Ham hacked the game, the boy made the computer infected with virtual money and ruined it
The boy entered the middle school last year and was given a laptop by his mother to serve his studies. It is an old HP Elitebook 8470p with Core i5-3320M chip, 8GB of RAM, 128GB SSD, quite stable configuration to perform office and study tasks. Elitebook is HP's most advanced model and has a high durability.
But only a year later, the device was broken.
When checked, the device is in a pretty bad situation. On the case, there are patchy, painted spots, Space Bar is warped.
When opening the radiator fan, a large dust block, blocking the radiator slot of the machine. Although when buying the HP Elitebook 8470p was an old machine but at that time, the cleaning staff cleaned it carefully.


The battery of this machine is broken because the charger IC is burnt, unplugged, the device is also "stuck".
What happened?
In fact, the boy not only uses computers to study but also to work on games. When checking the antivirus history of Microsoft Security Essentials, there was an appearance of a virtual money digger called Trojan: Win32 / CoinMiner! Bit in the folder of the game hack tool.

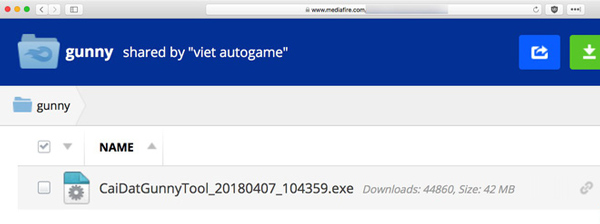
And obviously, the cause of the computer being infected with malicious code is intentional. The executable file of the malicious code named qc64.exe - 'promotional item' is attached to the hack of Gunny game. This is a famous virtual money code and on YouTube there is a video about it.
So probably the main reason why the HP Elitebook 8470p is broken is because of overworked work because it has to dig virtual money illegally, pushing the CPU to 100% for a long time.
In theory, it is very unlikely that software can damage hardware except for the CIH virus that occurred 20 years ago. However, with the explosion of virtual money, the possibility of this risk is very large.
The latest version of the hack tool has nearly 45,000 downloads on its website. This means that only the malicious code inside this hack game tool has tens of thousands of machines that have been infected with malicious code and are "plowing" at full capacity.
Digging a coin for a long time will cause serious degradation of computers, especially for those with simple heat sinks and discrete GPUs. In the past, there have been cases of malicious smartphone plague the coin for a long time, and the battery is so bulky that it is about to explode.
To illegally dig virtual money on a user's computer, hackers not only use the form of direct infection into the system, but also some websites that insert code to dig on the browser. With such sophisticated forms, even if a user's computer is 'clean', the virus will become a victim of malicious code when accessing such websites.
In short to protect and enhance the life of your laptop, you should pay attention:
- Do not hack in the game because it is possible that the hack tool comes with malicious code.
- During use, pay attention to monitor the temperature to avoid overheating.
- Regularly clean the machine.
- Do not carry out overload operations on your laptop. Such as heavy gaming on an office laptop .
- Use antivirus software.
- Prevent malicious code on web browsers by installing ad blocking software like uBlock Origin.
See more:
- Smartphone can also be exploited by hackers to dig virtual money illegally
- What to do when the computer is infected with a virus that fights virtual money?
- List of some types of files that are potentially dangerous on Windows
You should read it
- ★ VNCERT issued an emergency alert warning malicious code exploiting Coinhive virtual money
- ★ What to do when the computer is infected with a virus that fights virtual money?
- ★ Warning: a new variant of the virus that fills virtual money via Facebook Messenger will appear every 10 minutes
- ★ Warning: new code of virtual money digging is available via Facebook Messenger
- ★ Warning: New variants of malicious code digging on Facebook threaten users in Vietnam