Phishing emails are getting more sophisticated, can you spot them?
If you thought phishing emails were just poorly written messages asking you to help a distant prince move millions of dollars out of his country, you need to be wary of today's much more sophisticated scams.
3. "Hello, I'm a pervert" blackmail
This email scam has been around for years, but it continues to trick people; there are always questions about it on Reddit and similar sites. You receive an email that looks like it came from your own address. The email explains that the sender has installed a spyware program on your computer, giving them complete access to everything you do on your computer, including your contacts and webcam.
They then say they have a sensitive video of you watching porn online and threaten to send it to all your contacts if you don't send them cryptocurrency. The message includes threatening language that you only have 24 or 48 hours to send the money, and if you attempt to reset your device or report it to the police, they will make the video public immediately.
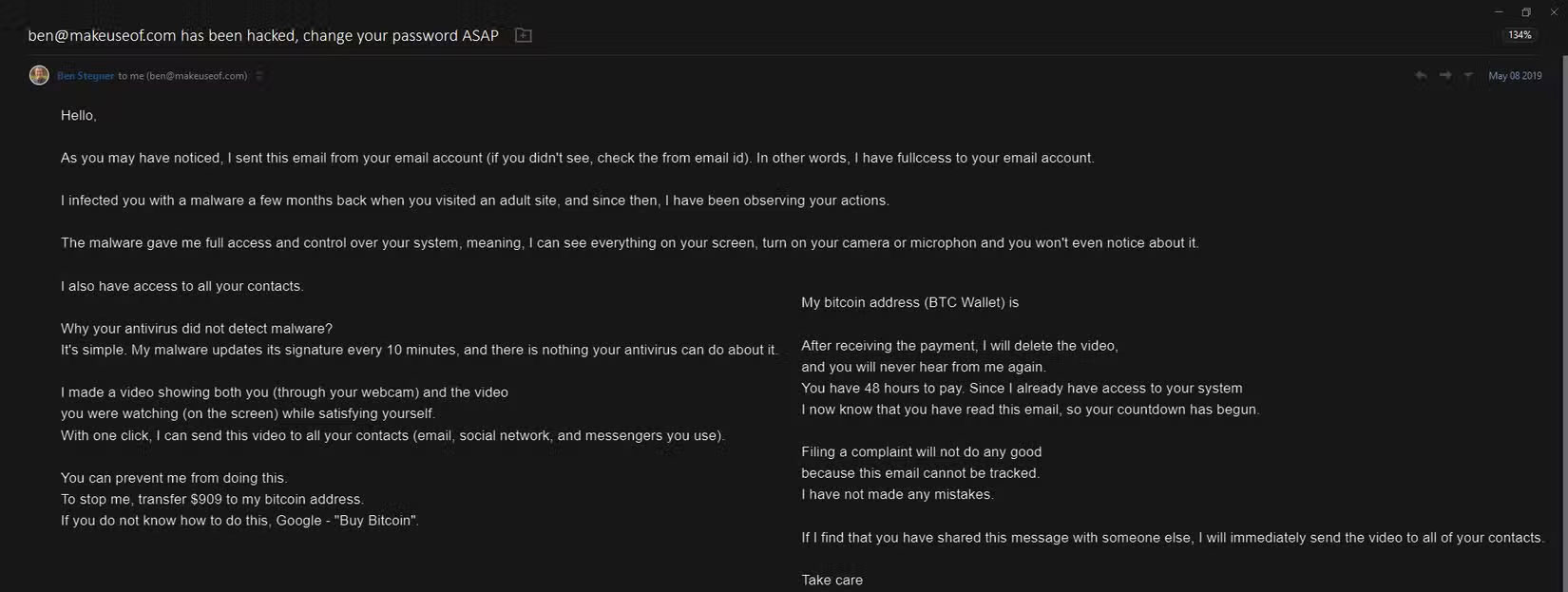
Over the years, this scam has evolved to sometimes include more personal information, making what the scammer says more believable. The message might contain your home address, a Google Maps photo of your house, or a password you've used in the past.
2. Fake shopping emails
Another common form of email scam designed to trick as many people as possible is a fake invoice. Sometimes it pretends to be from a computer security tool like Norton or McAfee. Earlier versions of this scam sometimes spoofed emails from Geek Squad, and they were styled after big retailers like Amazon to tell you that you had purchased a MacBook or other expensive item.
No matter who the fake sender is, the formula is the same: A bill for an expensive purchase you didn't make, along with a phone number to call if the purchase was "unauthorized." They hope most people will panic and call immediately to cancel the transaction, after which the phone number will lead you to the scammers.
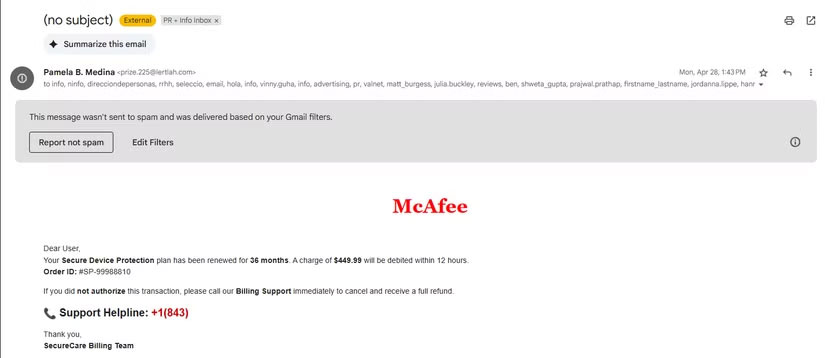
If you call them, they will try to trick you into giving them your credit card number, or more likely, it will look like a tech support scam. They will ask to connect to a computer and show you made-up 'problems' before asking for payment.
Look closely and you'll see telltale signs that these emails are fake. Even if the formatting and grammar are clean and correct (which phishing emails rarely are), they won't include details about the card you used to 'purchase' the item, the postal code for delivery, or anything like that. Almost every legitimate purchase receipt email will have this information.
1. AI enhances email fraud
AI's many capabilities allow scammers to create more sophisticated and more targeted email attacks — and AI can create them faster.
An example of this is the 'lost pet' scam, where scammers use contact information shared on 'lost pet' posters and listings to pretend they have someone's pet and extort money from them. With AI image generation becoming more and more impressive, if you have an email address on the list, scammers can take advantage of this. Using a reference photo from the listing, they can create an AI image of your pet, then perform the same scam by pretending they have found the animal.
AI image generation can also be used to create more realistic fake images for romance scams, celebrity impersonations ( which often target the elderly ), or even to impersonate your friends. Never trust anything sent to you randomly; always contact the person through a known method to verify.