Popular IT terms in English
In today's society, information technology has become popular as "breath" but having English terms will make it difficult for you to use it. Here, we would like to synthesize the most commonly used terms in the field of information technology for your reference.
FTP: An acronym for File Transfer Protocol . This is a file transfer protocol on the network based on TCP standard, often used to upload files to Host, Server with default port of 21
Traceroute: A program that allows you to determine the path of packets from your computer to the target system on the Internet.
ICMP: Abbreviation for Internet Control Message Protocol . This is the protocol for handling status messages for IP. ICMP is used to report errors that occur during the transmission of data packets on the network. ICMP belongs to the Transport Layer .
Telnet: ( short for TErminaL NETwork ) is a network protocol ( network protocol ) used on connections to the Internet or connections at the local LAN computer network.
DNS: An acronym for Domain Name System . A DNS server waits for a connection at port number 53, which means that if you want to connect to that server, you must connect to port number 53. The DNS server transfers the hostname with letters into the corresponding digits and vice versa.
For example: 127.0.0.1 -> localhost and localhost ---> 127.0.0.1 (127.0.0.1 is the address of the device you are using, or "loopback" address)
SMTP: An acronym for Simple Message Transfer Protocol . The SMTP protocol is used to send mail through a Sendmail program ( Sendmail Deamon ), though popular but less secure.
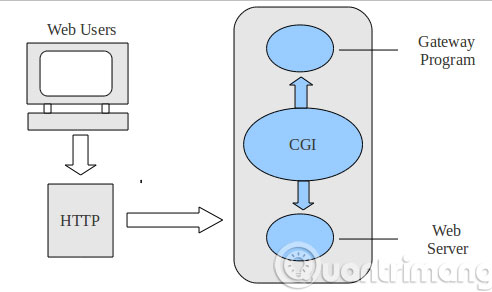
CGI: An acronym for Common Gateway Interface , which allows to initiate communication between the server and the program thanks to the information specification format. CGI programming allows you to write a program that starts commands from the website, the website uses HTML format to create the program. CGI program runs under single environment variable. When the WWW initializes the CGI program, it creates some special information for the program and responds back from the CGI program. Then, the server determines the type of file the program needs to execute. In general, CGI programming is to write programs that receive and transmit data over the Internet to the WWW server. The CGI program uses that data and sends the HTML response back to the client
Shell: A program between users and the Linux kernel. Each given command will be interpreted by the Shell and then transferred to the Linux kernel. In simple terms, Shell is the command language interpreter, in addition to making full use of the utilities and application programs available on the system.
NetBios: Is a protocol, networking technology of Windows 9.x. It is designed in a LAN environment to share resources ( such as sharing files, folders, printers and many other resources . ). This model is very similar to the peer network 2P model. Usually a network uses the Netbios protocol usually Netbios Datagram Service (Port 138), Netbios Session Service (Port 139) or both.
SYN: An acronym for The Synchronous Idle Character ( temporary translation ). The SYN execution process will take place as follows:
First, A will send B to ask for a connection and wait for B to reply. After B receives this request, it will reply A to "received a request from A" (ACK) and "a reply request to complete the connection" (SYN). At this point, if A replies "SYN" again, the connection will be initiated.
Cookies: Small structured pieces of data shared between the website and the user's browser that have been encrypted by that website. Cookies are stored under small data files in text format ( with a capacity of less than 4k ). They are created by sites to store / track / identify information about users who have visited the site and the areas they visited in the site. This information may include user name / user ID, password, preferences, habits .
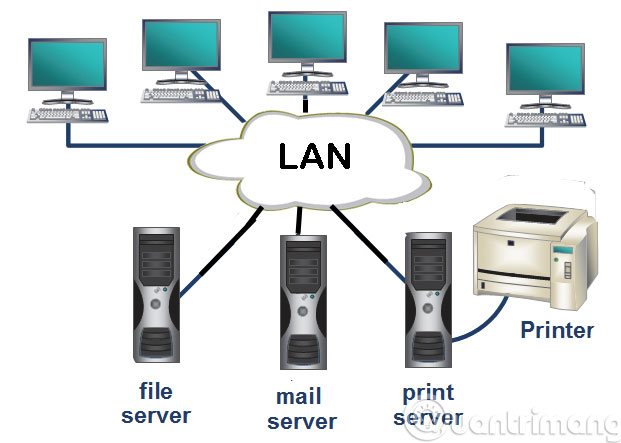
LAN: An acronym for Local Area Network . A system of computers and peripherals is linked.

Local network users can share data on hard disk, network and printer sharing.
Vulnerability: A region, vulnerable point in the system according to a discovered requirement, a feature or a standard, or an unprotected area in the entire security structure of the system to re-enable the system of points to be vulnerable or affected by other problems. Hackers often exploit vulnerability to attack the system.
Anonymous: Anonymous, anonymous
IIS: An abbreviation for Internet Information Server . This is a famous Microsoft WebServer program.
Account: The account is a combination of two username elements ( username ) and password ( password ) provided by a service to you when you have registered with them to secure you.
Source Code: Source code ( of a file or program )
Port: Port
Compile: Compile
Login: Login
Database: Database
ISP: The abbreviation for Internet Service Provider .
TCP / IP: The abbreviation for Transmission Control Protocol and Internet Protocol . TCP / IP packet is a block of data that has been compressed, then attach a header and send it to another computer. The header in a packet contains the IP address of the sender.
Whois: A very useful program, which helps you find out information about who hosts, networks and administrators of that site ( Address, Email, IP . )
Security: Security
NAV: The acronym for Symantec's Norton Anti-Virus program. This is a very popular and popular Virus scanning program.
UDP: An abbreviation for User Datagram Protocol, it has the same task as TCP but it does not guarantee the accuracy of the information conveyed. UDP is simply a packet with a starting point and a specified destination
Domain Is the domain name of a certain website Example: https://quantrimang.com
OS: Abbreviation for Operation System - Operating System
IRC: The abbreviation of Internet Relay Chat . This is a standalone program where you can participate in chat channels.
mIRC: As a chat client, Khaled Mardam-Bey wrote. It can be said that mIRC was the first chat software and then a series of other products from Yahoo, AOL (ICQ, AIM) . were born.
IPC: stands for Inter-Process Communication . Used in data sharing between applications and computers on the network (NT / 2K). When a machine is booted and logged into the network, hdh will create an implicit share named IPC $. It will make it possible for other machines to see and connect to shares on this machine
Encryption: Encryption
Decryption: Decode
Remote Access: Remote access via network
GNU Debugger: The gcc compiler and gdb debugger
SSI: Abbreviation for Server Side Includes . These are the instructions placed in html files. The server will be responsible for analyzing these instructions and will pass the results to the client.
ActiveX: Is a standard system used to build components in a Windows environment. These components are not only able to operate independently but can also be exploited by other components. These are components that are written in many different languages and are very diverse, maybe ActiveX controls for embedding into other programs from the design of the program, possibly ActiveX DLLs ( Dynamic link library ) that other programs refer to.
Packet: Packet data
Server: Server
Client: Client , used to connect to the server (Server)
Info: The abbreviation for "Information", ie information
Firewall: A firewall is a barrier between a local network (local network) and another network (such as the Internet), controlling the traffic between these two networks. If there is no firewall, the traffic to the internal network will not be subject to any regulation, and once the firewall is built, the traffic will be set by the settings on the firewall.
PPP: The abbreviation for Point-to-Point . This is a reliable Internet connection protocol through Modem
Serial Direct Cable Connection: A technology that connects a computer with a cable that transmits data
Ethernet: A powerful networking technology that is used mostly in LANs. This network uses CSMA / CD (carrier sense media access / collision detection).
Pwdump: An abbreviation for Password Dumper . This is a great tool that is indispensable when Hack into WinNT system
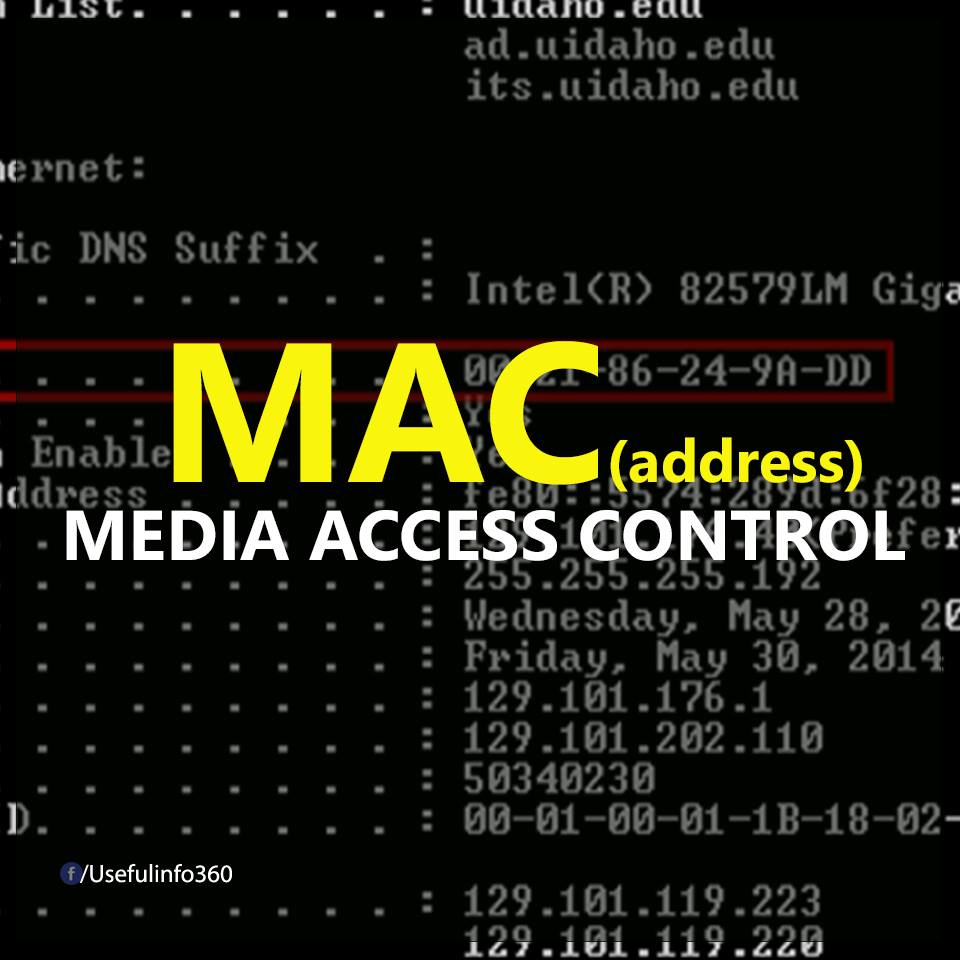
MAC: The abbreviation of Media Access Control means environment access control, is a sub-layer of data transfer protocol - part of the data link layer in the 7-tier OSI model.
OSI: An acronym for Open System Interconnection or OSI standard model. So what is the OSI model?
In the past, communication between computers from different vendors was difficult, because they used different data protocols and formats. Therefore, the International Organization for Standardization (ISO) has developed a communication architecture known as Open System Interconnection (OSI), a model that defines standards. link computers from different providers.
ATM: An acronym for Asynchronous Transfer Mode . This is a connection-oriented network technique that uses small cells with the lowest fixed size. ATM has the advantage of supporting voice and video data
EGP: An acronym for Exterior Gateway Protocol . This is a term that applies to which protocol is used by the router in an autonomous system to notify the ability to go to the network for routers in other autonomous systems.
DHCP: The abbreviation for Dynamic Host Configuration Protocol . This is a protocol that the computer uses to get all the necessary configuration information, including the IP address
OWA: An abbreviation for Outlock Web Access . This is the Microsoft Exchange Server Module ( a Server for Mail ), which allows users to access and administer their Mailbox remotely via Web Browser.
URL: The abbreviation for Uniform Resource Locator , used to refer to resources on the Internet. The power of the web is the ability to create hypertext links to relevant information. These information are other websites, images, sounds . These links are often represented by underlined blue letters called anchors. URLs can be accessed via a browser (Browser) like IE or Netscape.

WWW: The abbreviation for the World Wide Web

HTML: An abbreviation for Hyper Text Markup Language , which is hypertext language. This is a language used to create web pages, containing text pages and formatting tags that tell the web browser how to translate and render web pages on the screen.

Web page is a plain text page (text only), but semantically, there are 2 contents:
- Specific text paragraphs.
- Tags (text fields are written according to rules) describe a certain behavior, usually a link (hyperlink) to another site.
SMB: The abbreviation of Server Message Block . This is one of the popular protocols for PC, allowing you to use share files, disks, directories, printers and in some directions both COM port
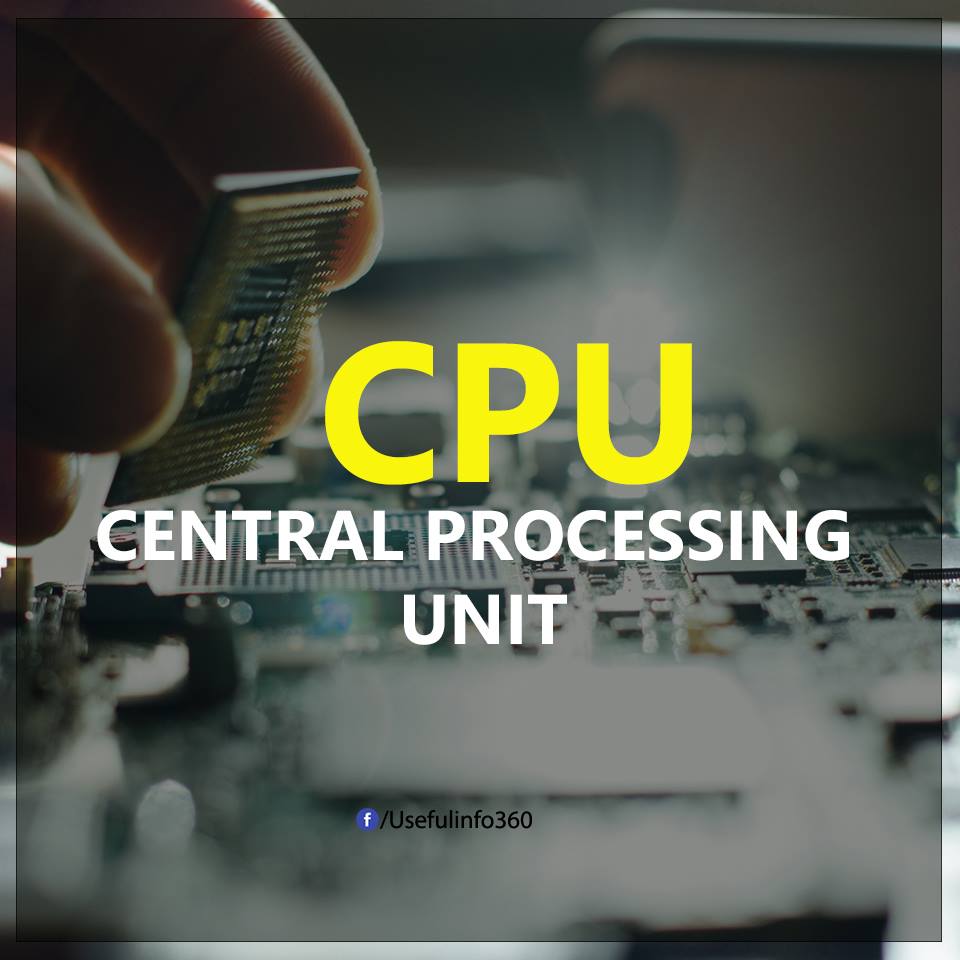
CPU: stands for Central Processing Unit . This is a collection of multiple circuits used to control all major operations of the machine.
GPU stands for Graphics Processing Unit, the graphics processor takes on the task of speeding up and processing graphics-related tasks for the CPU.

CAPTCHA: Completely Automated Public Turing Test To Tell Computers And Humans Apart - Fully automated public Turing test to distinguish people from computers.

Cc / Bcc: Carbon copy / Blind Carbon copy, is to create a copy / create a temporary copy. Cc / Bcc is used a lot when sending letters to many people. In which Cc is sending letters to many people at the same time and those who see each other's email addresses, Bcc is also sending emails simultaneously to many people, but not letting them see each other's email addresses.

CCTV: Closed Circuit Television, temporarily translated as Closed Circuit Television, CCTV uses a camcorder to record and transmit signals to a desired device.

DSL: Digital Subscriber Line, temporarily translate Digital subscriber channel. Readers can read more about DSL in the article: Summary of DSL technology.

DVD: Digital Video Disk is a digital video disc, DVD is a popular optical disc, which allows to store videos and data quite conveniently.

GPS: Global Positioning System is Global Positioning System. Please read How does GPS global positioning system work?

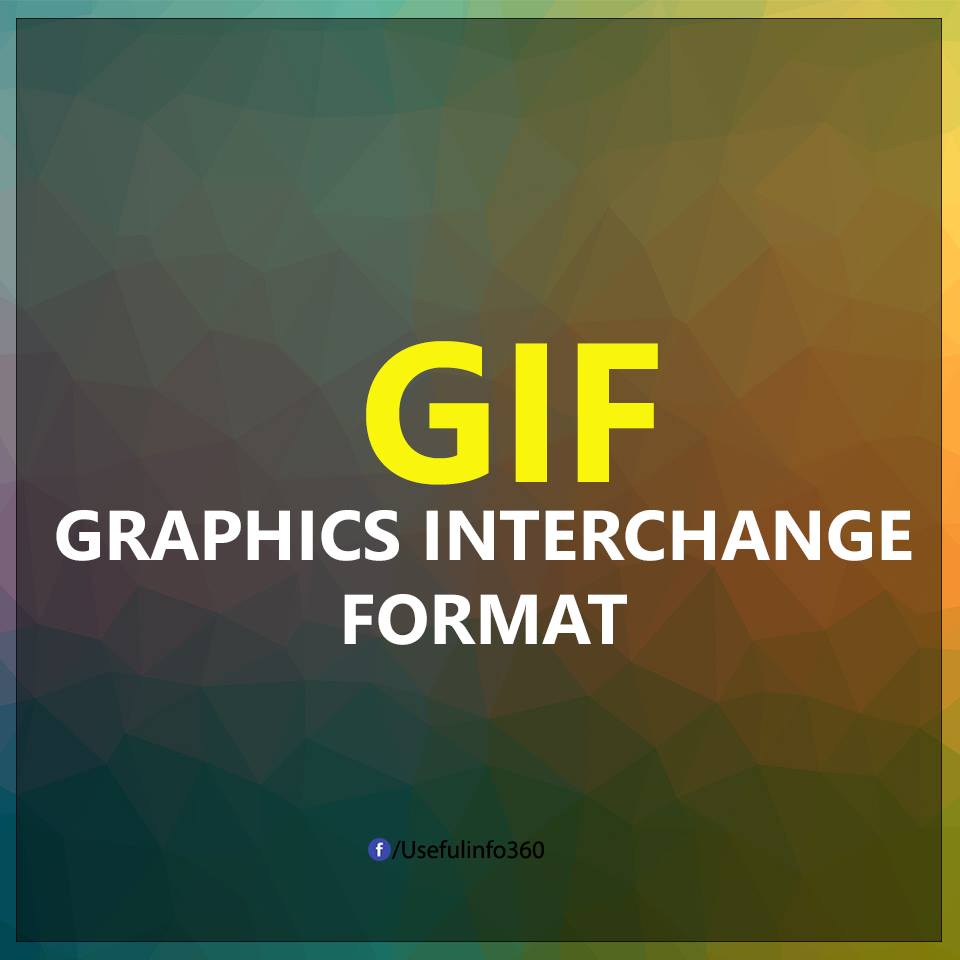
GIF: Graphics Interchange Format is an image exchange format, a popular bitmap image format, used for images with less than 256 colors and animation with less than 256 colors on each frame.
PNG: Portable Network Graphic, roughly translated as Dynamic Network Graphics, it is an image format that uses a new, no-quality, data compression method that was developed to improve GIF.

JPEG: Joint Photographic Experts Group, is an image format that uses data compression to alter the original image quality.

MPEG: The Moving Picture Experts Group is an international standard for video encoding and compression.

PDF: Portable Document Format. Please read the details in: What is a PDF file? How to read PDF file?

HDMI: High-Definition Multimedia Interface, details of this term can be read at: Difference between HDMI and DVI.

HTTP: Hypertext Transfer Protocol, is Hypertext Transfer Protocol.

I / O: Input / Output stands.
IP: Internet Protocol - Internet Protocol.

ISP: Internet Service Provider - Internet service provider.

LCD: Liquid Crystal Display - Liquid crystal display

LTE: Long Term Evolution - Long-term evolution, you can meet it in 4G LTE: Is 4G and 4G LTE the same?

SD Card: Secured Digital Card, is a type of removable memory, mainly used for storing data on the phone.

SMS: Short Message Service, roughly translated: Short message service, a telecommunications protocol that allows sending messages in short text format.

SQL: Structured Query Language, structured query language, is often used to manage data in a relational database management system.

SSL: Secure Sockets Layer. Please read in detail: What is SSL? Is SSL important to the website?

VPN: Virtual Private Network, is Virtual Private Network. If you want to learn more, read this article: VPN theory - What is a virtual private network?

POP3: An abbreviation for Post Office Protocol Version 3 . The POP3 daemon is usually run at port 110 ( this is its standard port ). To check mail, you must connect to the server running POP3 daemon on port 110
TFTP: The abbreviation for Trial File Transfer Protocol . TFTP runs on port 69 and uses UDP protocol so it is very insecure
RIP: Short for Routing Information Protocol , running on port 512
HyperTerminal: A program that allows you to open a server on any port of your computer and allow listening to input from specific computers.
You want to set it up: Start > Programs > Accessories > Communications . Then choose HyperTerminal
DES: Abbreviation for Data Encrypt Standar . This is one of the common password encryption standards, very difficult to crack, only one way and also the easiest to use dictionary
WU-FTP: stands for Washington University - File Transfer Protocol . This is a FTP server software that is used quite commonly on Unix & Linux systems. This program used to be quite a serious error, which is the execution of the globbing file on a vulnerable Server that allows hackers to execute code on the remote server (of course the code is harmful ). leads to overwriting files on the server and eventually leads to a system crash "
NIS: stands for Network Information Server .
GUI: stands for Graphic User Interface . This is the graphical user interface in the Linux operating system
Global: This command line utility will display the Global Group members on the specified server or domain.
Local: Like Global but it displays members of Local Group. For example, we want to query the Administrator Group list.
SOCKS: SOCKS is created by the word SOCKetS and is developed primarily by NEC, as well as being put into an Internet standard by the ITEF, defined in RFC (Request for comment). SOCKS's mission is to mediate between a SOCKS server end and the other end of the SOCKS server:
CLIENT --------> IN - SOCKS SERVER - OUT ---------------> SERVER
SOCK is mainly used in Proxy server and Firewall technology. Currently there is version SOCKS4 and SOCKS5. Socks 5 is the following development version so it has the ability to authorize, and can use UDP ( SOCKS 4 only with TCP ).
SQL Injection: Once a popular attack on websites. By inserting SQL query / command code into input before passing it to a processing web application, an attacker can log in without a username and password, remote execution, dump data and retrieve the root of SQL server. An attack tool is any web browser that can use Internet Explorer, Netscape, Lynx, .
DoS: The abbreviation for Denial of Service . This is a method commonly used by hackers to attack a website when other attack methods prove ineffective. The characteristics of DoS are to consume some of the resources on the server, taking up bandwidth, memory, CPU, hard disk . making the server unable to meet incoming requests. The end result will cause the server to be numb or to restart.
Exploit: Exploiting (an error)
Fake IP: fake IP
Crack Password: Break the password
Debug: The program that comes with DOS. This is a great tool for debugging programs, cracking software, reading hidden memory like boot sector and more . To debug the program, you need to have knowledge of Assembly.
TCP Port Scanning: The most basic form of Scanner programs. This type of program will try to open a TCP connection to a Port to determine the status of this Port
Web spoofing: A form of attack that allows someone to view and edit any web page sent to the victim's computer. They can track all information filled out by the victim. This is especially dangerous for personal information such as addresses, credit card numbers, bank account numbers, passwords to access that account . Web spoofing works on both IE and Netscape. It works based on the SSL protocol being used as a certificate for authentic Web sites. This type of attack can be done using Javascript and Web server plug-ins
Footprinting: Footprinting method is to collect all important information about your goals such as: Email, IP, Domain . This is the first basic step of a hacker before hacking into a certain system.
XSS: Short for Cross site scripting . This is a term that refers to how websites use certain ways to steal user information ( for example, cookies ). Hackers will lure victims to their site by including an attractive hyperlink. Of course good hackers often encrypt their hyperlinks to minimize suspicion. After the victim's data is stolen, it will be sent to the hacker and given a website with content suitable for fake hyperlink
Race Conditions: Race Conditions are one of the most common attacks on Unix / Linux systems. Race Conditions occur when certain programs or processes perform an inspection. Between the time that an inspection is performed and the operation is performed, the result of that test may reflect the state of the system. Hackers will take advantage of this program or process while it performs privileges
Overflow Buffer: Buffer overflow error. This is one of the most classic Hacking techniques
Nuke: It is one of the quite powerful techniques. If you know the IP of any connected computer, then nuke can completely disconnect the computer, even if it's a LAN
Sniffer: A program that lets you grab all data packets that are transferring your network card. Such data can be username, password, some other important information, .
Log: Is the operation to record the process of using your service. When entering a computer or server, log deletion is indispensable. Because, if you don't delete the log, then you can find your real IP
Trojan: An illegal program that is contained within a legitimate program. This illegal program performs secret functions that users don't know or need. Trojans have many types but are still mainly two main types:
- The Trojan retrieves the password and sends the password obtained via email (eg, Kuang2, Hooker, barok .)
- Trojan used for remote control (eg Sub Seven 7, Back Orifice 2000 .)
Port surfing: Connects to the ports of a server to collect information, such as time, operating system, running services, .
Finger: This is a very useful program, which helps you gather lots of information about users ( often disabled ).
Nmap: An abbreviation for Network exploration tool and security scanner. This is the leading scanning program with extremely fast and extremely fast speed. It can scan on a wide area network and is especially good for single networks. NMAP helps you see what services are running on the server ( services / ports: webserver, ftpserver, pop3, . ), what operating system the server is using, what type of firewall the server uses, . and a lot other function. In general, NMAP supports most scanning techniques such as ICMP (ping aweep), IP protocol, Null scan, TCP SYN (half open), . NMAP is considered as a leading tool for hackers as well as other users. Network administrator in the world.
Netcat: An indispensable tool for hackers who want to attack websites and servers. This program reads and writes data over the network via TCP or UDP protocol. The attacker can use Netcat directly or use other programs and scripts to control Netcat. Netcat is considered a exploitation tool because it can create links between attackers and servers for reading and writing data.
Get Admin: As a privilege escalator , also called Escalation of priority . This is considered one of the important steps when hackers break into systems. Suppose hackers capture the rights and log into the Win NT system. But hackers get no equivalent rights as the Administrators group but belong to the lower right group. So hackers do not have the right to do many things like Admin. Therefore, hackers must implement Get Admin to gain higher rights to control the system.
Netwatch: A tool to display shared resources on the network you want to hack
Usestat: This command line utility can display User, Full name, date and time of login for each user on each specified domain.
FootPrinting: The way that hackers do when they want to get the maximum amount of information about the server / business / user. It includes details about IP addresses, Whois, DNS . roughly all the official information related to the target. Sometimes hackers just need to use search engines online to find that information
Enumeration: A search for poorly protected resources or user accounts that can be used to invade. It includes default passwords, default scripts and services. Many network administrators do not know or modify these values
Gaining Access: This is based on the information captured in the Enumeration step where the hacker attacks the buffer overflow, retrieves and decrypts the password file, or the most crude is brute force ( check all cases ) password. The tools commonly used in this step are NAT, podium, or Lopht
Escalating Privileges: A hacker seeking to control the entire system. Hackers will find the admin password, or use the vulnerability to escalate privileges in case they enter the network with the Guest account. The John and Riper are two very popular password crack programs
Pilfering: A hacker who uses search engines to use methods to access the network. Những file text chứa password hay các cơ chế không an toàn khác có thể là mồi ngon cho hacker.
Covering Tracks: Sau khi đã có những thông tin cần thiết, hacker tìm cách xoá dấu vết, xoá các file log của hệ điều hành làm cho người quản lý không nhận ra hệ thống đã bị xâm nhập hoặc có biết cũng không tìm ra kẻ xâm nhập là ai
PKC: Là chữ viết tắt của Public key cryptos . Có nghĩa là hệ thống mật mã sử dụng từ khóa chung
PHP: Là chữ viết tắt của PHP Hypertext Preprocessor , tạm dịch là ngôn ngữ tiền xử lí các siêu văn bản. Các mã lệnh PHP được nhúng vào các trang web, các trang này thường có phần mở rộng là .php, .php3, .php4 . Khi client gởi yêu cầu "cần tải các trang này về" đến web server, đầu tiên web server sẽ phân tích và thi hành các mã lệnh PHP được nhúng trong, sau đó trả về một trang web kết quả đã được xử lí cho client. PHP là một ngôn ngữ rất dễ dùng, dễ học và cực kì đơn giản hơn nhiều so với các ngôn ngữ khác như C, Perl. PHP hiện nay rất phổ biến tuy nhiên PHP scripts chẳng an toàn chút nào, các Hacker có thể lợi dụng khe hở này để attack các servers

PUB: Một PUB thông thường có chứa các file để cho mọi người download, một số PUB có thể cho upload. Tuy nhiên, một PUB có thể không chỉ chứa các file dùng cho việc download, mà có thể chứa cả một "TRANG WEB".
Local Exploit: Là khai thác cục bộ. Đây là một trong những phương pháp tấn công cao cấp của hacker
- Những điều bạn nên biết về giao thức HTTP/2
- 7 kỹ năng mềm cần có của một người làm CNTT
- Tìm hiểu về định dạng file: Khi nào thì dùng JPEG, GIF và PNG
Having fun!