Security experts found a way to break iPhone passwords on all versions without worrying about locking or deleting data
Matthew Hickey, a security researcher at Hacker House, recently figured out a way for brute force attacks to unlock any iPhone or iPad device, despite being updated to the latest iOS version. Hickey's discovery made Apple once again have to review security technology on its iPhone and iOS devices.
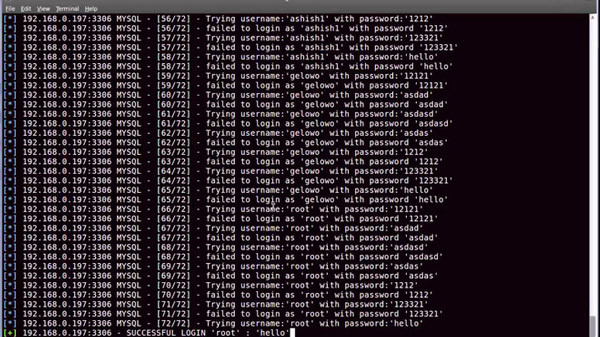
Brute force is a technique to try to guess a user's password. Hackers use the list of the most popular usernames and passwords in the world to constantly send queries to the user's wp-login.php file until they log in.
Starting from iOS 8, all iPhone and iPad devices are equipped with advanced encryption security technology with a 4 or 6 digit password. The close connection between hardware and software makes it impossible to break these devices. In addition, the device also allows users to set the mode to manually clear all data in the device if the wrong password is entered too many times, making brute force harmless.
On the new generation devices of Apple is equipped with a closed processor integrated right on the hardware of the machine. This security system is called Secure Enclave, which has a secure bootloader and its own software update mechanism that can 'count' the wrong number of user passwords. After each wrong entry, it reduces the speed of the device's response until it receives the correct password.
 Secure Enclave security system first appeared on Apple's A7 processor.
Secure Enclave security system first appeared on Apple's A7 processor.
But Hickey with an iPhone turned on but the screen lock and a Lightning cable figured out how to bypass the 10-time password entry limit on almost every iOS version to be able to run brute force comfortably, even above New versions like iOS 11.3.
Hickey said that when the iPhone or iPad is connected to Lightning and receives an input signal from an external peripheral (in this case a keyboard), an intervention request should be prioritized to handle immediately. will be activated. This means, if you do not break down the password to enter it multiple times and enter a long multi-digit string, the iPhone will process the entire sequence but only count as a single entry. This entry is equivalent to hundreds of single entries. This way, hackers can freely conduct brute force.
For example, all passwords listed from 0000 to 9999 will be hacked by hackers to create continuity during the operation of the software and then iPhone will process the entire range from 0000 to 9999 before the software tells the user that the password was entered incorrectly if the password is not in the above sequence.
With Hickey's attack method, hackers can only enter more than 100 passwords of 4 digits per hour and for 6-digit passwords, it will take longer.
Hickey has sent an email informing its findings to Apple, but the technology company has yet to give a formal response to the issue.
Earlier, Apple had to launch a new feature called USB Restricted Mode in the new version of iOS 12 to disable the iPhone unlocking tool called Grayshift's GrayKey.
See more:
- This is how this guy controls the iPhone with his eyes, not one touch
- Check iOS 12 beta and iOS 11.4 on iPhone 5S to iPhone 8, should upgrade?
- How to check the safety cable for your iPhone
You should read it
- ★ The former Apple engineer claims to be able to unlock all iPhones for $ 15,000
- ★ 6 ways to unlock iPhone without password
- ★ US police scramble to buy tools to unlock all iPhones despite the price of up to $ 30,000
- ★ Instructions to fix iPad errors are disabled
- ★ How to unlock iPhone when forgot password