
Continue…
Lesson 2: Bandwidth Management
SecureVN
Please donate to the article: Phan Thai Binh (Mr.) - Email:BinhPT@nForceSecure.com
Share by
Samuel Daniel
Update 26 May 2019
You should read it
- ★ The best network configuration management tools and software
- ★ The basic steps in dealing with network security issues that you need to understand
- ★ Remote UPS management via network
- ★ 9 misconceptions about security and how to resolve
- ★ What is Deep Packet Inspection (DPI)? How does it work and how does it work in network security?