Warning: A new code of virtual money training is spreading strongly in Vietnam
From mid-January 2018 up to now, the monitoring system CyRadar - a startup created and developed by FPT has discovered SMB protocol packets continuously sent back and forth between computers in the network of many businesses. , organization. In just a few hours, hundreds of businesses' computers were infected with malicious code.
CyRadar experts said that SMB packets sent internally between the main computers exploiting Windows' MS17-010 vulnerability, also known as EternalBlue, were developed by the National Security Agency (National Security Agency). revealed in 4/2017.
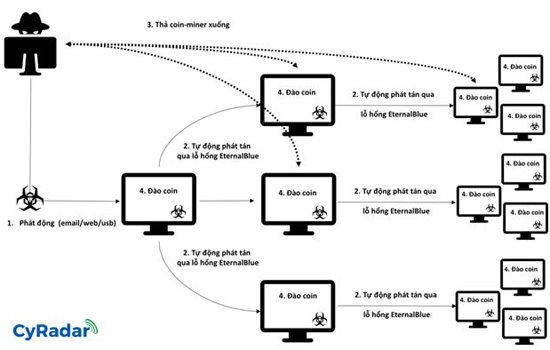
How to spread the malicious code.
When a computer on the network is infected, the malicious code will automatically scan for IPs in the same local area network (LAN). Later, it will use the EternalBlue exploit code to spread through port 445 of computers that exist vulnerabilities. If infected new machines connect to another network, the spread continues and extends.
This new malware not only has the ability to maintain connectivity to the control server, is ready to receive commands, download files, as a normal backdoor, but also can perform virtual money digging for hackers. The money that it exploits is Monero.
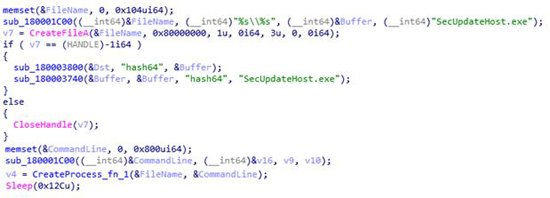 SecUpdateHost.exe file is actually a 'coin miner'.
SecUpdateHost.exe file is actually a 'coin miner'.
CyRadar detected the parameter passed to the miner file at runtime:

CyRadar experts conducted virus analysis, the results show that the domain name used for this malicious code is:
- ccc.njaavfxcgk3.club, registered on November 17, 2017, and started pointing to a server (IP 45.32.127.108) from 08/01/2018.
- "phimhayhdviet1.us" and "phimhayhdviet2.us", registered at the end of 2017, and pointed to server 45.32.127.108 at the beginning of 2018.
When checking on this server, experts discovered port 36215 for this version of the virus to download the file that was closed, but there are some other 'strange' ports open (48882, 48883):
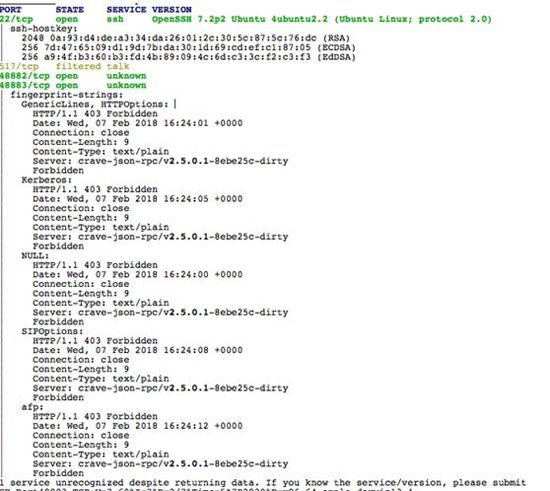
Although these domains are like a website, the server it points to does not open any regular ports for the website (80 and 443). Therefore, CyRadar believes that all three domain names are created by one person or group of Vietnamese speakers. There is currently no malicious code that connects to "phimhayhdviet" domains, but it is likely that hackers will use it in another attack.
What do users need to do to protect themselves against malicious attacks?
- Users need to regularly update the patches for the operating system and the software running on it.
- Equipped with antivirus software of reputable firms.
- Organizations and businesses need to equip the network monitoring system, can perform additional network isolation steps between the computers in the network together, to avoid the possibility of internal spread.
See more:
- Campaign to distribute spyware aimed at macOS in Vietnam
- New malware detection has terrible spy capabilities never seen on Android
- Acronis Ransomware Protection, a completely free anti-ransomware solution for Windows
You should read it
- ★ Warning: New variants of malicious code digging on Facebook threaten users in Vietnam
- ★ Smartphone can also be exploited by hackers to dig virtual money illegally
- ★ After WannaCry, Petya's 'extortion' malicious code is raging, this is a remedy to prevent
- ★ The Chrome gadget secretly exploits virtual money, making it slow
- ★ What to do when the computer is infected with a virus that fights virtual money?