REvil ransomware gang sites mysteriously stop working ngừng
The REvil ransomware group, aka Sodinokibi, uses a variety of clean and dark web sites to negotiate ransoms, share stolen data, and serve as backend infrastructure.
Starting last night, the websites and infrastructure owned by the REvil ransomware group mysteriously stopped working.
"In a word, their onion website is offline or disabled. To be sure, you need to contact the administrator of this site," - BleepingComputer quoted Al Smith of the Tor Project.
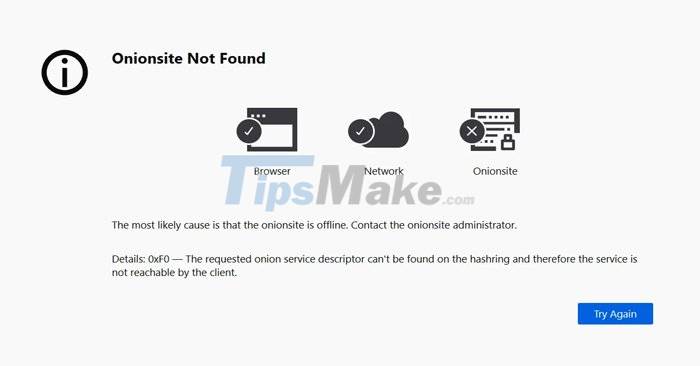 REvil ransomware gang sites mysteriously stop working ngừng Picture 1
REvil ransomware gang sites mysteriously stop working ngừng Picture 1
While it's not uncommon for REvil's websites to lose connection for a while, it's unusual for all of them to go down altogether.
Furthermore, the fact that the decoder[.]re clean site is not responding to DNS queries indicates that the DNS records for the domain have been affected or that the DNS infrastructure is disabled.
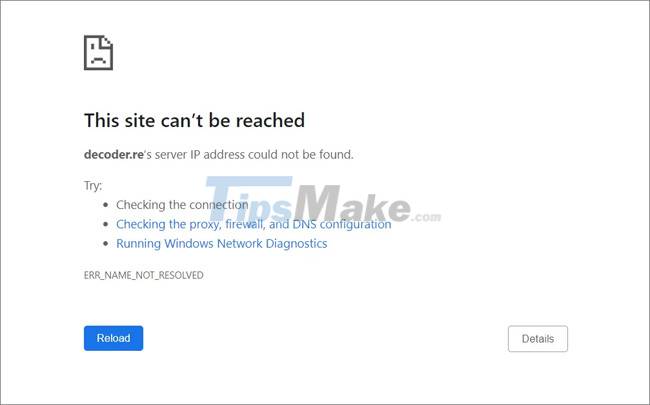 REvil ransomware gang sites mysteriously stop working ngừng Picture 2
REvil ransomware gang sites mysteriously stop working ngừng Picture 2
According to Recorded Future expert Alan Liska, REvil's websites went offline around 1am on July 13.
On the afternoon of the same day, a representative of the LockBit ransomware posted on the XSS hacking forum that the REvil gang deleted their server after learning that they had to appear in court.
"According to unverified information, REvil server infrastructure received a government legal request, forcing REvil to completely delete server infrastructure and disappear. However, that has not been confirmed. received", BleepingComputer quoted a post by a LockBit ransomware representative.
 REvil ransomware gang sites mysteriously stop working ngừng Picture 3
REvil ransomware gang sites mysteriously stop working ngừng Picture 3
Soon after, the XSS admin banned Unknown, the public representative of the REvil ransomware gang, from operating on the forum.
 REvil ransomware gang sites mysteriously stop working ngừng Picture 4
REvil ransomware gang sites mysteriously stop working ngừng Picture 4
Advanced Intel's Vitali Kremez explains: 'As a rule of thumb, administrators of forums would ban members from being active while under suspicion by the police.
On July 2, the REvil ransomware gang encrypted about 60 managed service providers (MSPs) and more than 1,500 small businesses using a zero-day vulnerability in the Kaseya VSA remote management software. .
As part of these attacks, REvil initially demanded a ransom of $70 million, but later reduced it to $50 million.
Since then, the REvil ransomware group has come under closer scrutiny by law enforcement.
Because these ransomware gangs often operate outside of Russia, President Biden negotiated with President Putin about the attacks and warned that, if Russia did not take action against them, the United States would automatically problem solving.
At this time, it is not clear whether REvil's servers are down for technical reasons or the impact of Russian or US law enforcement agencies.
Other ransomware groups, such as Darkside and Babuk, voluntarily ceased operations due to legal pressure.
However, when ransomware groups close down, they often renew their money to continue the attack. This has happened in the past when GandCrab closed and many members of the group reactivated under the name REvil.
Babuk also reactivated as Babuk v2.0 after the group disbanded due to differences in the way attacks were carried out.
The FBI declined to comment on the incident.
You should read it
- 7 kinds of ransomware you didn't expect
- Another large Data Center service provider became a victim of ransomware
- This is the world's fastest ransomware, encrypting 53GB of data in just over 4 minutes
- List of the 3 most dangerous and scary Ransomware viruses
- 5 gangs that create the world's most dangerous ransomware
- Matrix Ransomware is back under the distribution of RIG Exploit Kit
- Ransomware can encrypt cloud data
- General guidelines for decoding ransomware
- What is Ransomware Task Force (RTF)?
- [Infographic] 7 effective ways to protect businesses from Ransomware
- How to decode ransomware InsaneCrypt (Everbe 1.0)
- Why is Ransomware the perfect hack?
May be interested

Google is about to launch Drive for desktop, Backup and Sync feature stops working from 1/10

Microsoft Teams adds a meeting lock feature, late people can't access it

Microsoft released a set of Nostalgic wallpaper images, reminiscent of iconic Windows images

5 gangs that create the world's most dangerous ransomware

Figured out how to take over iCloud, but Apple's behavior made this hacker depressed and gave up the whole 18,000 USD in bounty

Detected 172 fake Android apps used to mine coins





 STOP - Ransomware is the most active in the Internet but rarely talked about
STOP - Ransomware is the most active in the Internet but rarely talked about Another large Data Center service provider became a victim of ransomware
Another large Data Center service provider became a victim of ransomware GandCrab blackmail extinguished after earning $ 2.5 billion worldwide
GandCrab blackmail extinguished after earning $ 2.5 billion worldwide This is the world's fastest ransomware, encrypting 53GB of data in just over 4 minutes
This is the world's fastest ransomware, encrypting 53GB of data in just over 4 minutes 7 kinds of ransomware you didn't expect
7 kinds of ransomware you didn't expect The 'gang' behind the Sodinokibi malware began auctioning celebrity data on the dark web
The 'gang' behind the Sodinokibi malware began auctioning celebrity data on the dark web